Elliptical curve-based method and elliptical curve-based device for self-authenticating signature
A technology of elliptic curve and verification method, which is applied in the field of cryptography and can solve problems such as key escrow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
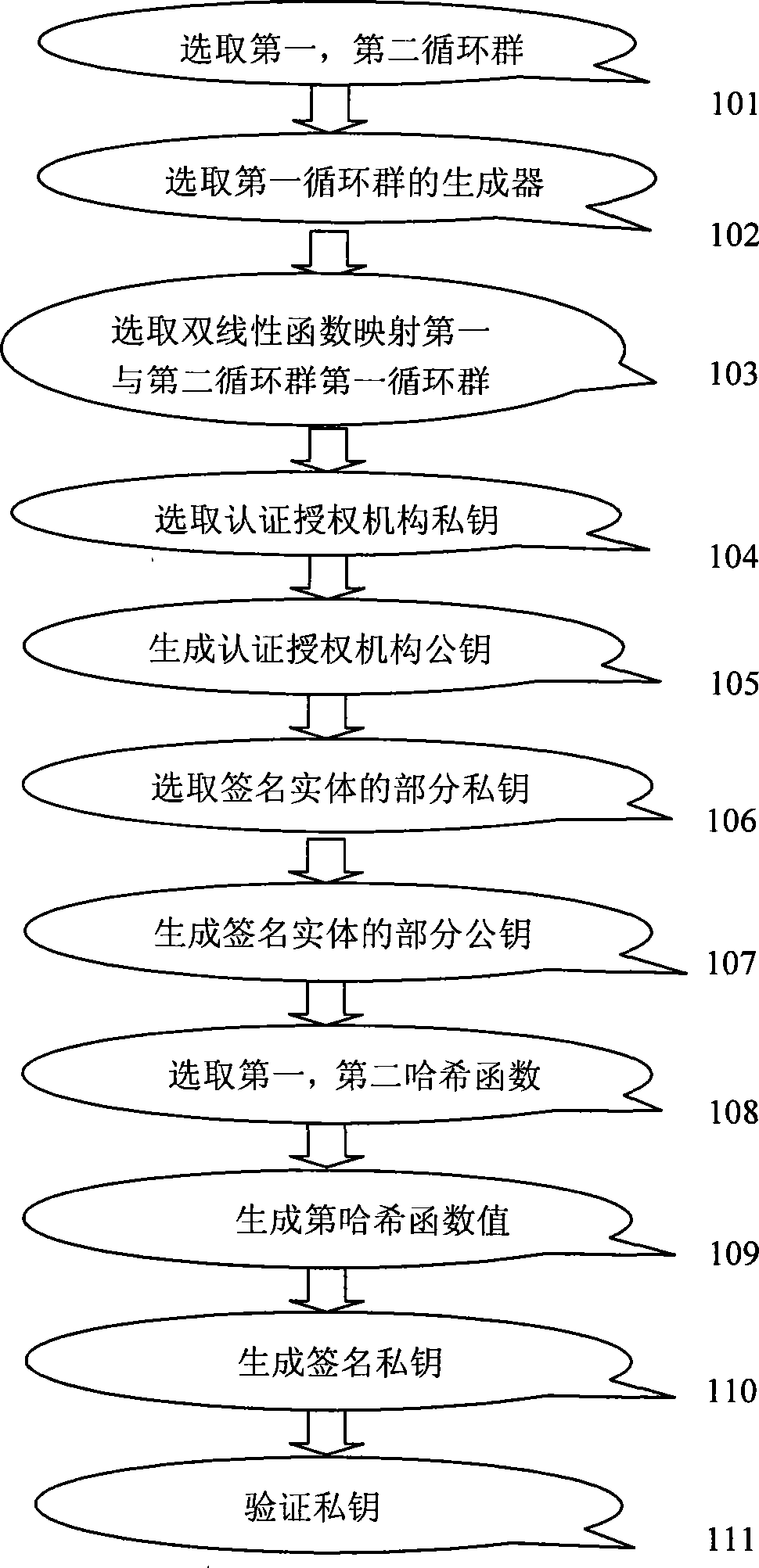
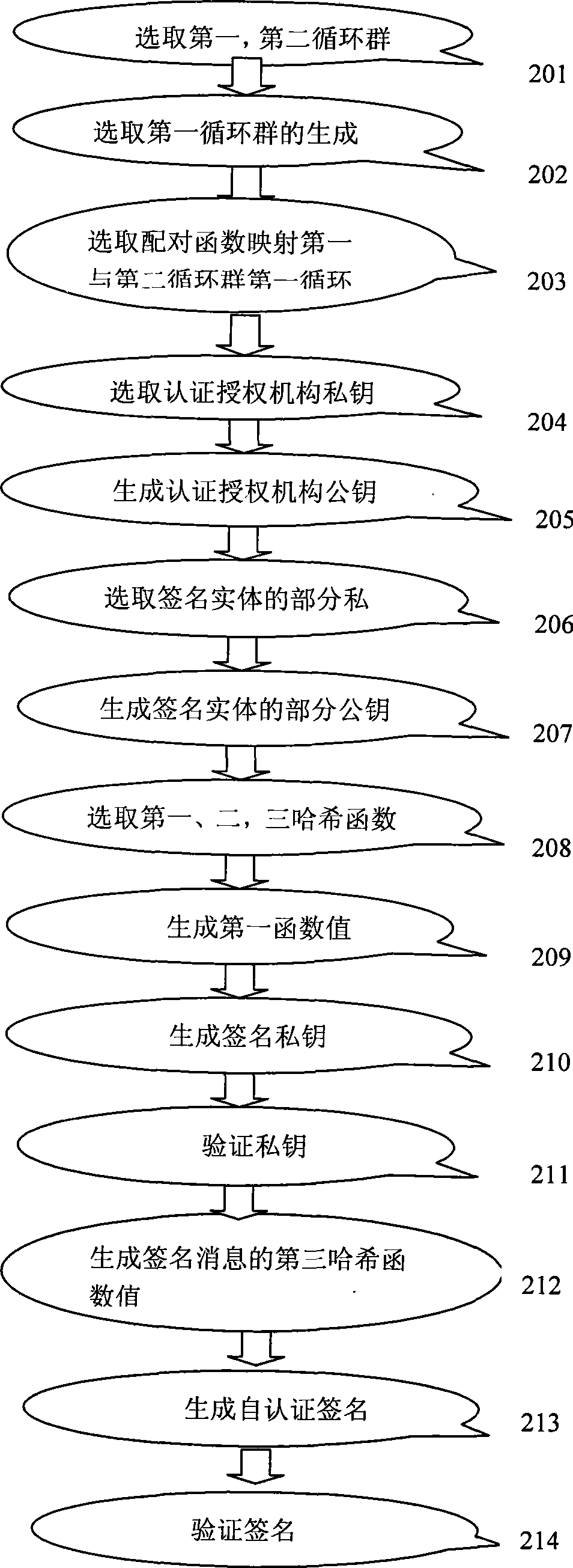
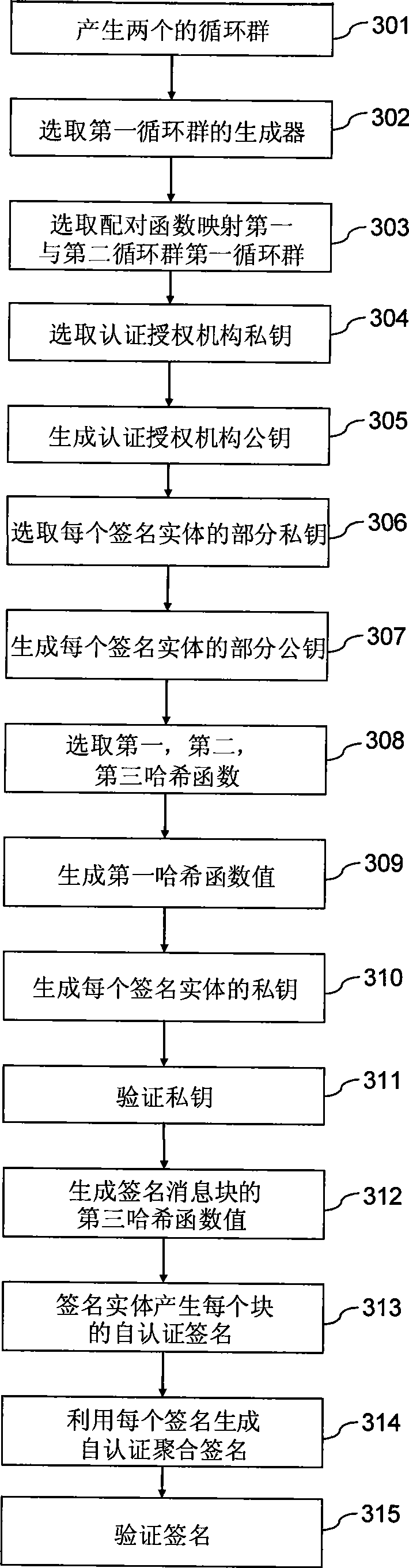
[0057] The self-authentication signature method based on elliptic curve proposed by the present invention can provide a safe, fast, concise and effective signature method, and prevent the extension of signature rights by setting the signature key of the signature entity. The self-authentication signature method based on elliptic curves proposed by the present invention can be extended to satisfy one-to-many aggregate signatures according to different signature entities and signature messages, that is, one signature entity performs self-authentication signatures on different messages, and then, these A method of message signature aggregation into one signature; in order to improve the speed of online signature, a method of on / offline self-authenticated message signature is given.
[0058] The self-authentication signature method based on the elliptic curve of the present invention needs a certification authority CA in the generation of the user's partial private key. During the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com