Static and dynamic analysis technology-based host system security evaluation method
A host system, static security technology, applied in computer security devices, transmission systems, digital transmission systems, etc., can solve the problems of difficult to find logical security risks, time-consuming and laborious, and achieve the effect of more comprehensive analysis results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
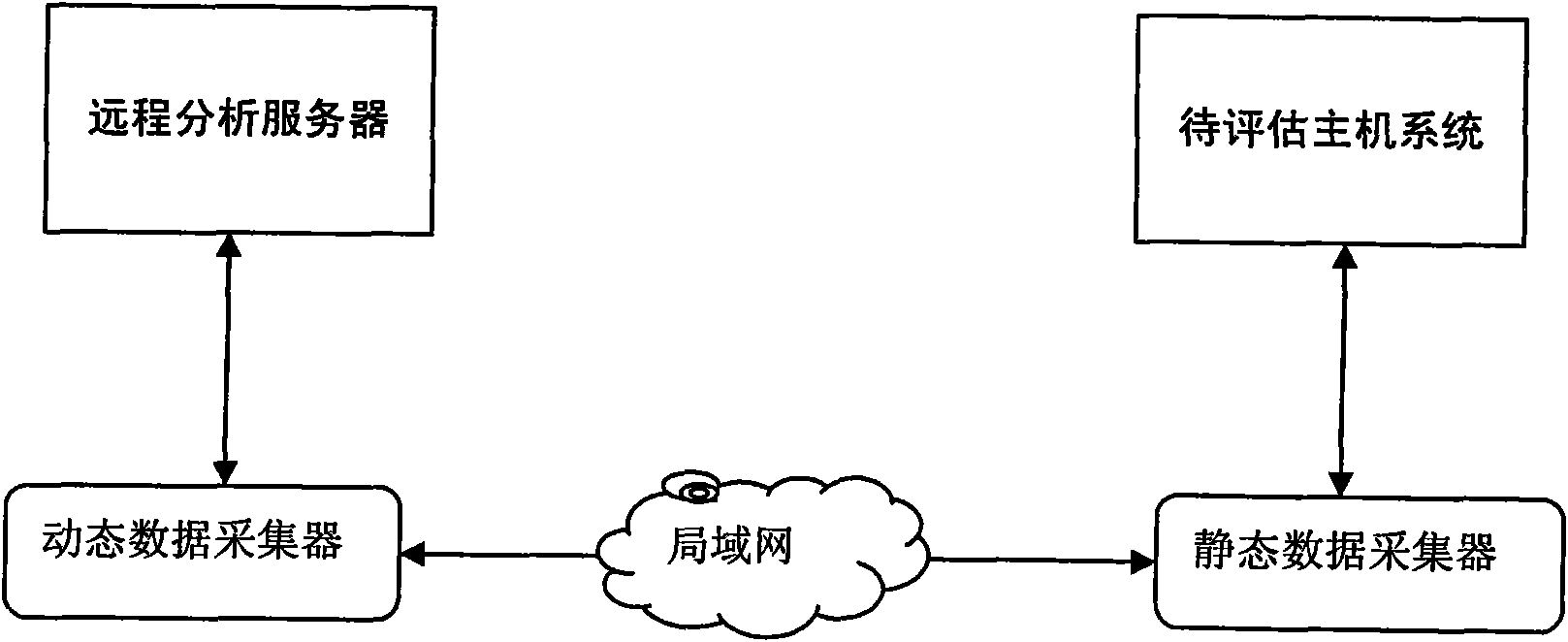
[0046] The present invention will be further described below in conjunction with accompanying drawing.
[0047] This method collects static security data such as host system profile parameters, service lists, and process information by uploading a static data collector. , and dynamically analyze the service response, vulnerability matching, and in-depth logical security of the host system. The data to be analyzed includes the following:
[0048] 1) Operating system language, version, IP address and other basic information, account information, network configuration, sharing, services, permission information of key files, patch and vulnerability information;
[0049] 2) Detailed version of database system, listener service security, account password security, initialization parameter setting security, account password policy, permission setting of stored procedure, startup account permission, non-essential service, log audit strategy and authentication mode and table usage of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com