Monitoring system, apparatus and method in IP network
A technology of network equipment and IP network, which is applied in the field of communication, can solve problems such as the impact of existing functions of network elements, and achieve the effects of improving networking flexibility, having mobility, and reducing transformation and impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
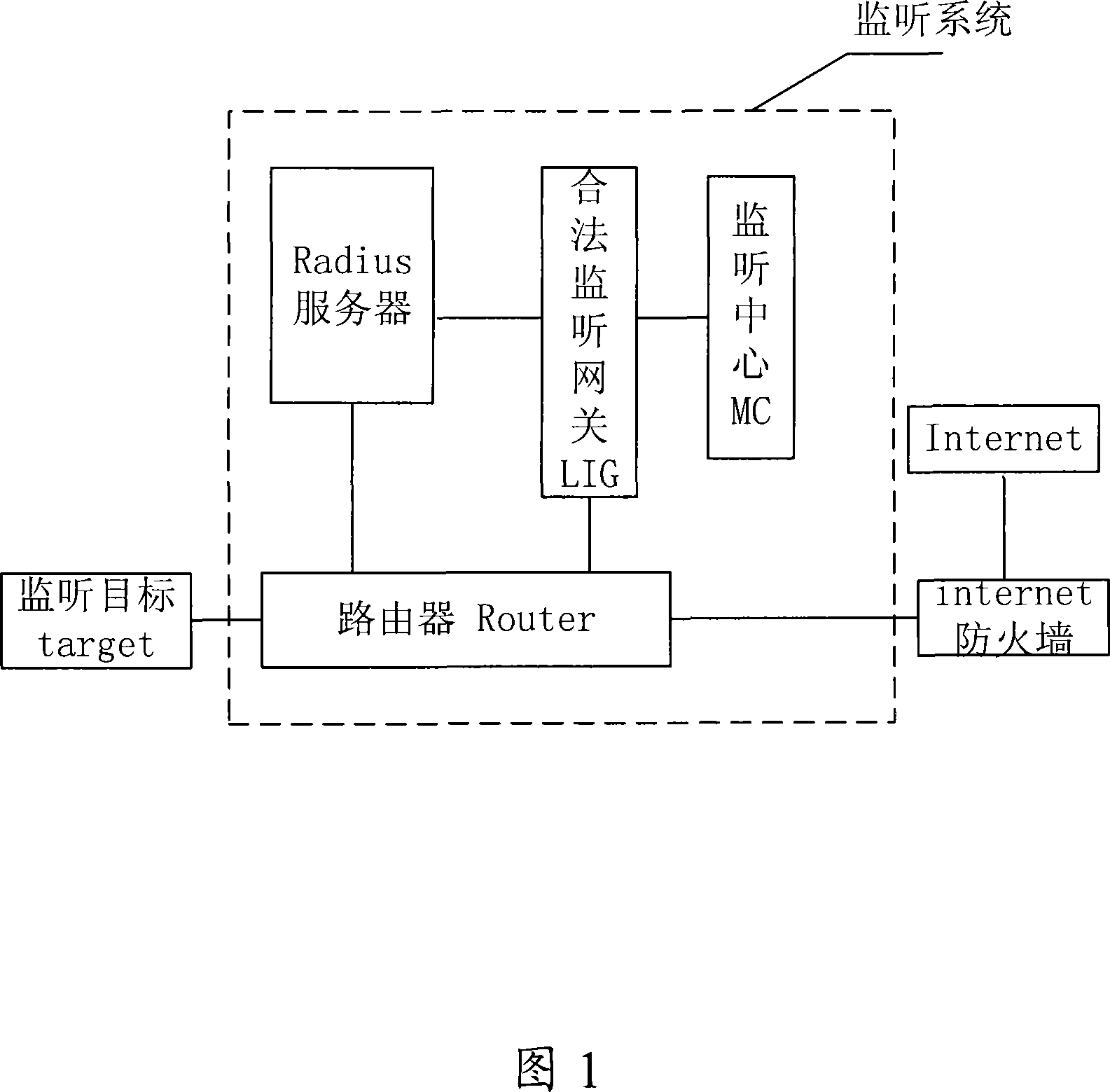
[0060] In conjunction with the foregoing embodiments, the first embodiment of the present invention provides a monitoring system in an IP network. In this embodiment, the network device is a router. With reference to FIGS. 3 and 4 , the specific working process of the monitoring system is as follows:
[0061] The Radius server receives the user's authentication and accounting request message forwarded by the router, and performs authentication and accounting for the user;
[0062] The LIG sends a monitoring command to the filtering rule processing module of Analysis TAP, and the monitoring command carries information related to setting monitoring filtering rules;
[0063] The filtering rule processing module receives the monitoring command issued by the LIG, and sets the monitoring filtering rule according to the relevant information of the setting monitoring filtering rule carried by the monitoring command, wherein the monitoring command issued by the LIG includes the filterin...
Embodiment 2
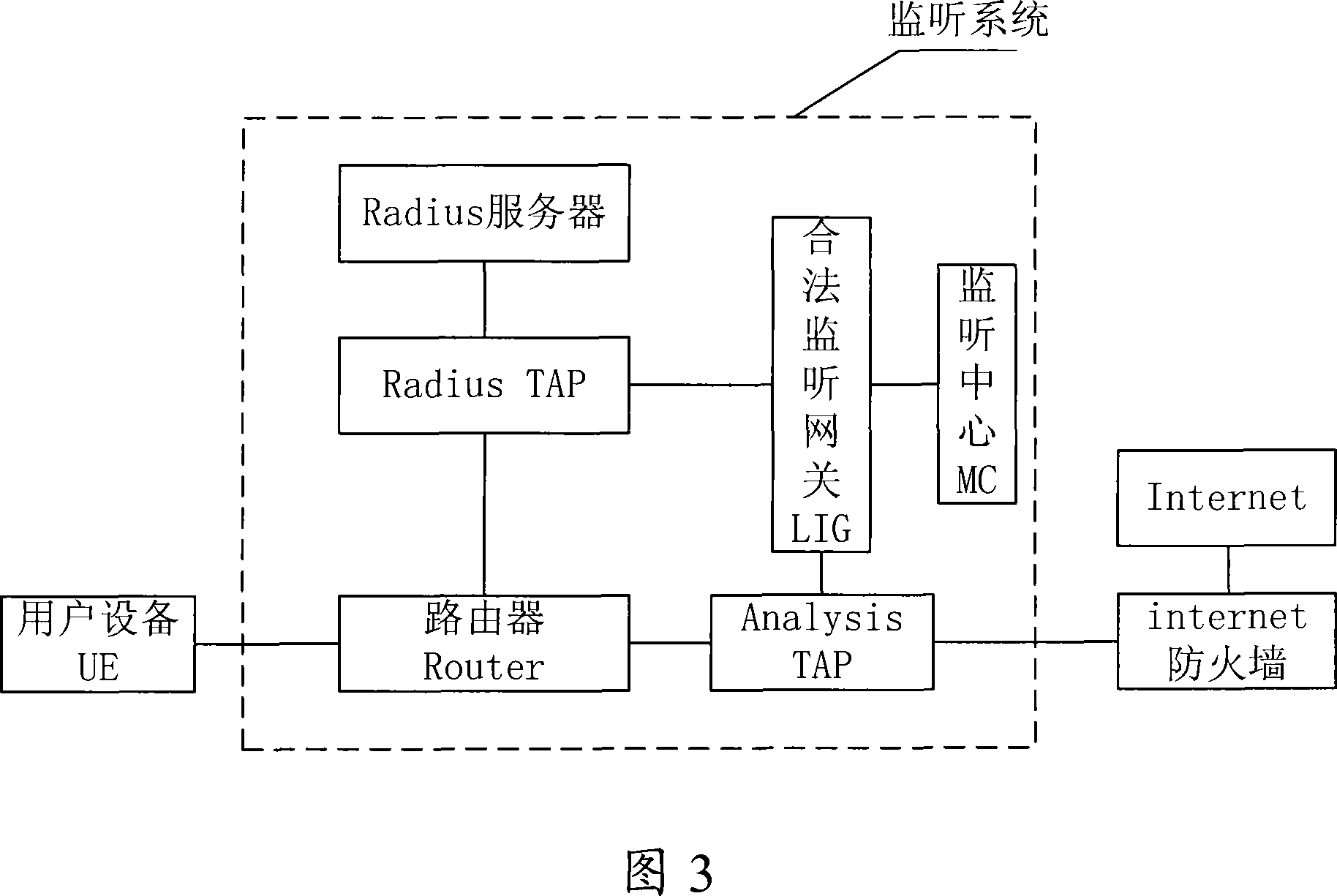
[0073] In combination with the above-mentioned embodiments, the second embodiment of the present invention provides another monitoring system in an IP network. The difference from the first embodiment is that the monitoring system of this embodiment further includes: a message analysis unit Radius TAP, the monitoring system The specific working process is as follows:
[0074] The Radius server receives the user's authentication and charging request message forwarded by the network device router, and performs authentication and charging for the user;
[0075] Radius TAP, intercepting the Radius message that the router and the Radius server interacts and analyzing, determining the monitoring target and obtaining the address information of the monitoring target, specifically, the Radius message includes: the authentication request message sent by the user equipment to the Radius server and the Radius server sending The authentication response message returned by the user;
[007...
Embodiment 3
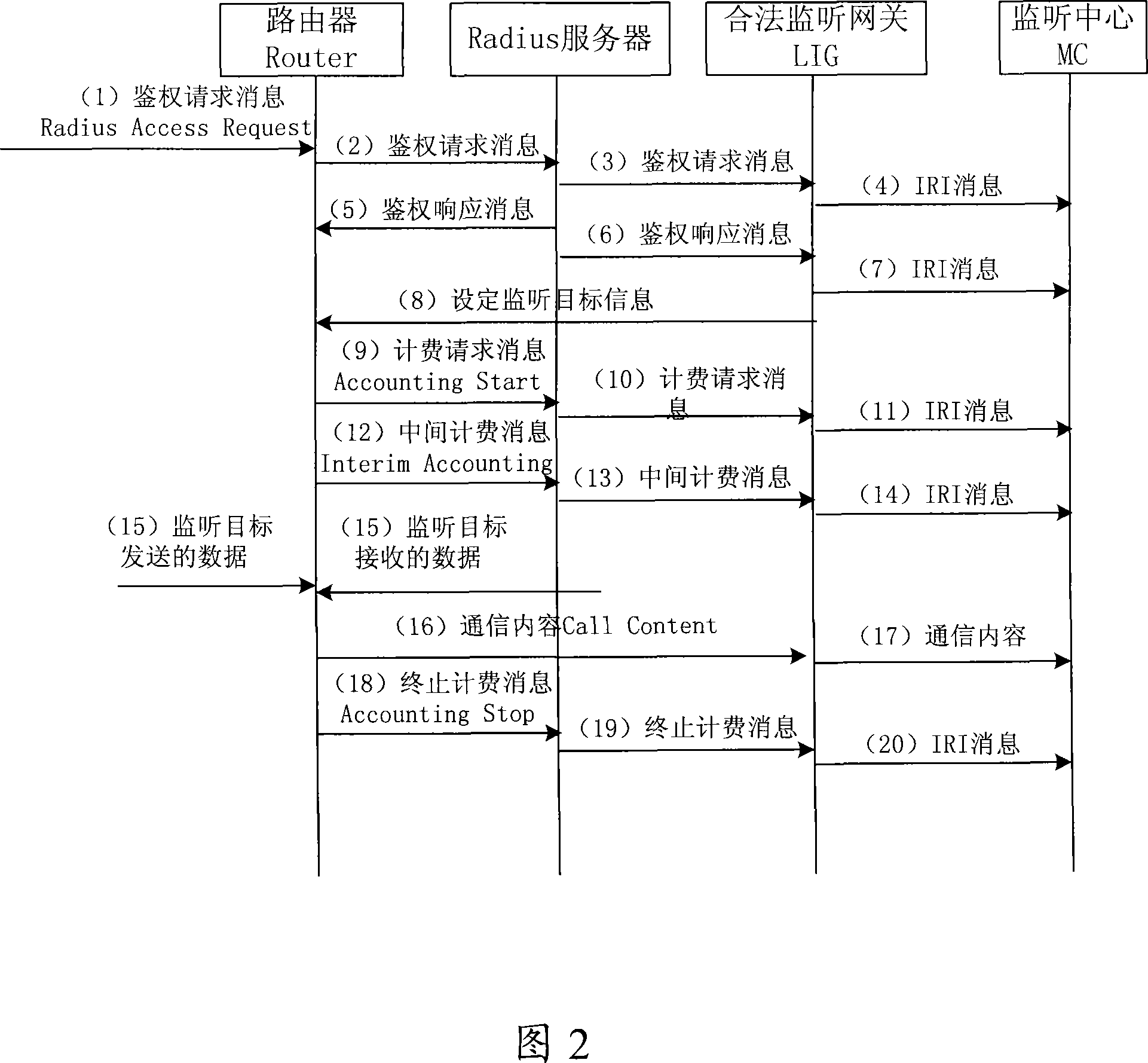
[0086] At the same time, the third embodiment of the present invention also provides a method for realizing monitoring in an IP network, and the specific process is as shown in Figure 5:
[0087] Step 1. The user equipment UE initiates a login, and sends a request message Radius Access Request to the router Router requesting to log in to the remote dial-in user authentication server;
[0088] Step 2, the router receives the request message, and sends an authentication request message to the Radius server;
[0089] Step 3, the analysis unit Radius TAP intercepts the authentication request message, and through analysis, it is known that the user information carried in the message is consistent with the monitoring target user information pre-configured in the Radius TAP, then it is determined that the user equipment is the monitoring target, And send an authentication request IRI message Access Request IRI to the legal interception gateway LIG;
[0090] Specifically, the user in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com