Authentication method and system of subscriber identity module and terminal
A technology of subscriber identification module and terminal, which is applied in the field of wireless communication, and can solve problems such as the inability to determine the party responsible for the leakage, many parties knowing the key, and key leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
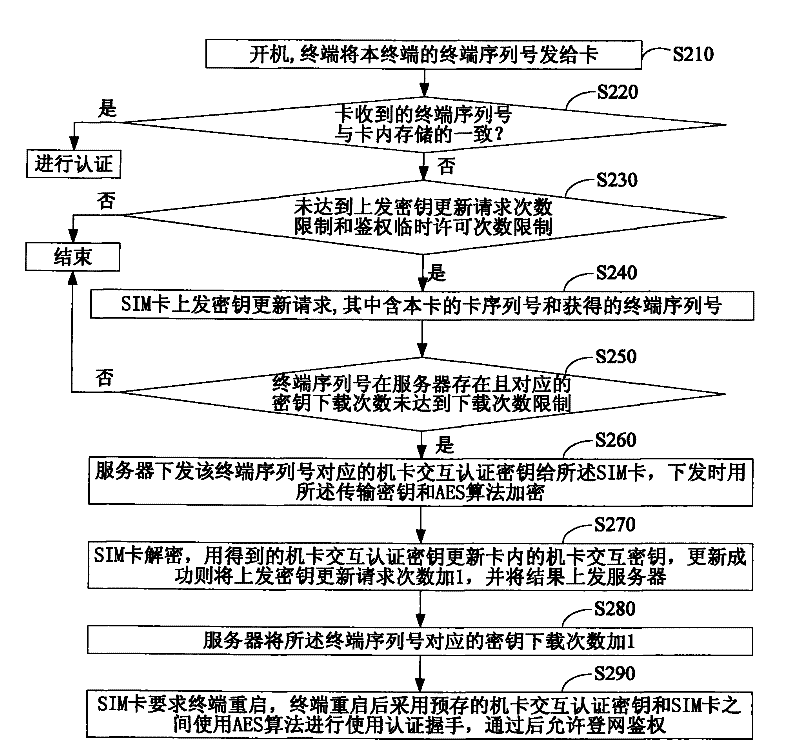
[0076] Embodiment 1, a method for authenticating a subscriber identity module and a terminal, such as figure 1 shown, including:
[0077] Step S110, when the subscriber identification module determines that the authentication key with the terminal needs to be obtained, send a key update request to the key management system platform, which carries the identity of the subscriber identity module and the identity of the terminal;
[0078] Step S120, after the key management system platform receives the key update request, it generates a message carrying the authentication key according to the identity of the terminal, and determines the transmission key corresponding to the identity of the subscriber identity module; The transmission key and the transmission encryption and decryption algorithm encrypt the message carrying the authentication key and send it to the subscriber identification module;
[0079] Step S130, the subscriber identification module decrypts the message using ...
Embodiment 2
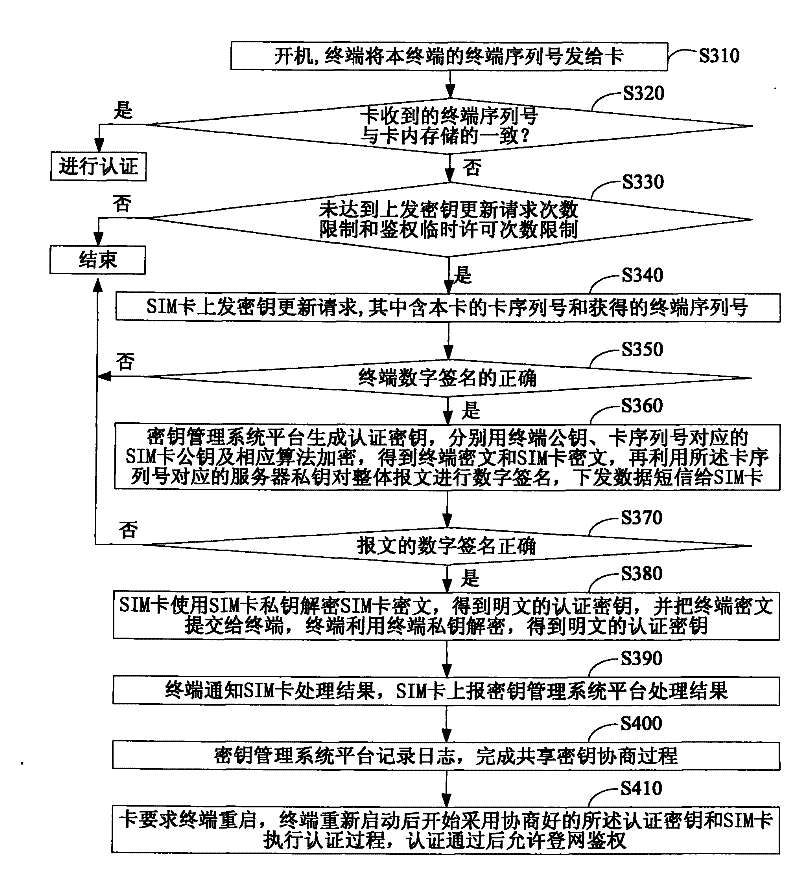
[0190] Embodiment 2, a system for authentication between a user identification module and a terminal, such as Figure 4 As shown, including: subscriber identity module, terminal and key management system platform;
[0191] The user identification module is used to send a key update request to the key management system platform when it is determined that an authentication key with the terminal needs to be obtained, which carries the identification of the user identification module and the identification of the terminal; When receiving the message returned by the key management system platform, use the pre-stored transmission key and the transmission encryption and decryption algorithm to decrypt the message, and obtain the authentication key according to the decrypted message and save it;
[0192] The terminal pre-stores the authentication key, or obtains the authentication key according to the decrypted message of the subscriber identification module; uses the authentication k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com