Method and apparatus for defending network attack
A network attack and priority technology, applied in the field of data communication, to reduce the impact and improve the ability to defend against network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The method of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments of the present invention.
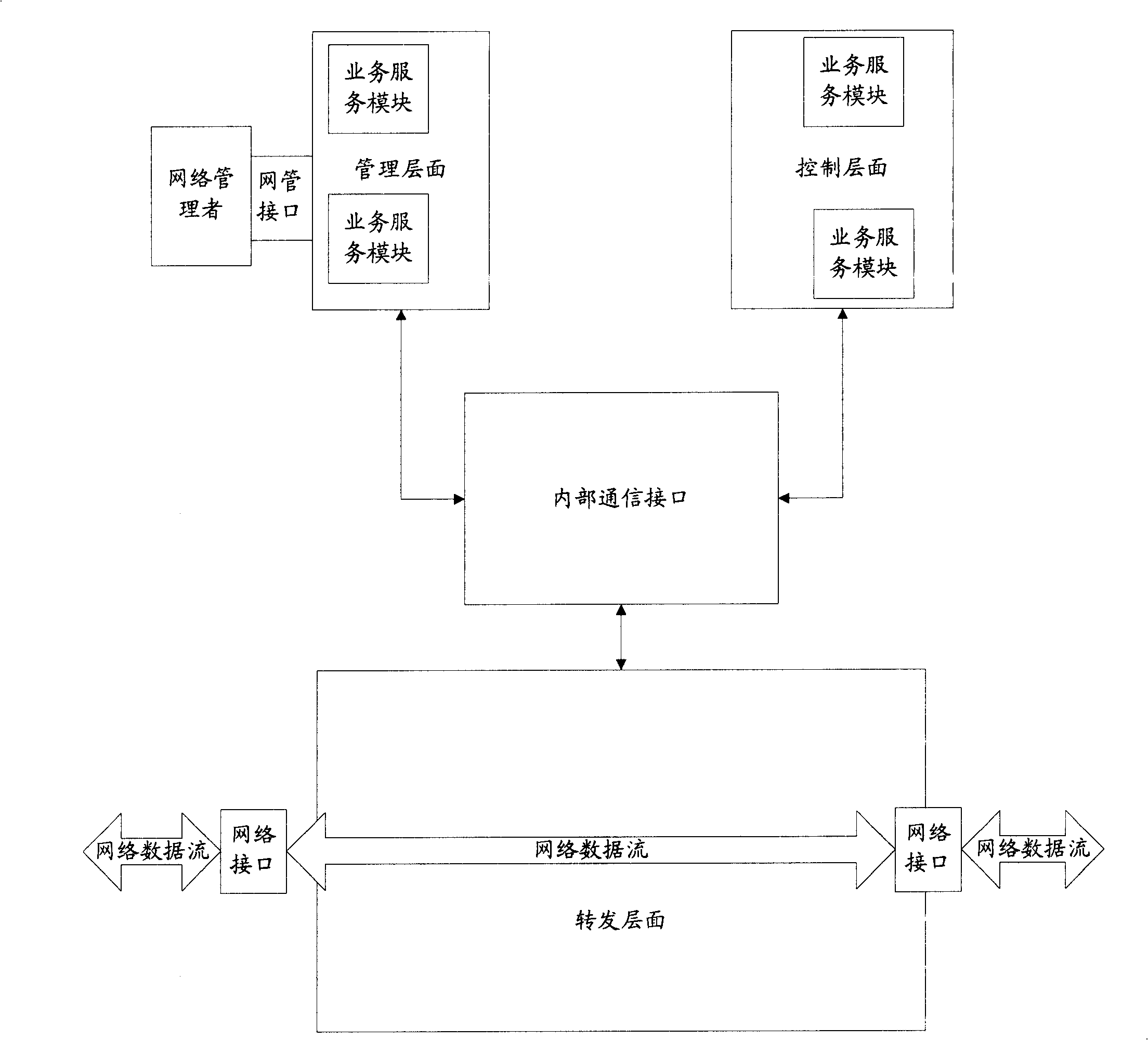
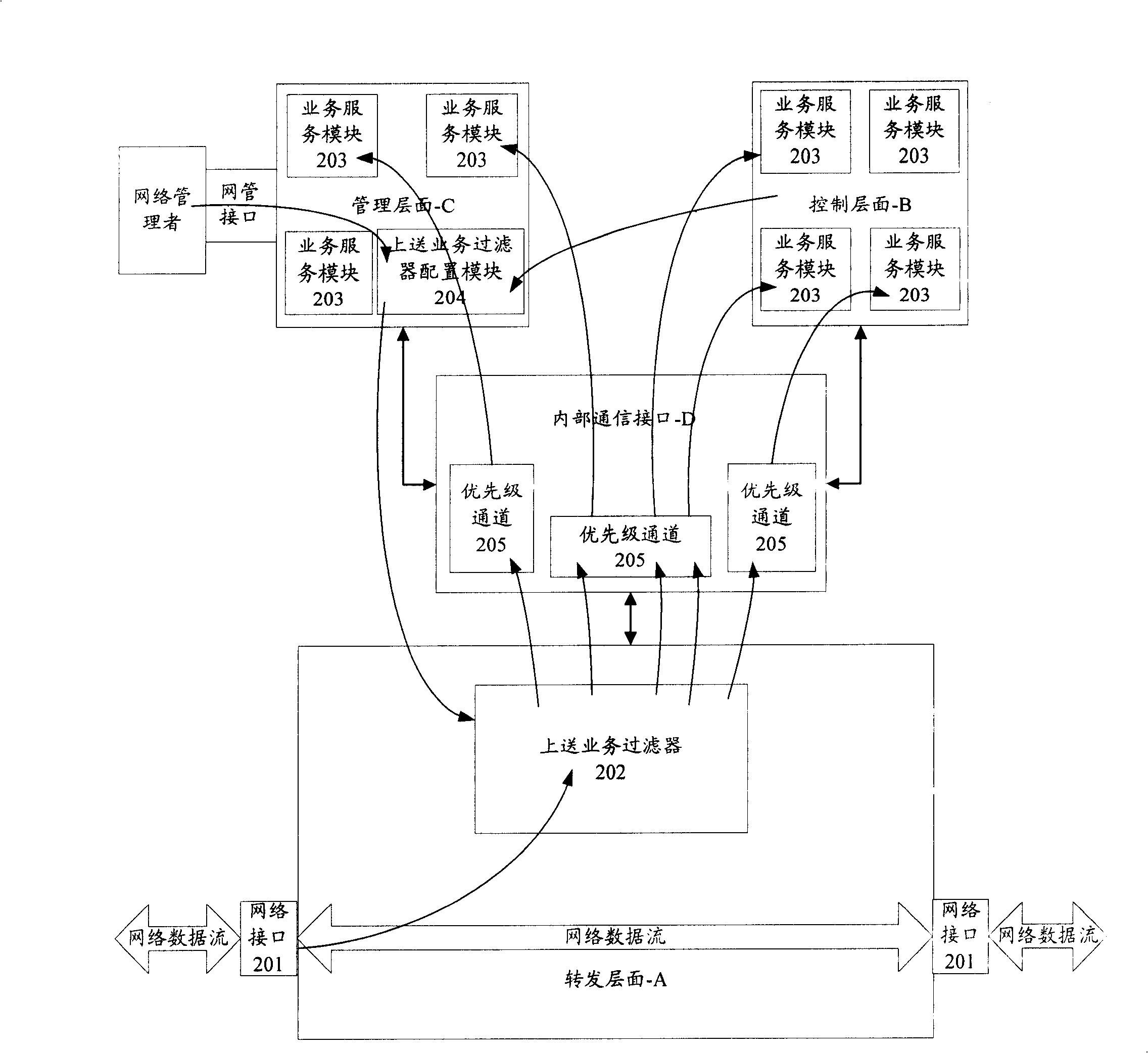
[0035] figure 2 It is a schematic diagram of the functional structure and working process of the network equipment in the embodiment of the present invention, such as figure 2 As shown, the network device includes three processing layers: forwarding layer-A, control layer-B, and management layer-C, and an internal communication interface-D; the forwarding layer-A includes a network interface 201, an upload service filter 202 ; The control plane-B includes a plurality of different business service modules 203; the management plane-C includes a plurality of business service modules 203 and an upload service filter configuration module 204; the forwarding plane-A passes an internal The communication interface-D communicates with the control plane-B and the management plane-C respectively for data communic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com