Authentication method, system and apparatus for communication
A communication system and authentication technology, which is applied in the communication field, can solve problems affecting user experience, authentication failure, and increasing user access delay, so as to improve experience, reduce the frequency of secondary authentication, and improve access time. Delayed effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
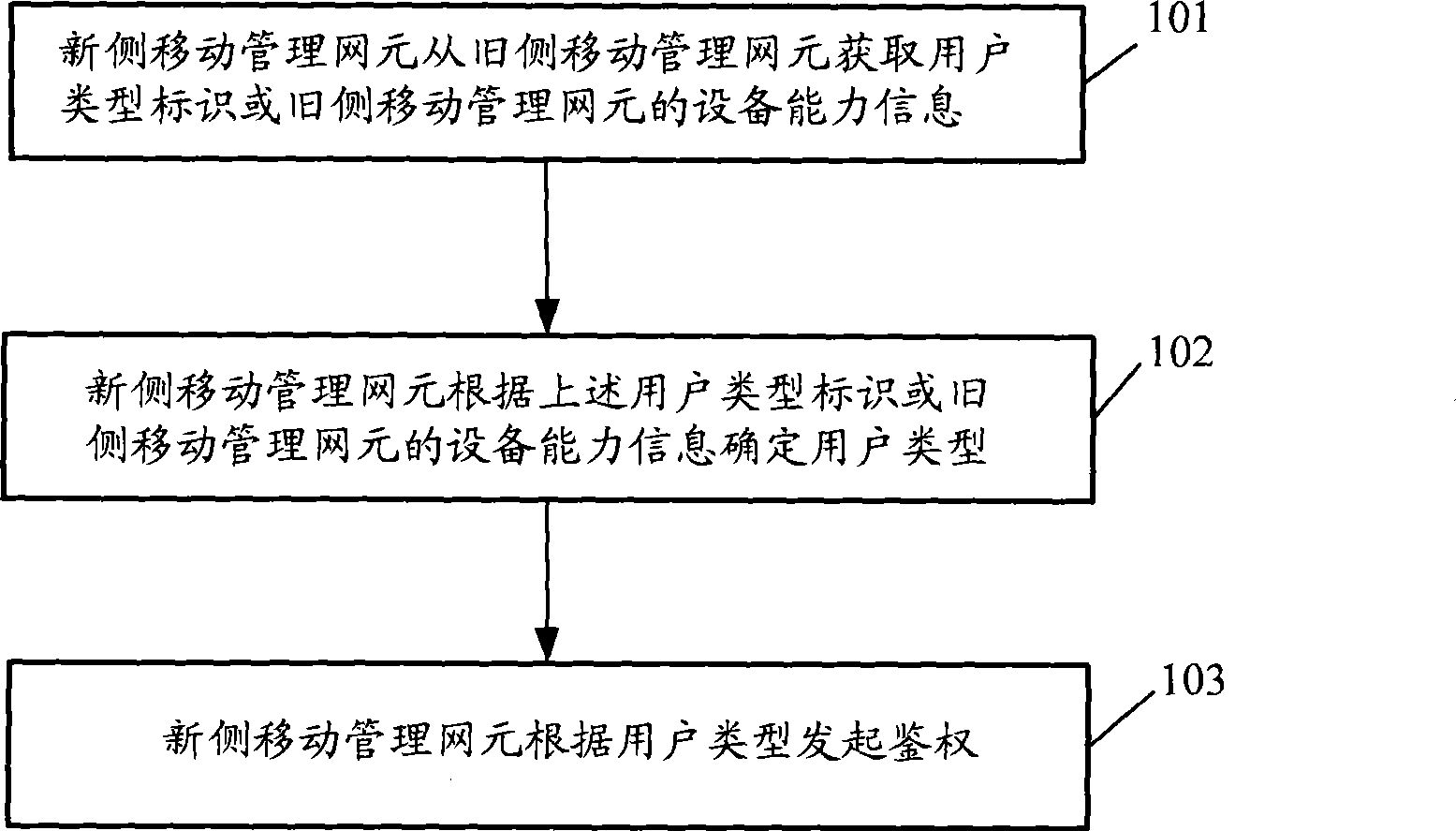
[0037] This embodiment describes an authentication method, through which the mobile management network element on the new side can accurately know the user type.
[0038] Describe in detail below in conjunction with accompanying drawing, see figure 1 , the method of this embodiment may include the following steps:
[0039] Step 101: The mobility management network element on the new side obtains the user type identifier or equipment capability information of the mobility management network element on the old side from the mobility management network element on the old side;
[0040] Before step 101, the old-side mobility management network element may also receive a network access request message sent by a user, where the network access request message includes a user type identifier.
[0041] Before step 101, it may also include that the old-side mobility management network element obtains the user type identifier through a request response message sent by the user data serv...
Embodiment 2
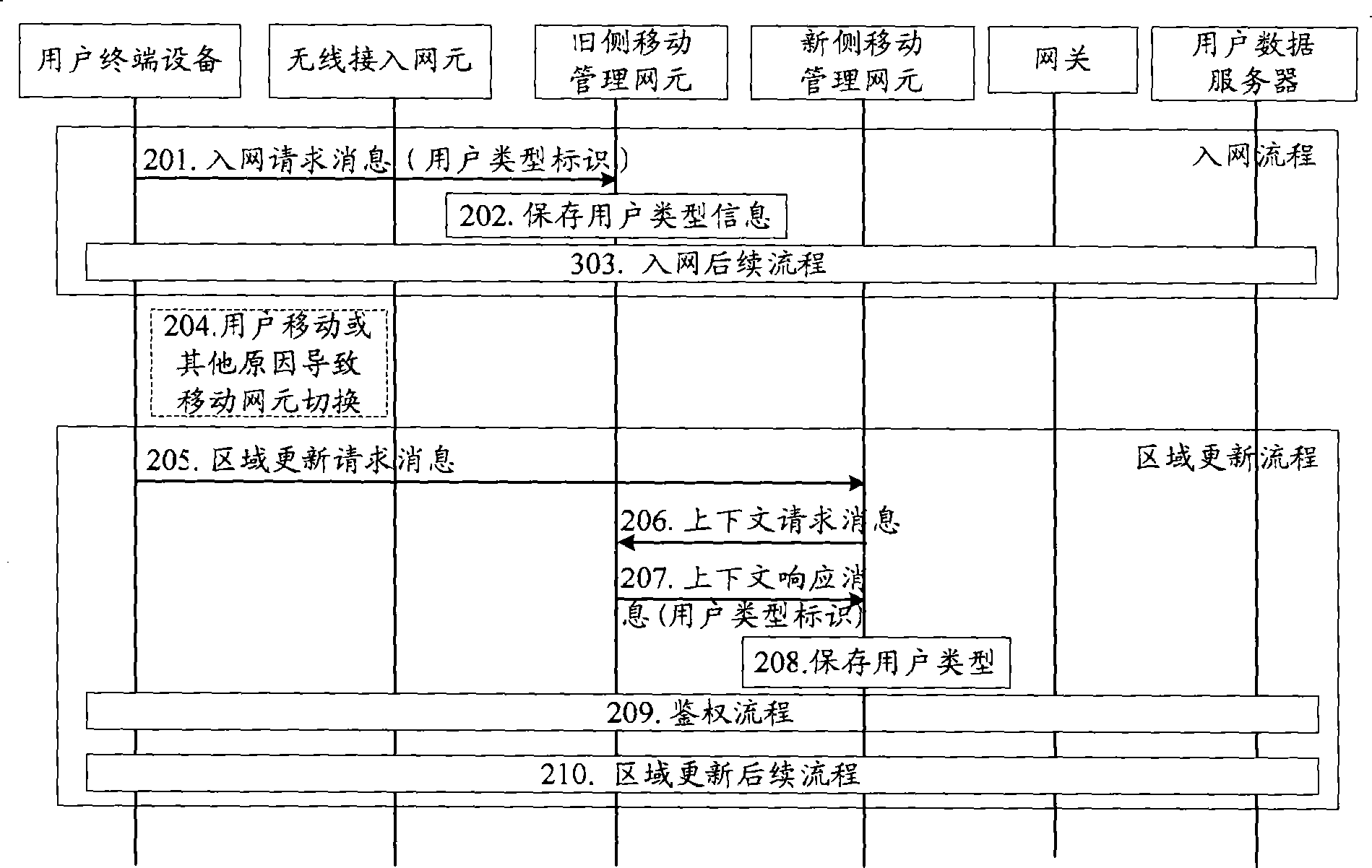
[0053] This embodiment describes that the old-side mobility management network element obtains the user type identifier by carrying the user type identifier in the network access request message sent by the user, and then the old-side mobility management network element replies to the context request message sent by the new-side mobility management network element, Carry the user type identifier in the context response message and send it to the mobility management network element on the new side.
[0054] Describe in detail below in conjunction with accompanying drawing, see figure 2 , the method of this embodiment may include the following steps:
[0055] Step 201: the user terminal equipment sends a network access request message to the old mobility management network element;
[0056] During the user's network access process, the user will send a network access request message to the old-side mobility management network element. The message carries the user type identifi...
Embodiment 3
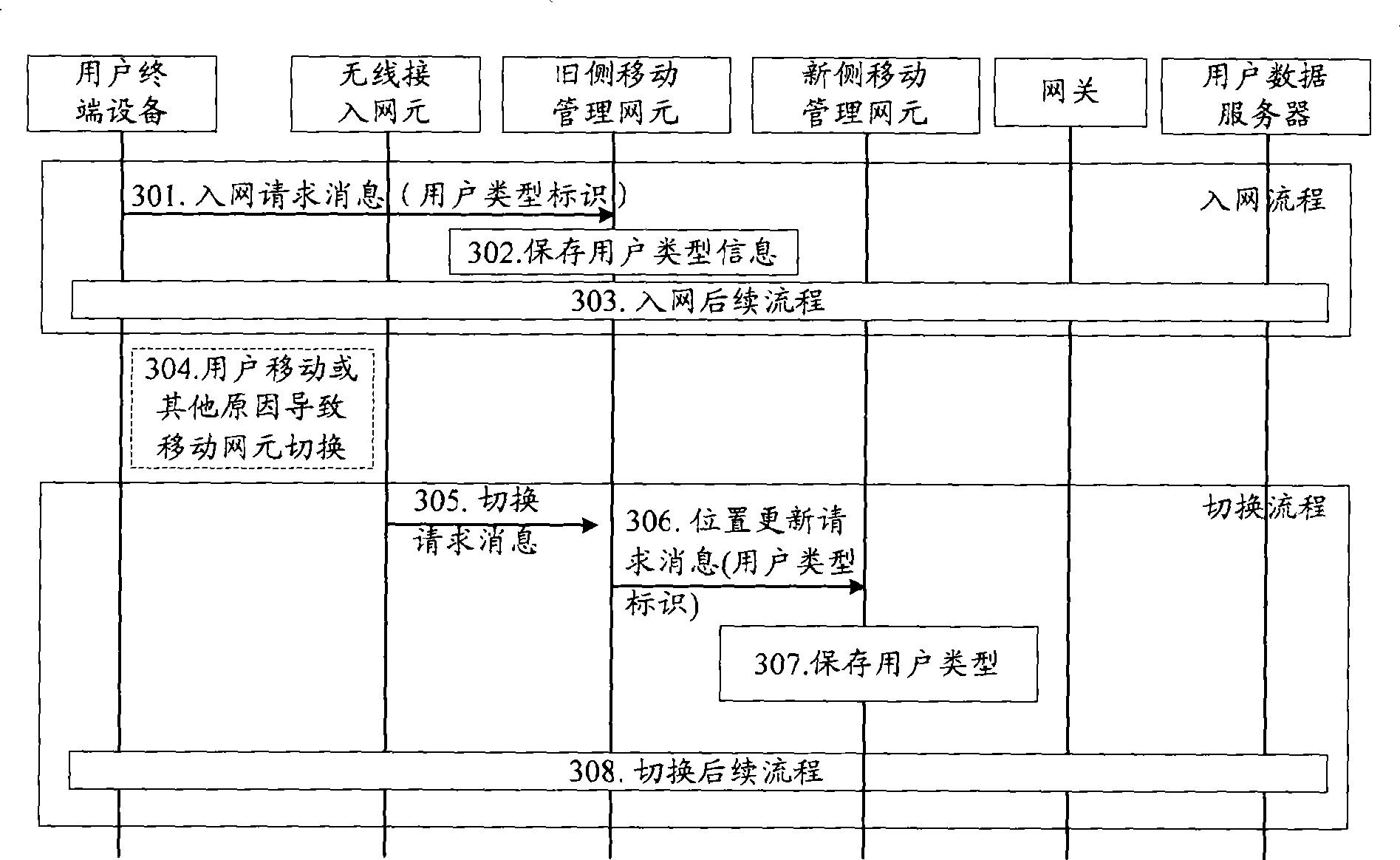
[0080] This embodiment describes that the old-side mobility management network element obtains the user type identifier by carrying the user type identifier in the network access request message sent by the user, and the new-side mobility management network element obtains the user type identifier from the old-side mobility management network element through the location update request message. Type identification and authentication methods.
[0081] Describe in detail below in conjunction with accompanying drawing, see image 3 , the method of this embodiment may include the following steps:
[0082] Step 301: the user terminal equipment sends a network access request message to the old mobility management network element;
[0083] During the user's network access process, the user will send a network access request message to the old-side mobility management network element. The message carries the user type identifier, such as SIM or USIM. This type can be a new cell or an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com