Tree traversal method and device
A table entry and traversal technology, applied in the direction of data exchange, digital transmission system, electrical components, etc. through path configuration, can solve problems such as message channel blockage, business abnormality, long processing time, etc., to avoid timeout, improve traversal efficiency, Guaranteed to work properly
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
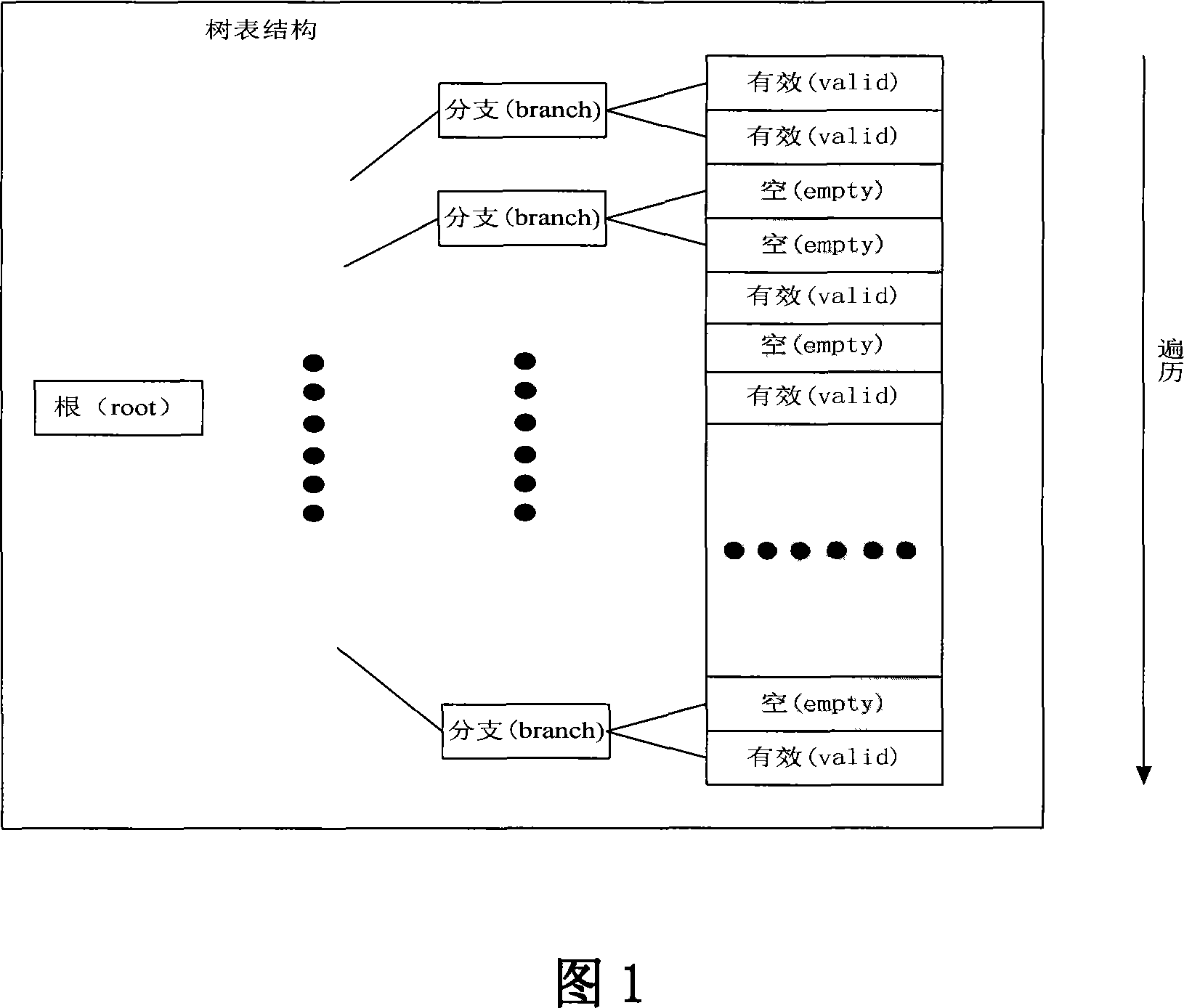
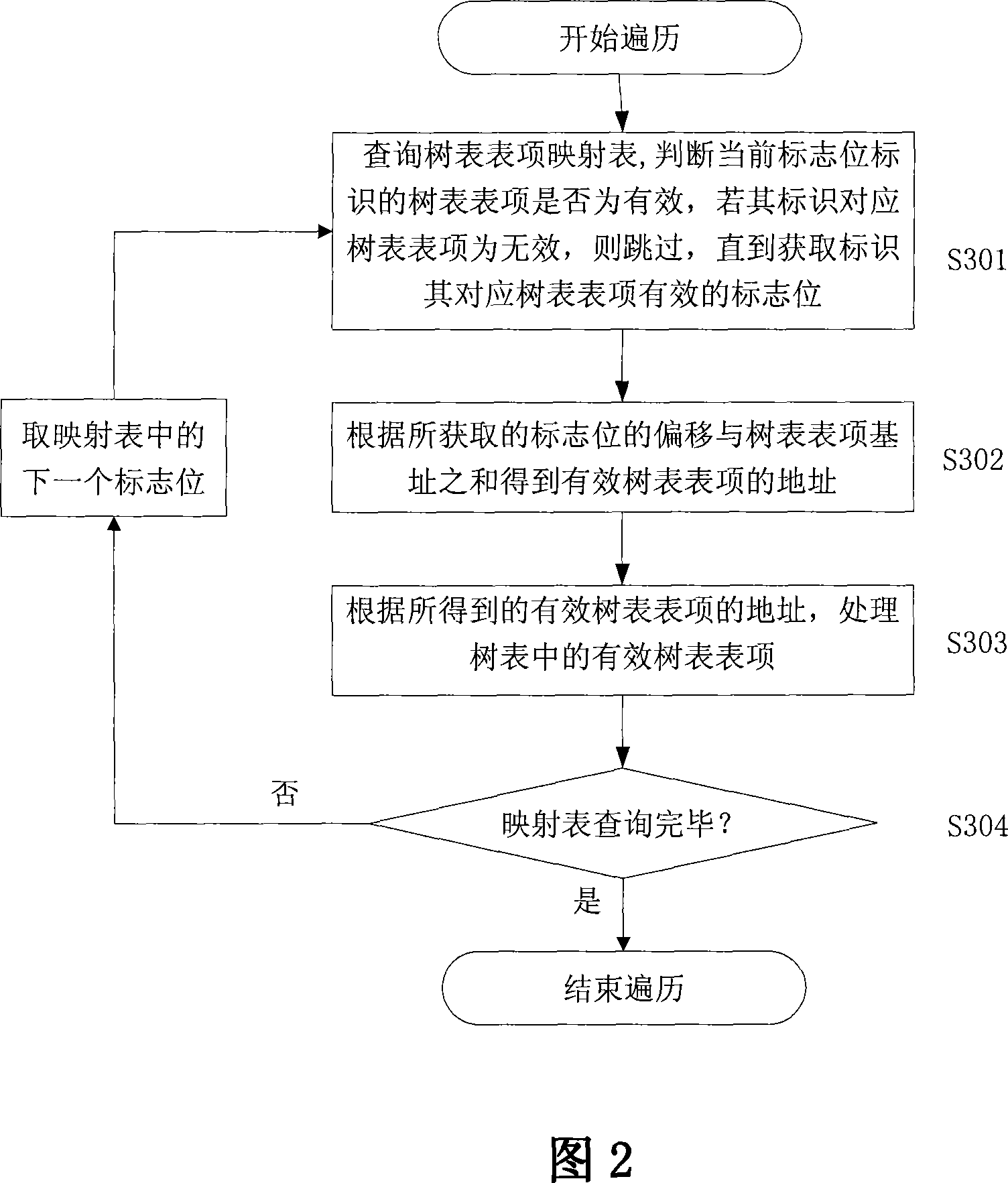
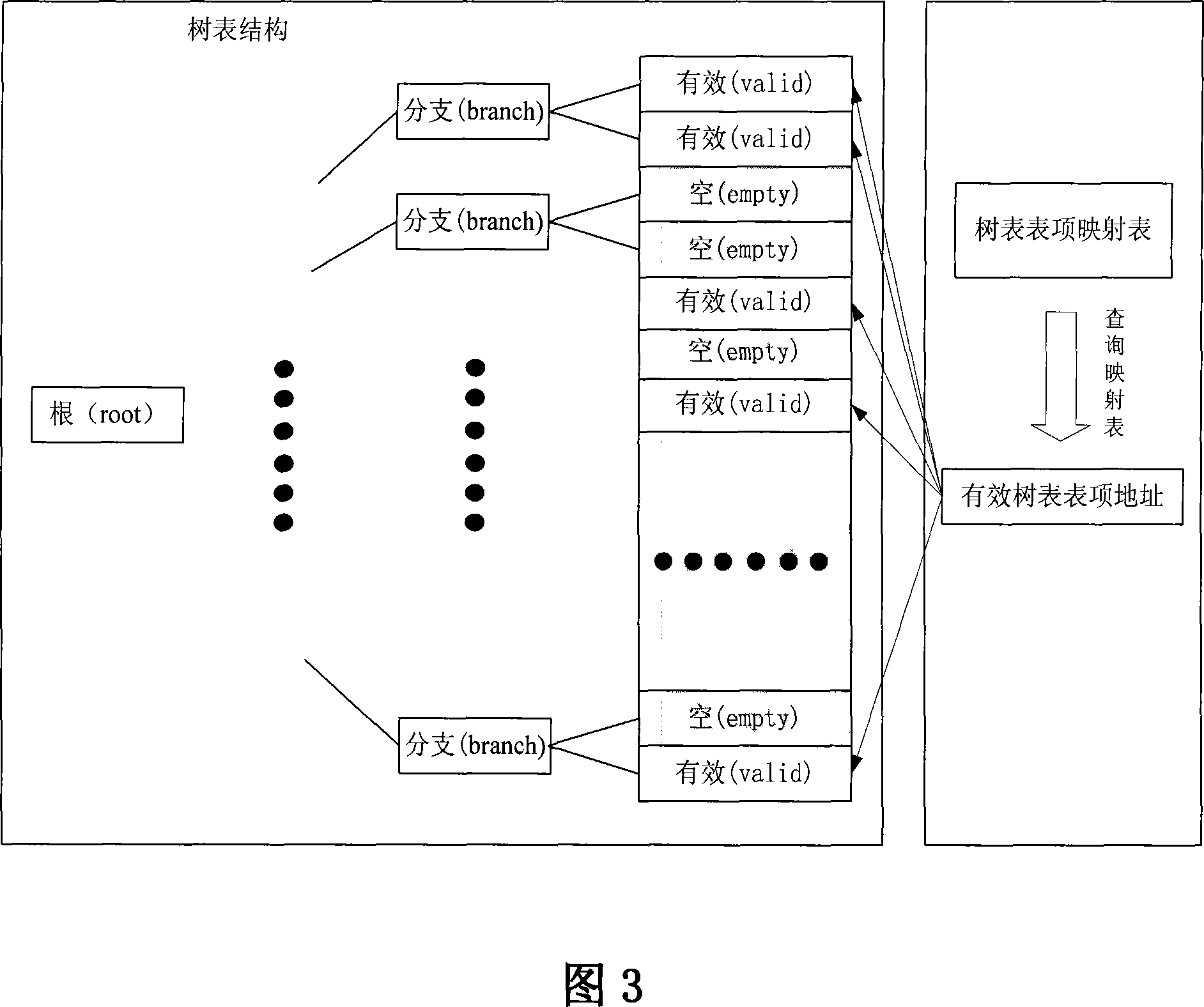
[0038] The method for traversing the tree table entries of the network processor in the embodiment of the present invention is to establish a tree table entry mapping table of the pre-traversal tree table in the network processor in advance, and the mapping table is set in a one-to-one correspondence with the tree table entries of the tree table Flag bit, each flag bit identifies whether its corresponding tree table entry is valid (for example, if the flag bit is 1, its corresponding tree table entry is valid, and if it is 0, its corresponding tree table entry is invalid), that is, to identify its corresponding tree table entry The table entry is a valid tree table entry or an invalid tree table entry; the network processor obtains the valid tree table entry by identifying the valid flag bit of the corresponding tree table entry in the tree table entry mapping table The address of the item.
[0039] In this embodiment, the flag bits of the tree table entry mapping table corres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com