Detecting method of DDOS (distributed denial of service) attacks
A technology for attack detection and data packets, applied in digital transmission systems, electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0123] The present invention will be further described in detail below in conjunction with the drawings and specific embodiments:
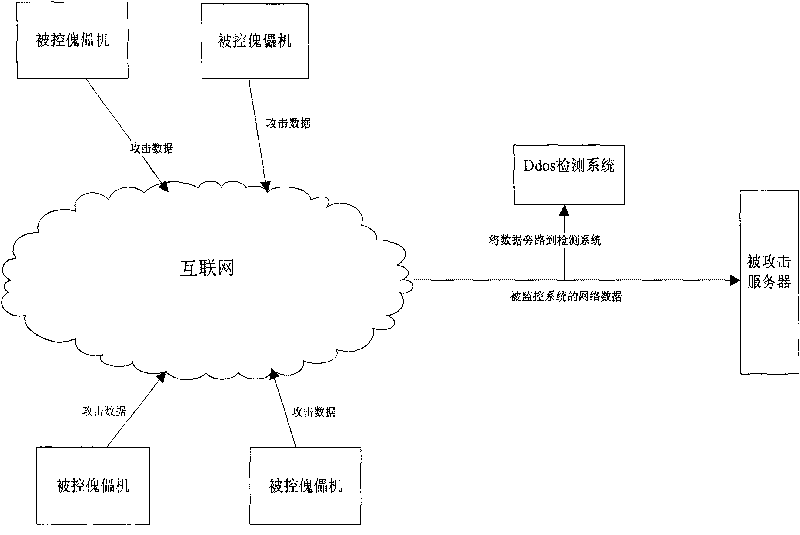
[0124] 1. Connect network traffic to the monitoring equipment in bypass mode.
[0125] According to the different protection objectives, the access location can have the following two options.
[0126] (1) Bypass the network data at the connection between the protected LAN and the external Internet.
[0127] (2) At the exit of the inter-provincial network, the bypass detection device detects the network traffic. At this time, because the network data volume is very large, multiple detection devices can be used for distributed detection.
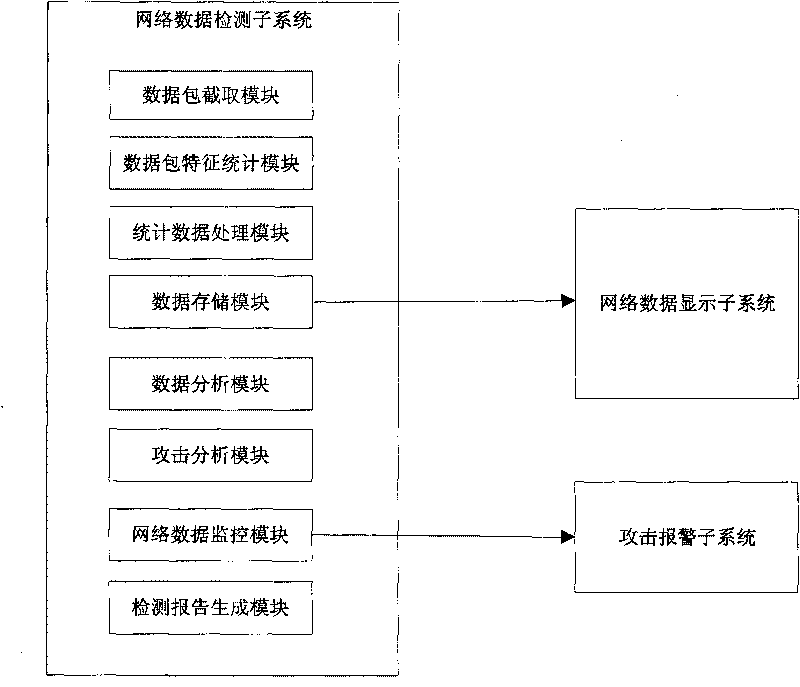
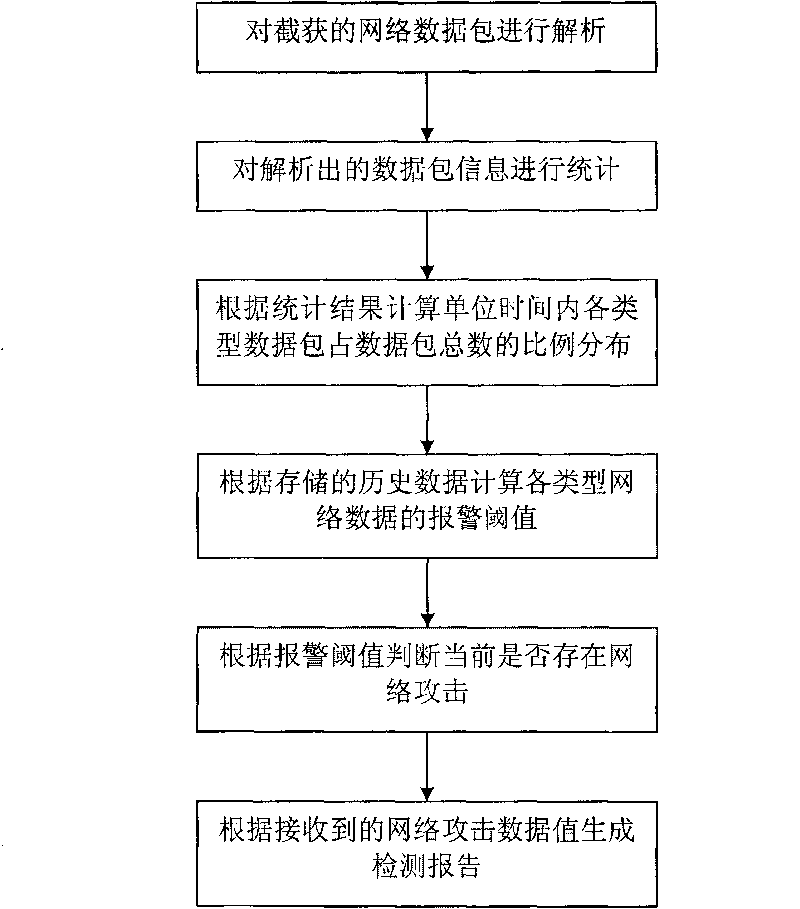
[0128] 2. First, the network data stream flows into the "network data detection subsystem", and the processing methods for the network data stream are as follows: image 3 Shown:
[0129] (1) The "data packet interception module" subsystem of the "network data detection subsystem" analyzes the data packets connected by the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com