Totally-blind digital speech authentication method
A technology of digital voice and authentication method, applied in the field of digital voice authentication, digital voice material tampering authentication and tampering area positioning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
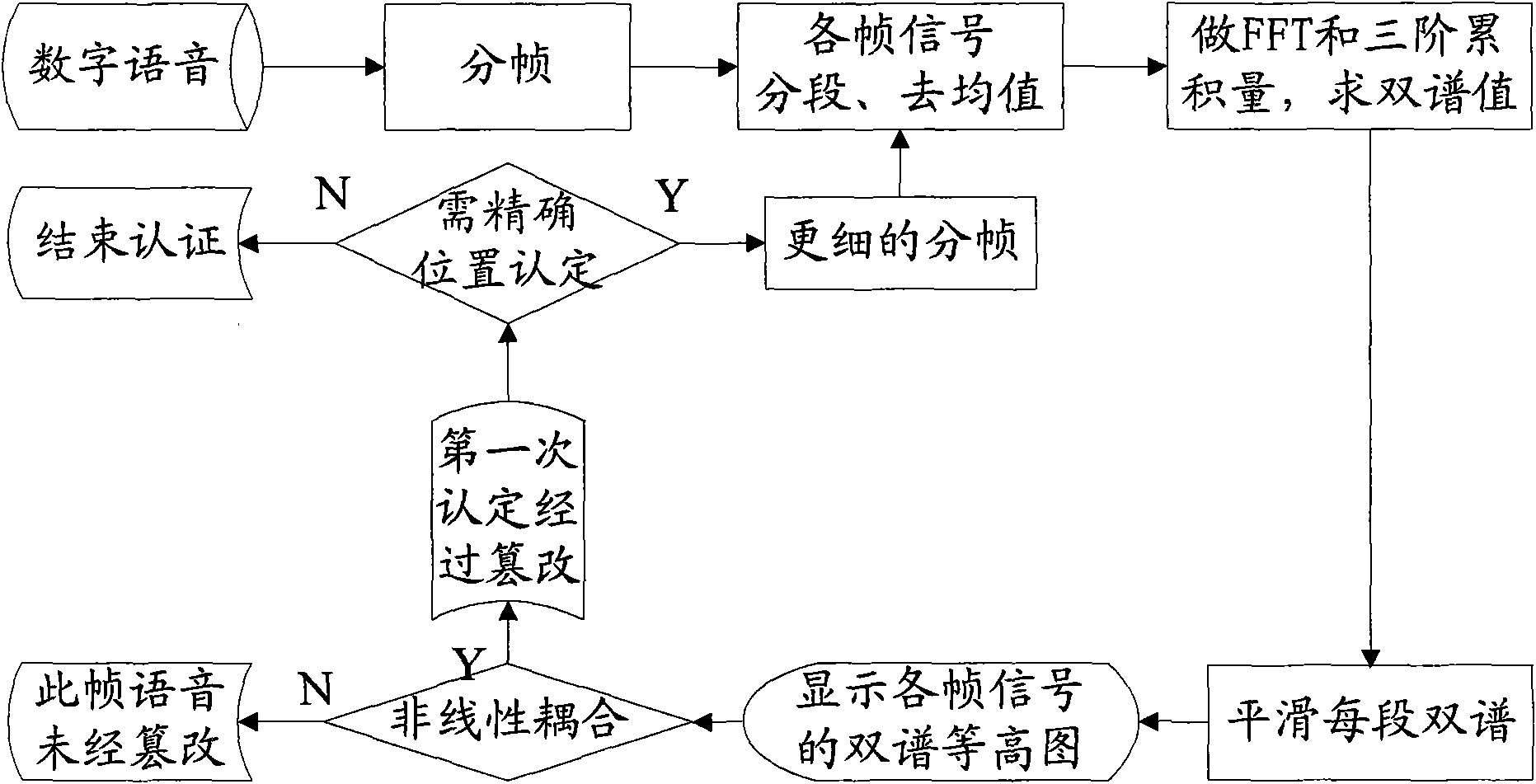
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
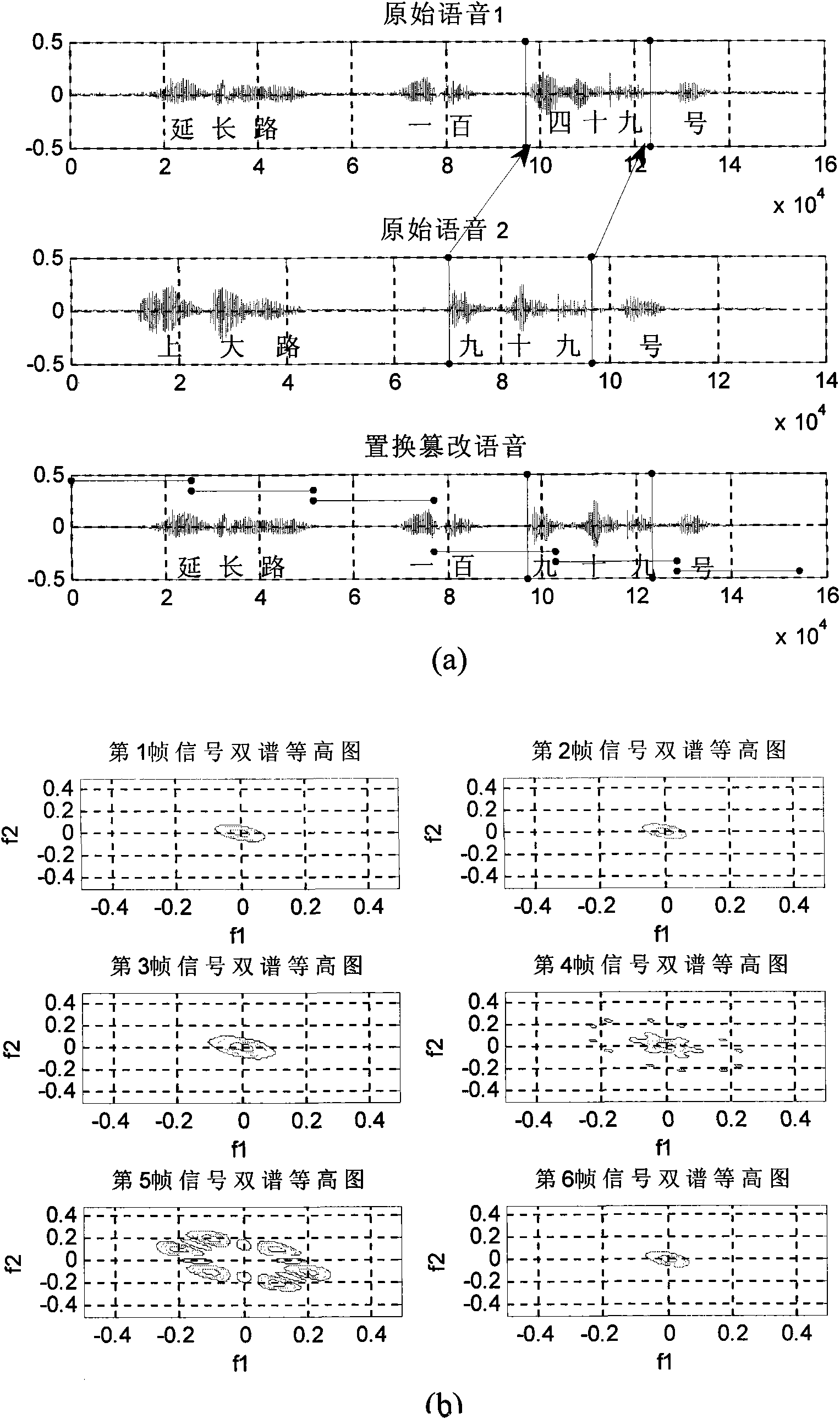
[0040]The full-blind digital voice authentication method of the present invention is used to discriminate the replacement and tampering voice waveform display and the bispectrum contour map display of each frame of voice, such as figure 2 As shown in the figure (a), the replacement voice "No. 199 Yanchang Road" is replaced by "99" in the original voice 2 "No. 99 Shangda Road" in the original voice 1 "No. 149 Yanchang Road" A new audio signal is obtained. In the analysis process, the replaced speech signal is divided into 6 frames for processing, and the joints of the above-mentioned replaced speech are respectively in the 4th and 5th frames. Figure (b) shows the bispectrum contour of each frame obtained by this method analysis In the figure, the 4th frame and the 5th frame have obvious nonlinear coupling phenomenon, and it is determined that these two frames have been tampered with.
specific Embodiment 2
[0041] The fully blind digital voice authentication method of the present invention is used to discriminate splicing and tampering voice waveform display and each frame of voice bispectrum contour map display, such as image 3 As shown, the spliced voice "LV830" in Figure (a) is a new voice obtained by splicing the voice segment "LV" in the original voice 1 "LV316" and the voice segment "830" in the original voice 2 "PY830". voice. In the analysis process, the spliced speech is divided into 5 frames for processing, and the junction of the two speech segments is in the third frame. Figure (b) shows the framing of the spliced and tampered speech signal in Figure (a) and this The method analyzes the obtained bispectral contour map of each speech frame, and the third frame has obvious nonlinear coupling phenomenon, and it is judged that the speech of this frame is tampered with.
specific Embodiment 3
[0042] The fully blind digital voice authentication method of the present invention is used to discriminate the insertion tampering voice waveform display and the bispectrum contour map display of each frame of voice, such as Figure 4 As shown, the insertion of Figure (a) tampers with the speech "I don't like it", which is cut and inserted into the original speech 2 "I like it" by the monophonic "No" in the original speech 1 "Nobody wants this" The new voice obtained in the. In the analysis process, the inserted tampered speech is divided into 5 frames for processing, and the two joints of the inserted single tone are respectively in the second frame and the third frame. Figure (b) shows the inserted tampered speech signal in Figure (a). The framing situation and the bispectral contour map of each speech frame obtained by this method analysis, in which the second and third frames have obvious nonlinear coupling phenomenon, it is judged that the speech of the second and third ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com