Target attack and defense method specific to optimized link state routing protocol
A link state and routing protocol technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as destroying integrity, providing error messages, and affecting network topology, achieving highly targeted effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] - Attack method steps
[0046] Step 1) Implant malicious nodes in the network, do not launch malicious attacks at the beginning, only eavesdrop on relevant routing information,
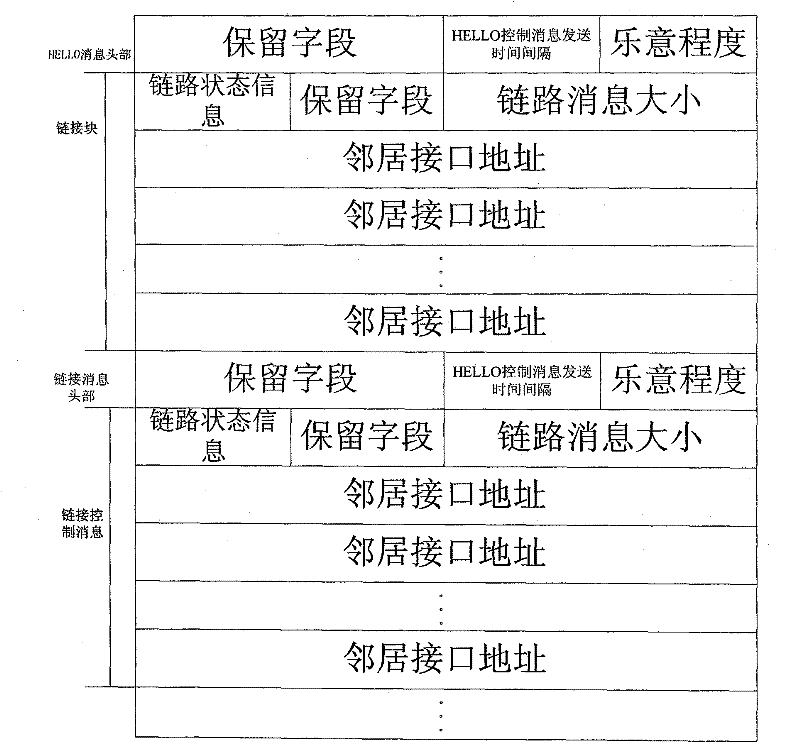
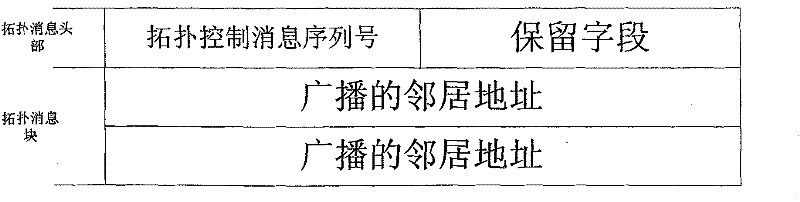
[0047] Step 2) Send attack command, start malicious attack, malicious node receives the topology control message that source node A produces, i.e. TC message, records the sequence number of this TC message, i.e. ANSN,
[0048] Step 3) On the basis of step 2), the malicious node resends a new topology control message, the source address is still set as the initial source address, and the new serial number is to add 5 to the original serial number, namely ANSN 新 =ANSN 旧 +5,
[0049]Step 4) In the optimal link state routing protocol, the node will ignore the TC message sent by the source node A for a subsequent period of time,
[0050] Step 5) set a timer, and take the operation of step 3) every 5s;
[0051] Two detection method steps
[0052] Step 2 1) In the topology discovery within the O...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com