Operating record tracing system and method based on cloud computing
An operation recording and tracking system technology, applied in the field of information security, can solve problems that are difficult to find, and achieve the effect of raising vigilance and avoiding illegal use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
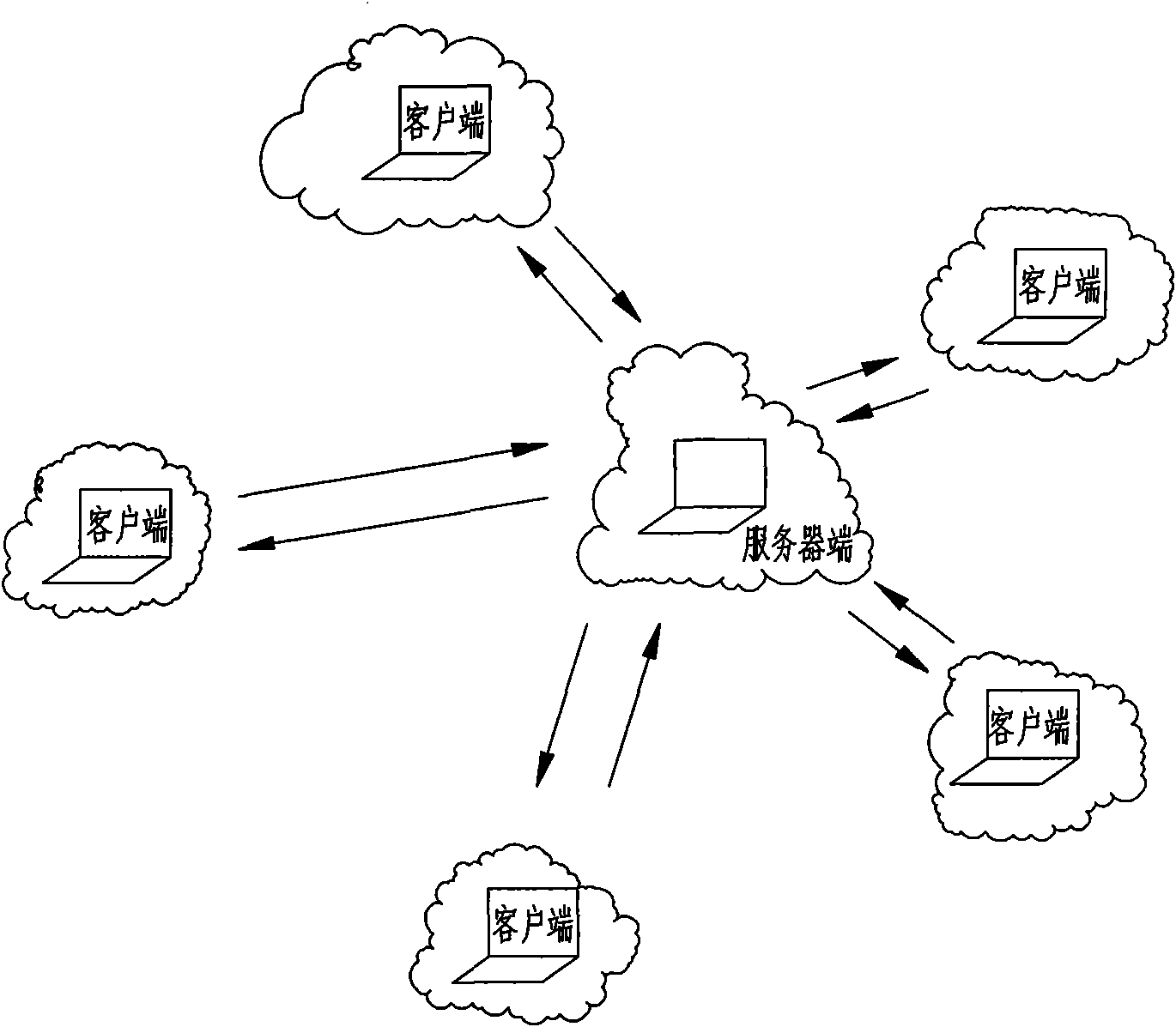
[0036] figure 1 Shown is a schematic diagram of the overall structure of the multi-user collaborative operation record tracking system, including: at least one server and several clients. Multiple servers can be set up as required, and each client is connected to at least one server through the network; The system can include one or more servers, and one client can connect to one or more servers.
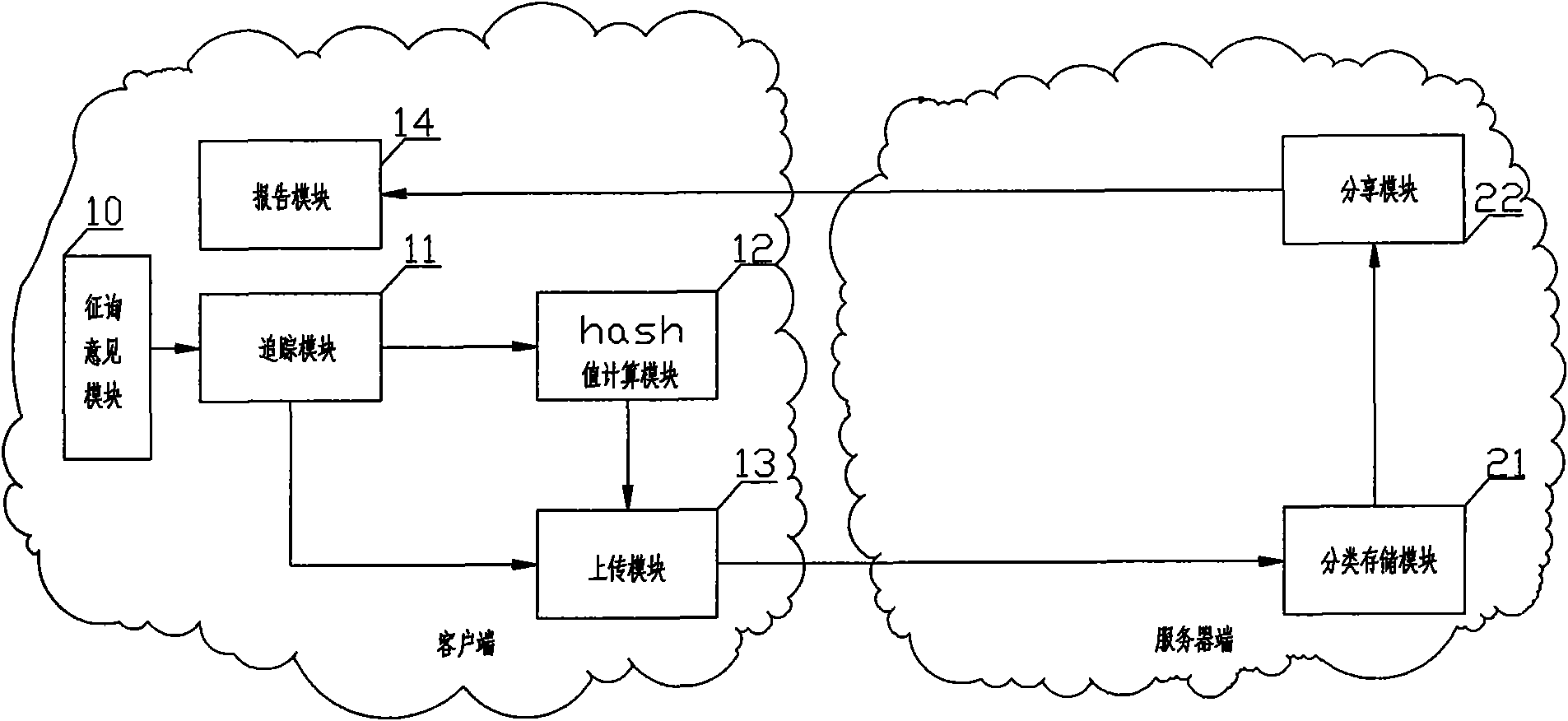
[0037] The client is used to track and obtain the operation records of at least one process run by the client and the process information of the process running on the client. The information can include but not limited to the information of the user to which the process belongs, the company to which the process belongs, etc., and the operation records of multiple processes can be tracked as needed; then the hash value of the process is calculated, and the server receives data from a large number of For the above hash value and process information of the client, on the server side,...
Embodiment 2
[0043] On the basis of Embodiment 1, in order to improve the human-computer interaction function, the client also includes an opinion-seeking module 10, which is connected to the tracking module 11, and is used to consult the client user's opinion on whether the tracking module 11 starts tracking, If the affirmative answer of the client is obtained, the tracking module 11 will immediately start tracking. For example, before starting the tracking process B.EXE, the user will be asked whether to start tracking the process. If the user selects an affirmative answer, the tracking module 11 will begin to track the process B.EXE traces, which can avoid unnecessary tracing and recording of some routine processes.
Embodiment 3
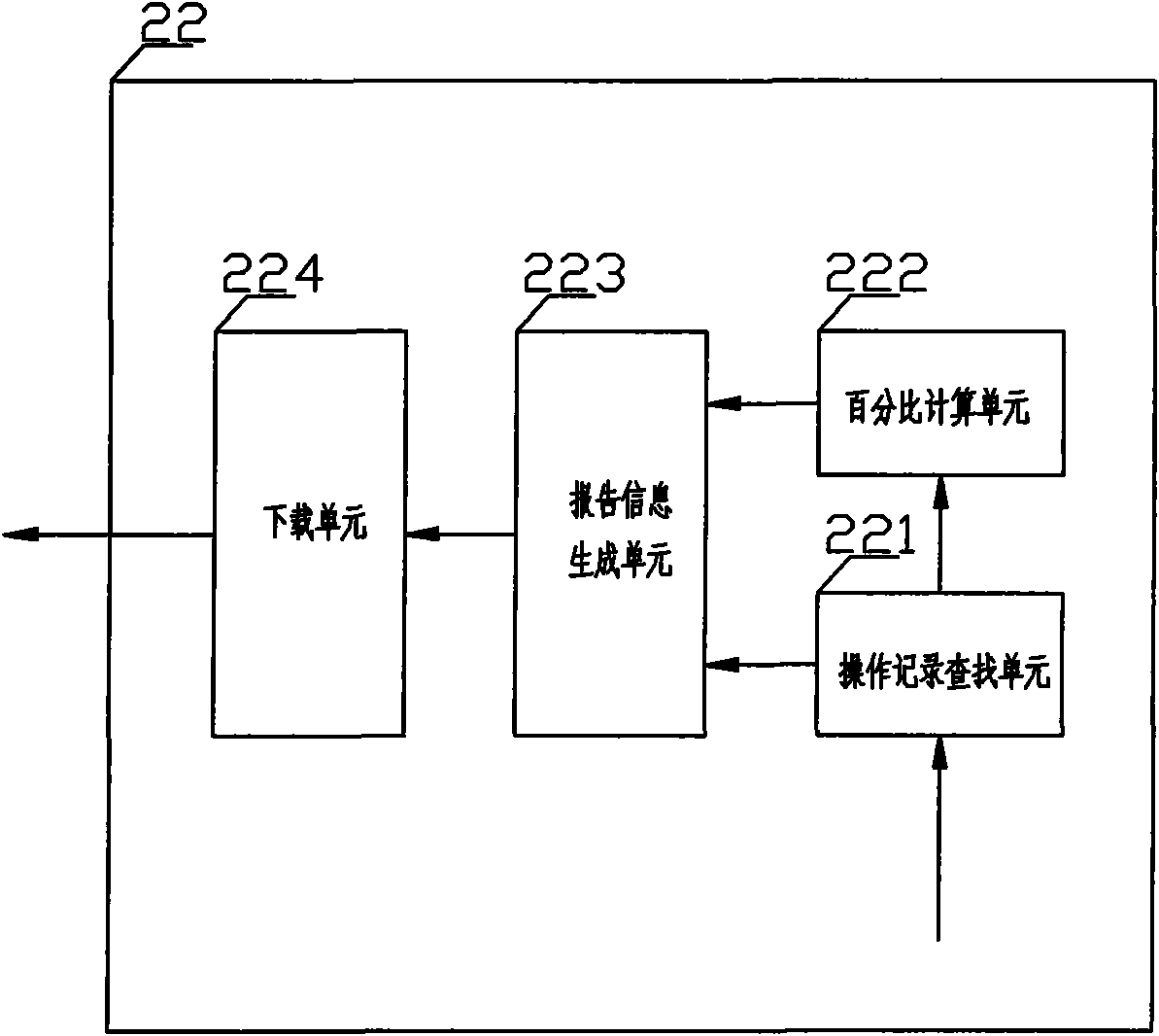
[0045] On the basis of Embodiment 1, in order to further complement and perfect the function of the system, the sharing module can further include an operation record search unit 221, a percentage calculation unit 222, a report information generation unit 223 and a download unit 224; the operation record search unit 221 is used to In the classification storage module 21, search for the operation record and the information of the process with the same hash value, generate a search result, for example, use the hash value as a search condition, search in the classification storage module 21, and search for the hash value The operation records of the same process, and the recorded user quantity and user information generate search results; the percentage calculation unit 222 is used to generate the operation record percentage according to the above search results; the report information generation unit 223 is used to generate the operation record percentage according to the operatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com