Identification authentication method for communication entity based on combined public key
A communication entity and identity authentication technology, which is applied in the field of communication entity identity authentication based on combined public keys, can solve a large number of user parameters and other problems, and achieve low implementation cost, less resource occupation, and less impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
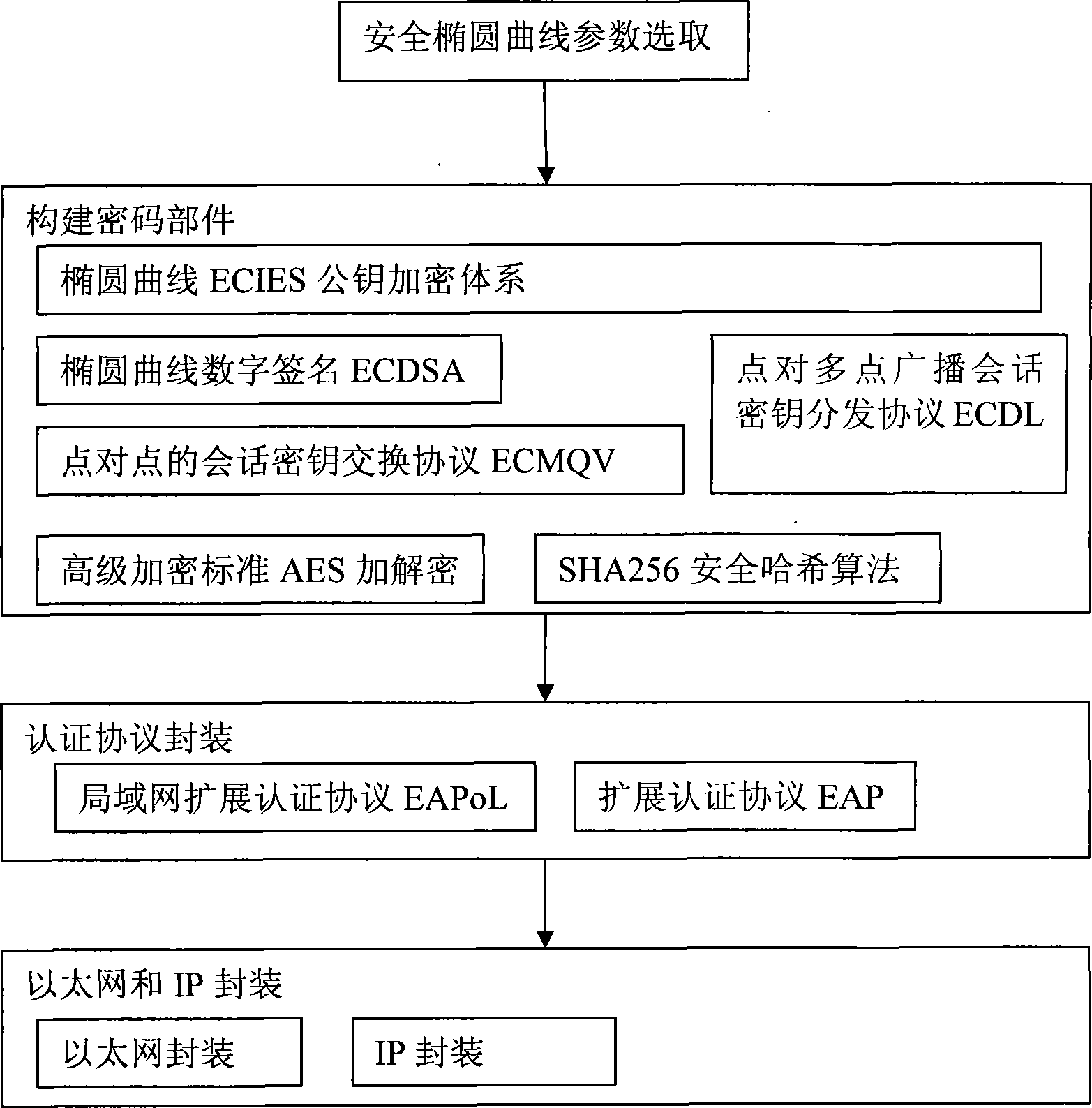
[0022] refer to Figure 1 to Figure 3 , the present invention comprises steps as follows:
[0023] ① According to the "ECDSA and ECDH Cryptographic Algorithm Elliptic Curves and Parameters Adopted by Wireless Local Area Network Products" issued by the National Commercial Cryptography Management Office, determine the security elliptic curve parameters for communication entity identification authentication.
[0024] Embodiment The ECDSA that the present invention adopts and the ECDH cryptographic algorithm elliptic curve and parameter are as shown in the table below:
[0025]
[0026] In the above table, p, a, b are safe elliptic curve y 2 =x 3 The parameter of +ax+bmod p, G=(x G ,y G ) is a point of order n on the elliptic curve, called the base point.
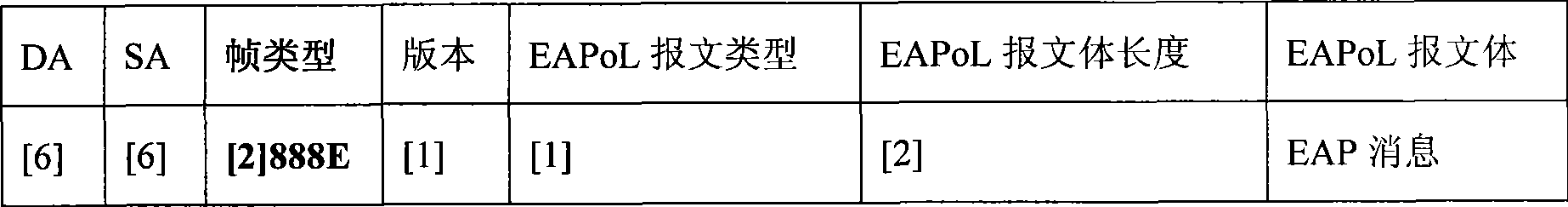
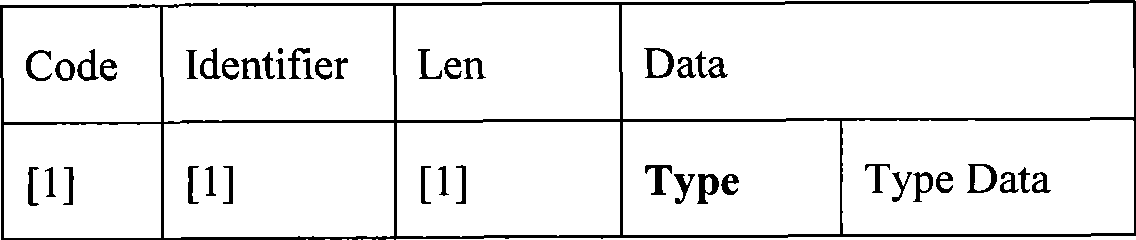
[0027] ② According to the recommendations of the International Institute of Electrical and Electronics Engineers IEEE 1363-2000 and IEEE1363a, construct the elliptic curve ECIES public key encryption system between comm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com