Network security-based mirror method and system
A network security and mirroring technology, applied in the field of network communication security, can solve the problem of no traffic being mirrored, and achieve the effect of preventing traffic from being mirrored and ensuring network communication security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
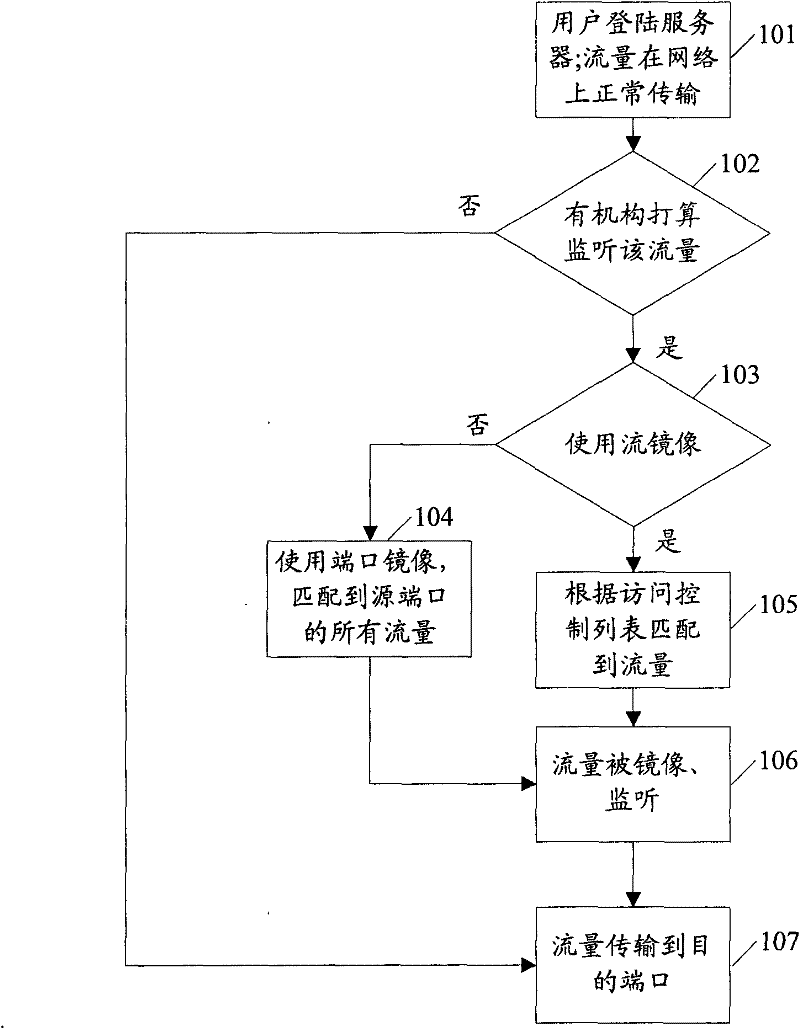
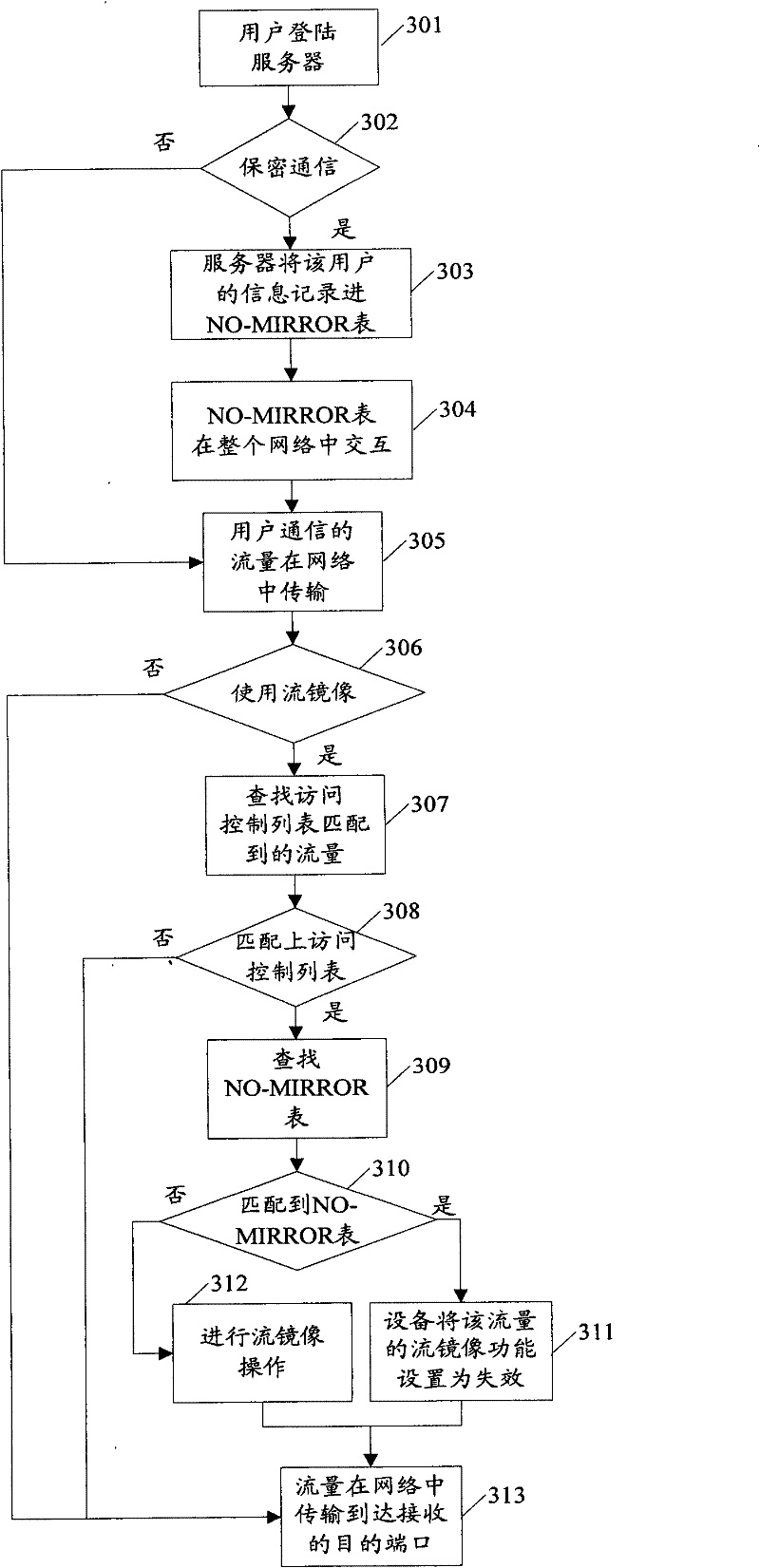
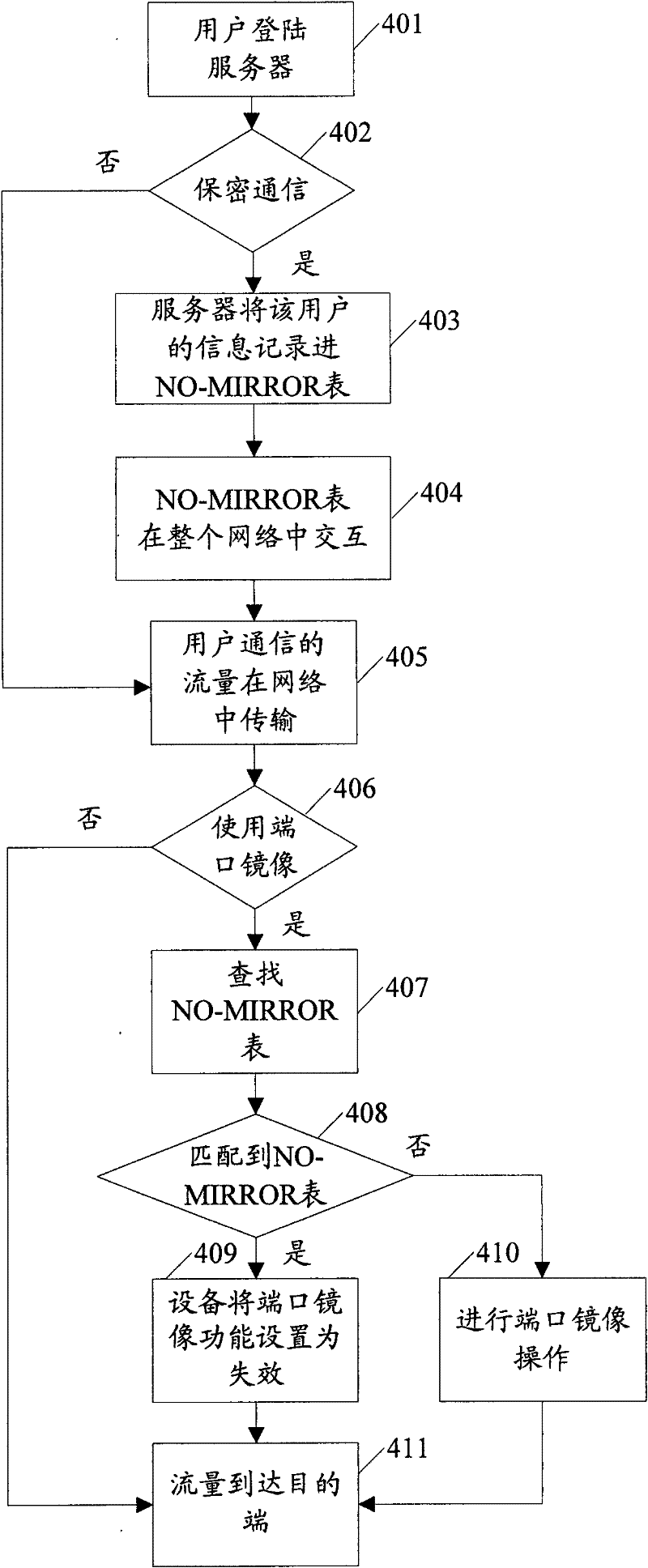
[0041] The basic thought of the present invention is: the NO-MIRROR option that the user enables setting; Write the NO-MIRROR table of user's identification information into setting; When the mode matches the different results of the NO-MIRROR table, the operation of denying the user's traffic to be mirrored is executed respectively.
[0042] The implementation of the technical solution will be further described in detail below in conjunction with the accompanying drawings.
[0043] A mirroring method based on network security, the method comprises the following steps:
[0044] Step 201, the user enables the set NO-MIRROR option.
[0045] Here, the user who enables the NO-MIRROR option in the present invention is the user who refuses to be mirrored, and will not be described in detail below. Different from the prior art, the user of the present invention can add a NO-MIRROR option on its client, if the user does not want the user data traffic to be mirrored in the subsequent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com