Method for carrying out harmful content recognition on network text and short message service
A network text and mobile phone technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as innocent shielding of normal content, misunderstanding of the author's meaning, and inability to update in time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
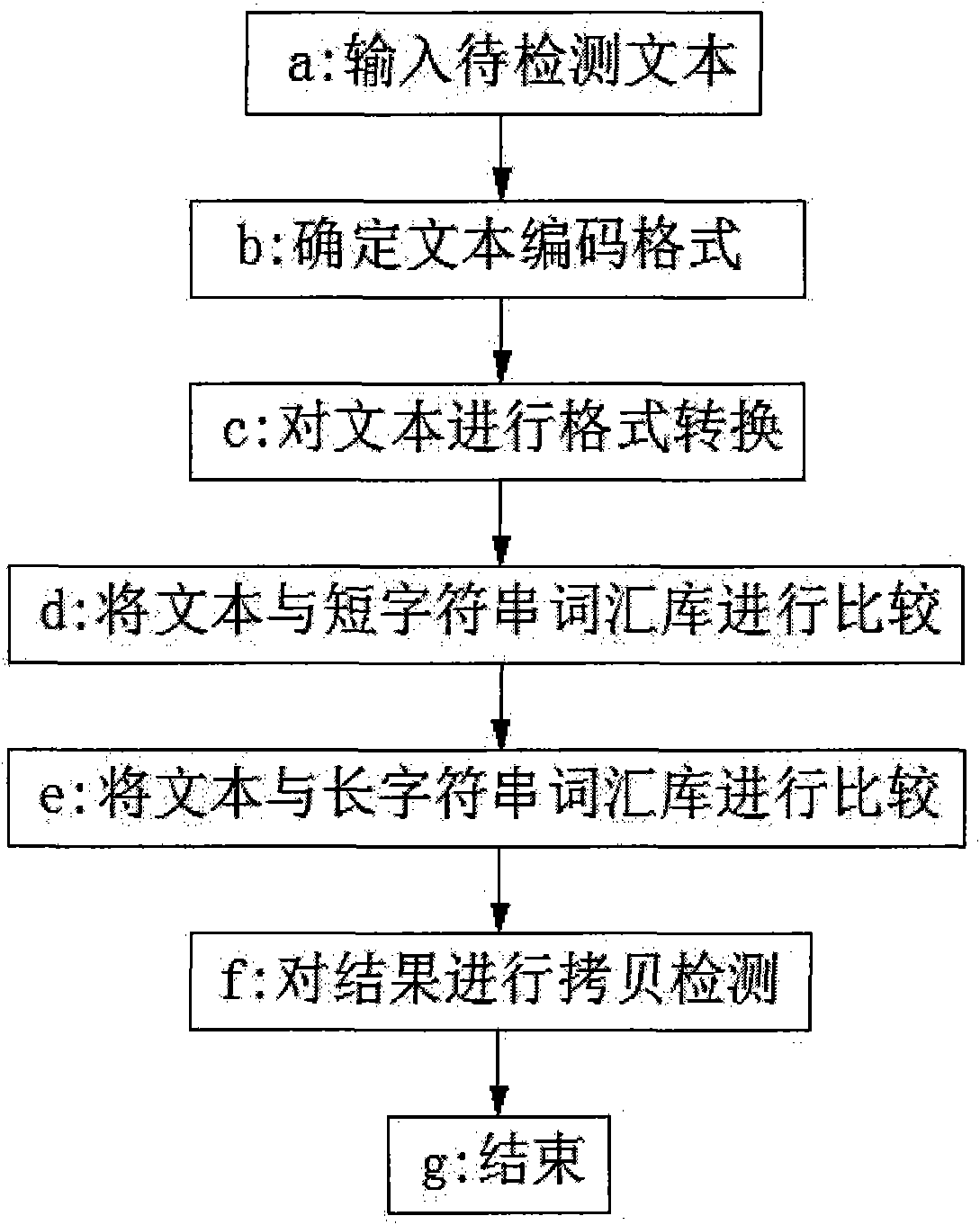
[0013] a: Determine the text encoding format. Currently, there are two mainstream encoding formats on the Internet: GBK and UTF8. The two encoding formats are completely different and cannot be mixed with each other. The encoding of GBK has no special format requirements, so it is difficult to identify. But UTF8 has its unique encoding characteristics, so all encodings can be regarded as UTF8 format first, as long as there is a word in the text that does not meet the UTF8 encoding format, it can be regarded as GBK format. If the entire paragraph of text satisfies the UTF8 encoding format, the format is considered to be UTF8 format. If you think it is a waste of time to search the entire text, you can set a threshold K, as long as you find that the consecutive K texts are all in UTF8 format, you can determine that the text is in UTF8 format.
[0014] b: Convert the format of the text. Firstly, removing spaces and tabs on Internet web pages, for example, is equal to detecting...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com