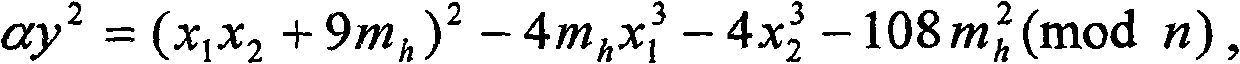Identity authentication method adopting password firewall
A technology of identity authentication and password authentication, applied in the field of information security, can solve problems such as inconvenience and increase the cost of computer application system construction and operation, and achieve the effect of careful security protection and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
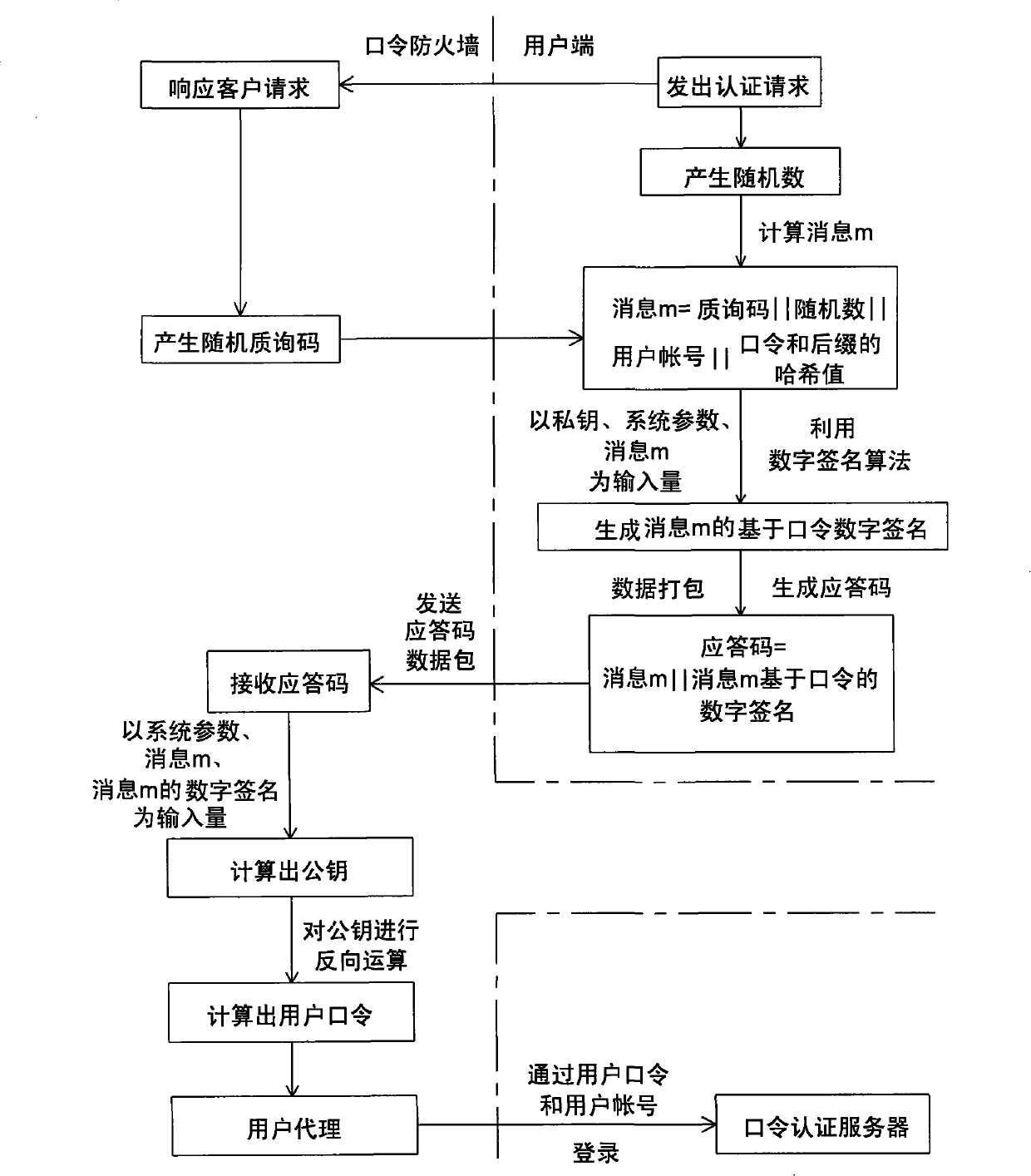
[0035] Please refer to figure 1 , the present invention is an identity authentication method using a password firewall, the system applied to the method physically / logically includes a password firewall, a private key generator, a user terminal and a password authentication server, wherein the private key generator can be regarded as a password firewall The client side is physically / logically outside the password firewall, and the password authentication server is physically / logically inside the password firewall. This identity authentication method is made up of initialization mechanism (A) and user identity authentication mechanism (B), it is characterized in that: described initialization mechanism (A) comprises the steps:
[0036] Step (A1), the private key generator performs an initialization operation, uses software or hardware to randomly generate two secret large prime numbers, which are recorded as p and q respectively, and uses them to form the master key required by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com