Digital copyright management proxy system based on dependable computing concept
A technology of credible computing and thinking, applied in the direction of electronic digital data processing, computing, computer security devices, etc., can solve the problems of digital copyright protection, improve security and anti-cracking ability, ensure security, ensure Effect of legitimate interest
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings, but the present embodiments are not intended to limit the present invention, and all similar structures, methods and similar changes of the present invention should be included in the protection scope of the present invention.
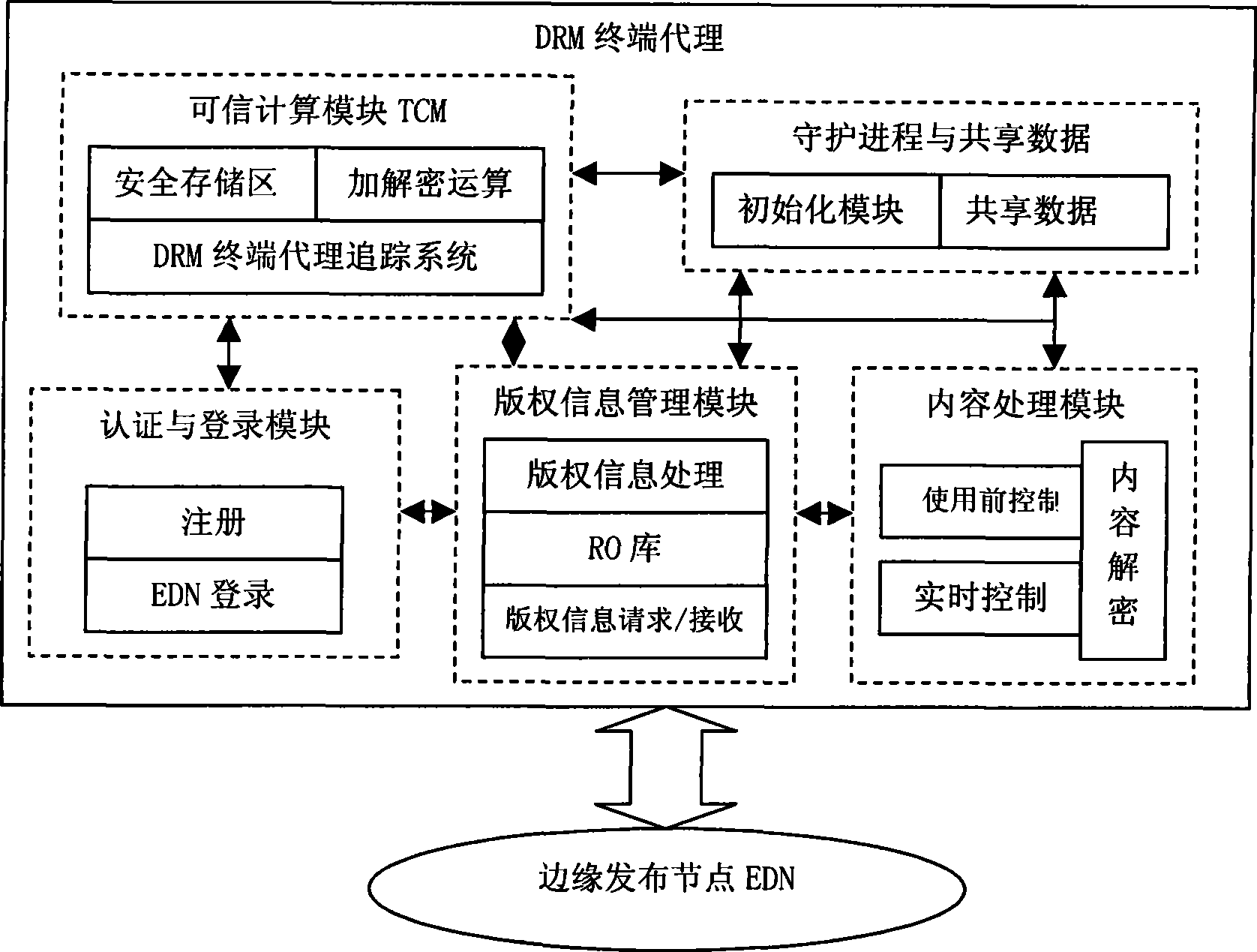
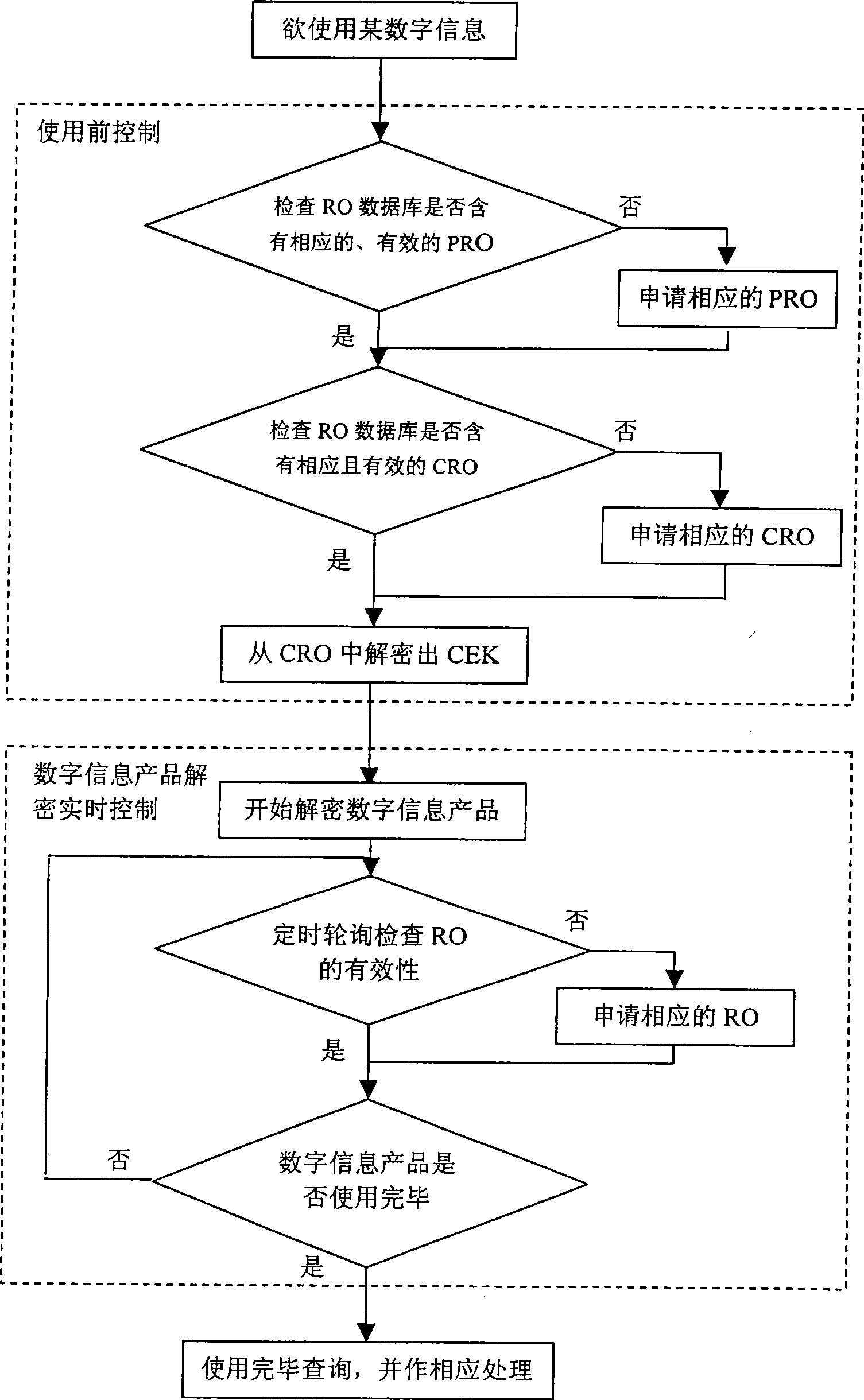
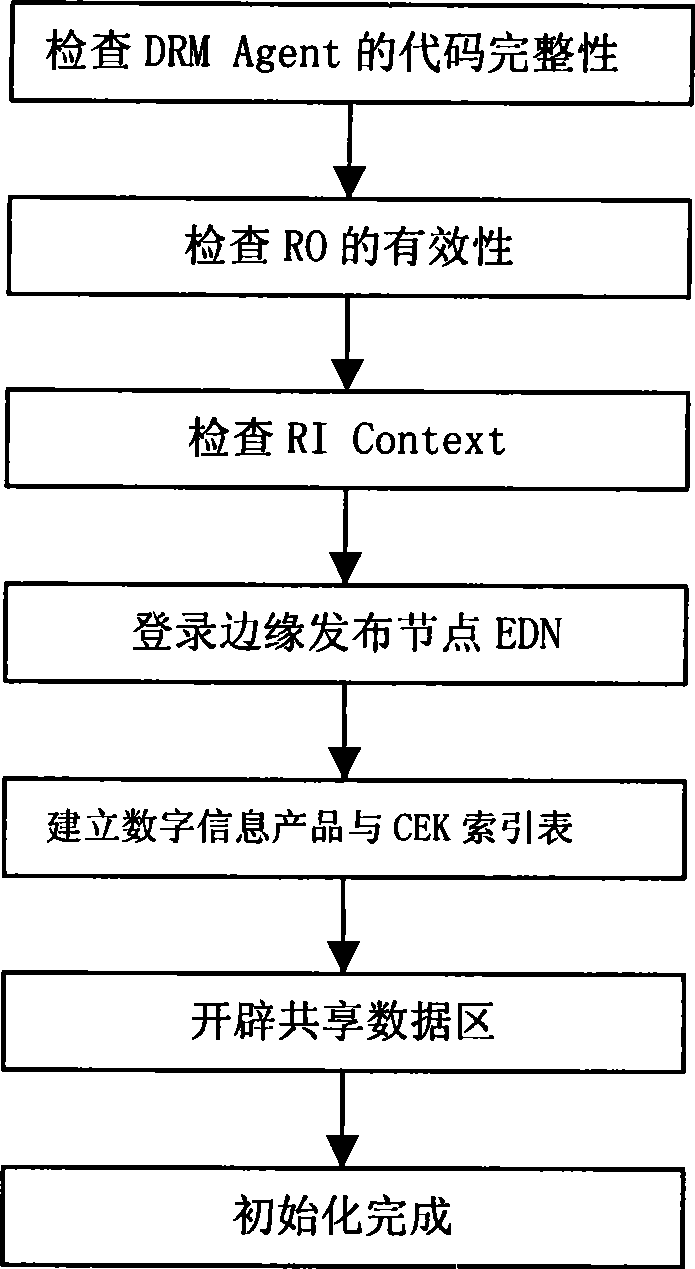
[0031] The DRM Agent based on the trusted computing idea proposed by the present invention is characterized in the following four aspects: first, the DRM Agent proposed by the present invention is based on the trusted computing idea; second, the DRM Agent is composed of the trusted computing module TCM, Authentication and login module, copyright information management module, content processing module, daemon process and shared data modules; third, trusted computing module TCM is used to save DRM Agent private key information, verify DRM Agent core code integrity, and decrypt CEK etc.; Fourth, for the realization of DRM Ag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com