Flow linkage control method, apparatus and system
A linkage control system and linkage control technology, applied in the network field, can solve problems such as inability to control illegal traffic, achieve the effect of improving the ability to resist malicious traffic attacks and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
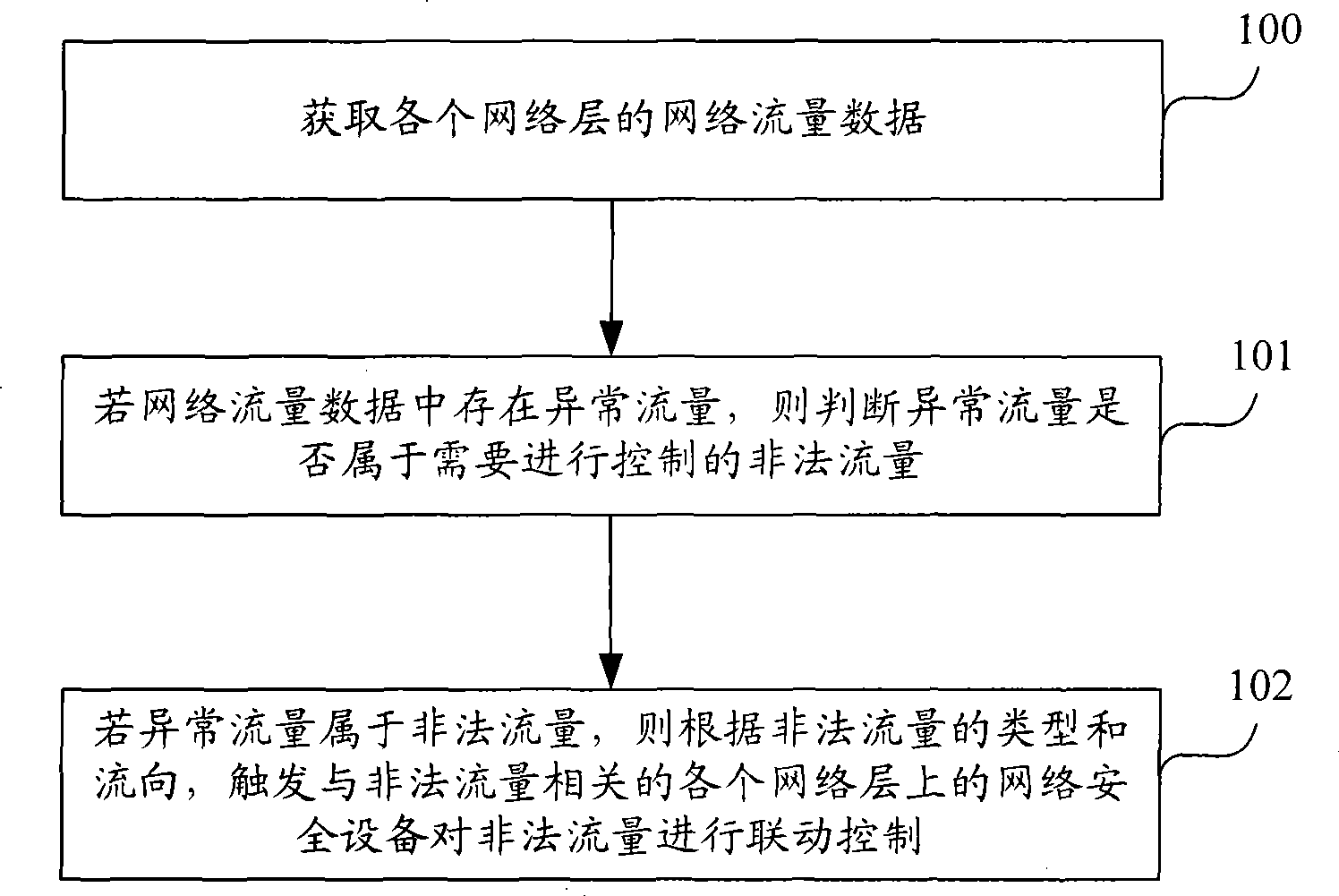
[0024] figure 1 It is a flow chart of the first embodiment of the traffic linkage control method of the present invention, as shown in figure 1 As shown, the traffic linkage control method of the present invention includes:
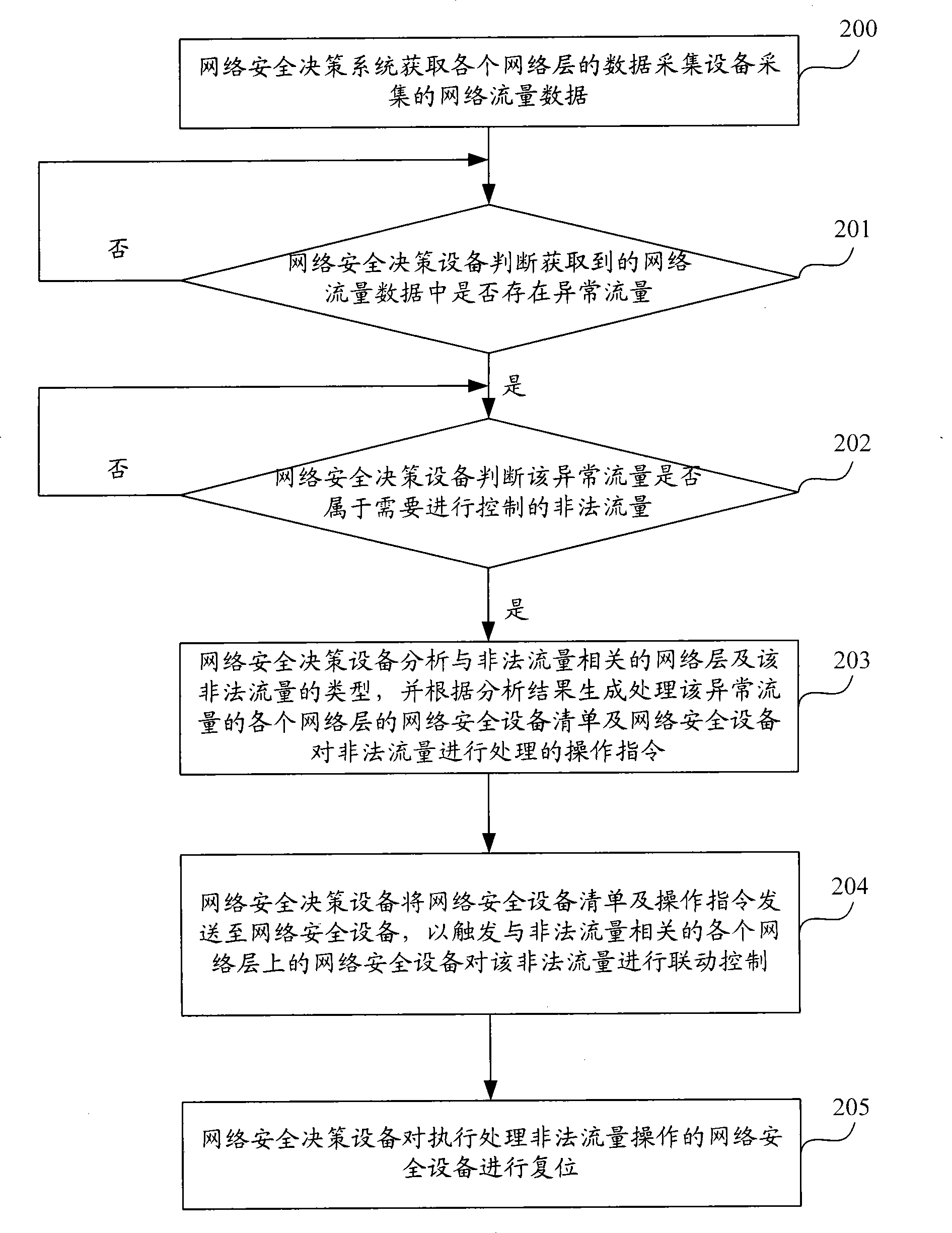
[0025] Step 100, the network security decision-making device acquires network traffic data of each network layer;
[0026] Step 101, if there is abnormal traffic in the acquired network traffic data of each network layer, the network security decision-making device judges whether the abnormal traffic belongs to illegal traffic that needs to be controlled;
[0027] Among them, the abnormal traffic may be divided into many situations. For example, if the abnormal traffic is only a large amount of traffic but there is no malicious attack, the abnormal traffic is not illegal traffic and does not need to be controlled. If the traffic size is normal but there are Malicious attacks are illegal traffic and need to be controlled.
[0028] Step 102, if the abn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com