Network node scanning detection method and system for LAN environment
A network node, scanning detection technology, applied in the field of computer networks, to achieve the effect of reducing accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
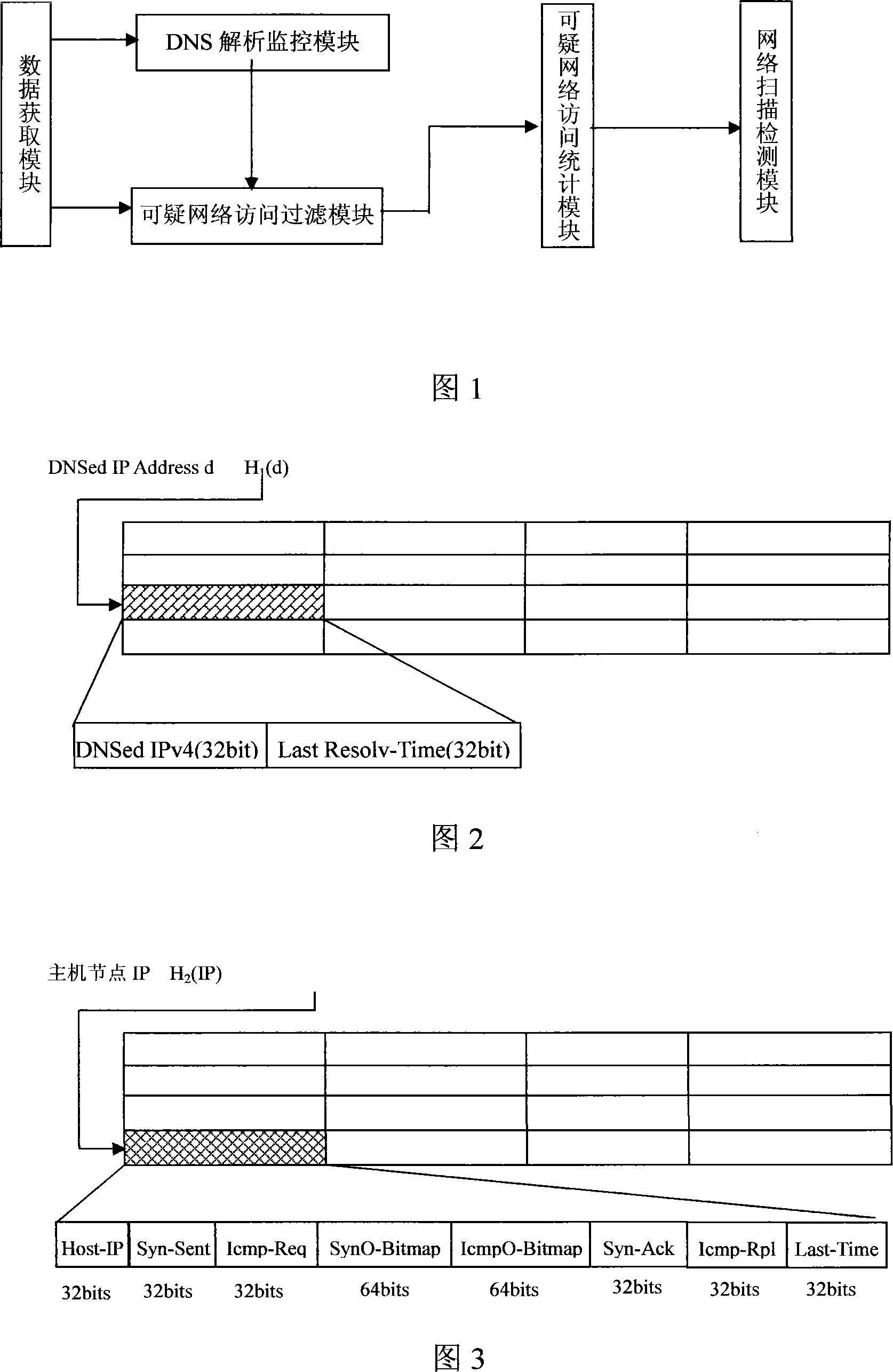
[0021] This embodiment is a network node scanning detection method suitable for a local area network environment. FIG. 1 is a schematic diagram of a system used in the method of the present invention.
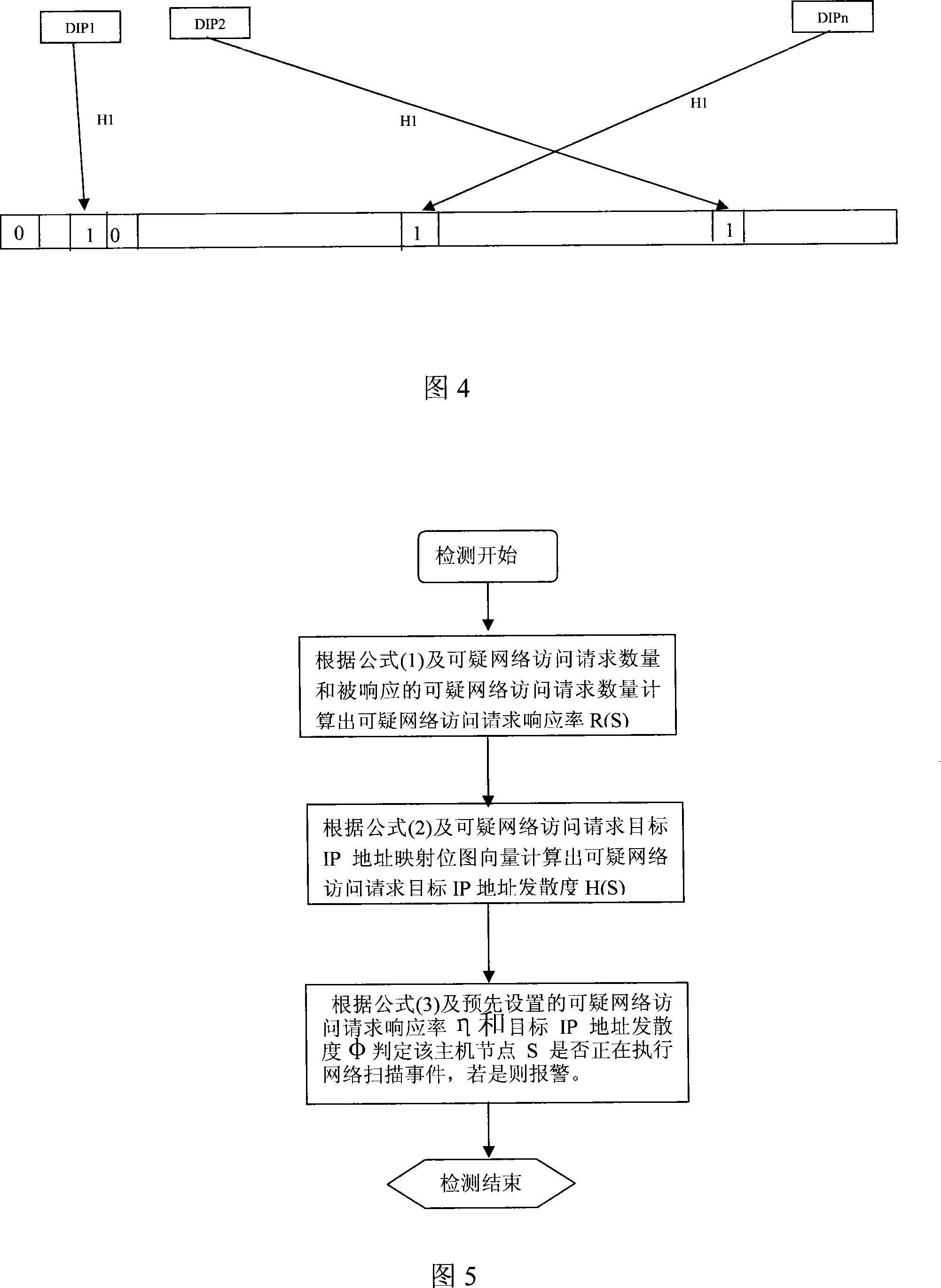
[0022] The basic idea of this embodiment is that detecting network scanning events can be distinguished from the context of network access behavior sequences. There is a difference between the network access traffic sent by the network scanning host node and the network access traffic sent by the normal network access host node: under normal circumstances, when a normal network access node sends out a normal outbound network access attempt, it will first send a The DNS (Domain Naming System, domain name resolution system) resolution operation related to the target IP address of an outbound network access; and a network scanning access issued by a network scanning host node, its related target IP address is randomly constructed, so there is no The DNS resolution operation rela...
Embodiment 2
[0030] This embodiment is a refinement of Embodiment 1, and is about the preferred scheme of the data acquisition step. The data acquisition module first collects all data packets on the local area network. After the data acquisition module captures network data packets, it needs to divide these network data packets into three categories:
[0031] 1) Network data packets related to DNS domain name resolution, where the network data packets are marked with TCP or UDP port 53, and this type of network data packets will be forwarded to the DNS resolution monitoring module for further analysis.
[0032] 2) network data packets related to the network access request and response sent by the host node, the present embodiment only considers TCP-SYN, TCP-SYN-ACK, ICMP-Request and ICMP-Reply type messages, and this type of network data packets will Forward to the suspicious network access filtering module in the background.
[0033] 3) other network data packets, this type of network ...
Embodiment 3
[0038] This embodiment is a refinement of Embodiment 1, and is about an optimal solution for DNS resolution monitoring steps.
[0039] This step receives all network data packets related to the DNS domain name resolution protocol from the data acquisition module, performs DNS protocol resolution on them, extracts the list of IP addresses resolved by the DNS domain name, and dynamically maintains a data cache about these IP address lists.
[0040] When the DNS resolution monitoring module caches the list of IP addresses resolved by the DNS domain name, it also records the latest DNS resolution time of each IP address, adopts a fast hash table structure, and uses the IP address as an index to index all DNS domain names. IP addresses and their associated resolution times are stored into a fast hash table.
[0041] The network data packets related to the DNS domain name resolution protocol can be divided into two types: DNS domain name resolution request data packets and DNS domai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com