Firewall system based on virtual machine
A firewall and virtual machine technology, applied in the field of information security network access control, can solve the problems of firewall function shielding, misoperation or execution of Trojan horse programs, flexibility and security risks, etc., and achieve an easy-to-achieve effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings.
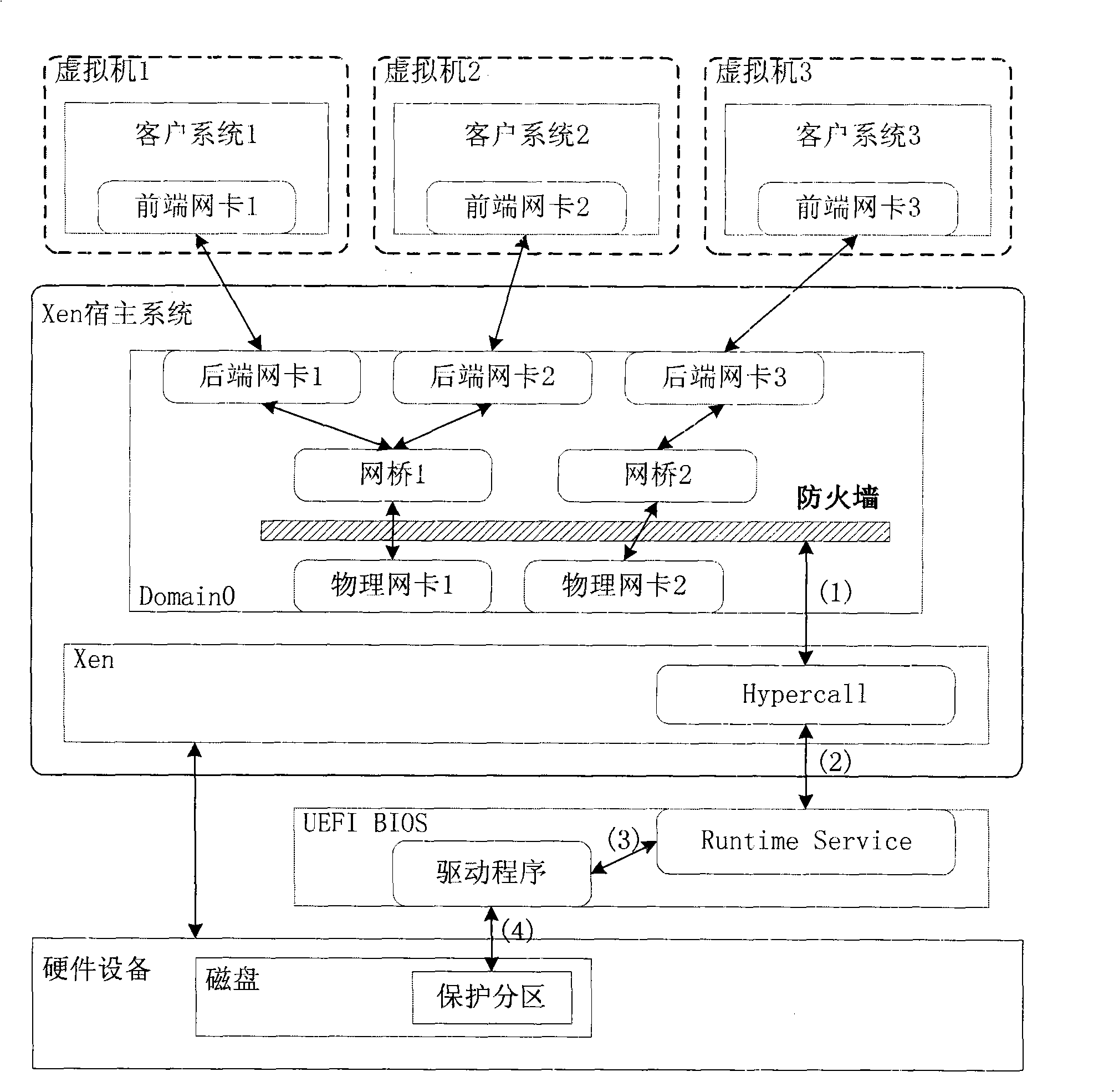
[0024] Such as figure 1 As shown, the major modules from bottom to top are: hardware device, BIOS, Xen host system and various client systems. Different from the traditional personal firewall, the firewall of the present invention is deployed in the Xen host system.
[0025] The Xen host system is the most important part of the system and consists of Xen and Domain0. Xen is a virtual machine monitor, which replaces the position of the operating system, directly interacts with hardware devices, and creates a virtual machine environment for the guest operating system to run. Domain0 is a Linux system running in the default virtual machine created by Xen, which is responsible for assisting Xen in managing other virtual machines. The back-end network card is the aforementioned virtual network card, which corresponds to the front-end network card in the client system one...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com