Piracy preventing method of system
A technology of anti-piracy and encryption algorithm, applied in the direction of instrument, program loading/starting, electronic digital data processing, etc., can solve the problem of limited anti-piracy function and high cost, and achieve good anti-piracy effect, low cost and small data volume Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
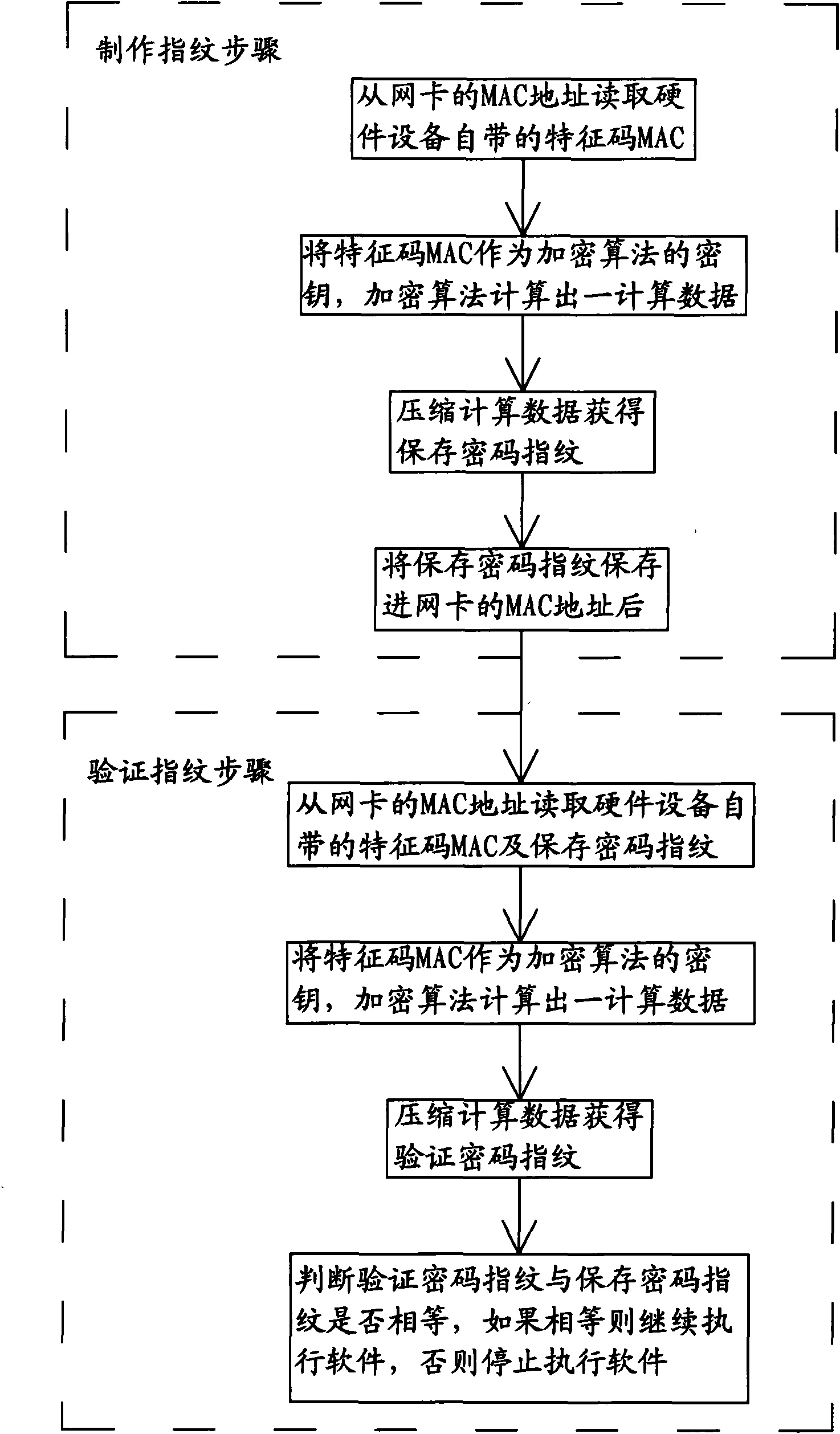
[0026] Please check figure 1 , which is a schematic flow chart of an anti-piracy method in a preferred embodiment of the present invention. The anti-piracy method, which includes:
[0027] Step S100, the step of making a fingerprint, which is executed when installing the software. Generally, the software is installed by a designated user, such as installed by an operator. The step of making a fingerprint includes:
[0028] Step S110, read the feature code MAC of the hardware device from the MAC address of the network card, the MAC is inserted when the hardware device leaves the factory, and has unchangeable and unique characteristics;
[0029] Step S121, using the feature code MAC as the plaintext of the encryption algorithm, and the encryption algorithm calculates a calculation data;
[0030] Step S122, compressing the calculation data to obtain and save the cryptographic fingerprint, the cryptographic fingerprint data can be compressed into a single byte;
[0031] Step S1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com