Method and device for detecting scanning attack
A technology for detecting scanning and equipment, which is applied to detecting scanning attack equipment, detecting scanning attack equipment based on monitoring the number of attacks within a certain period of time, detecting scanning attacks, and detecting scanning attack areas based on monitoring the number of attacks within a certain period of time, It can solve problems such as high complexity and high time precision requirements, and achieve the effect of reducing difficulty, simple implementation method and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] see Figure 4 , before describing each embodiment of the present invention in detail, it is necessary to briefly explain the format of the ICMP address unreachable message: usually, an ICMP address unreachable message contains Figure 4 The content of each message shown:
[0033] IP packet header, including: source IP address (SIP) and destination IP address (DIP);
[0034] ICMP message header, for the unreachable message, its type (Type) value is 3; when the code (Code) value is 2, 3, it indicates that the protocol is unreachable and the port is unreachable respectively;
[0035] Original IP packet header, including: original source IP address (O_SIP), original destination IP address (O_DIP) and original protocol (O_Protocol);
[0036] The original IP UDP message header, including: the source port (O_SPORT) and destination port (O_DPORT) of the original IP message.
[0037] Embodiments of the first aspect:
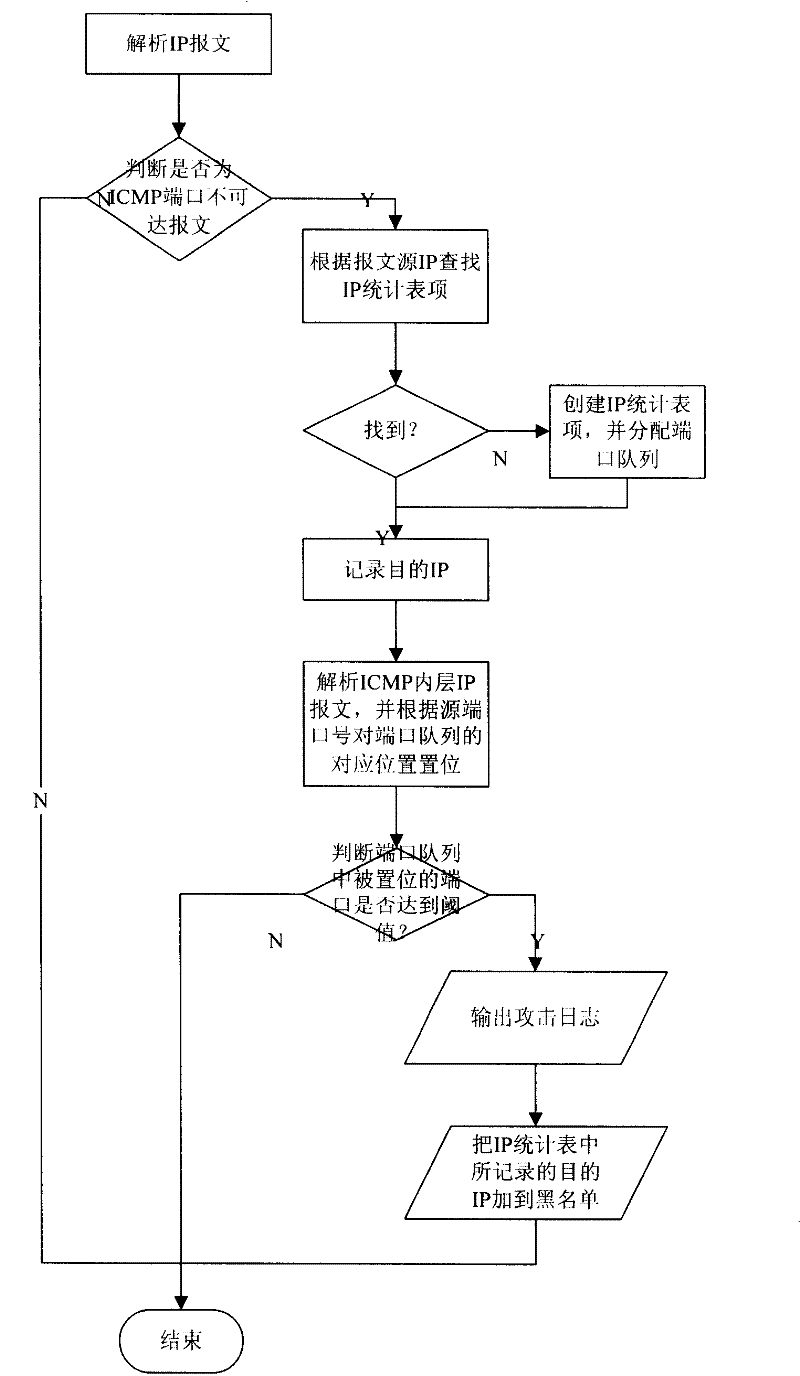
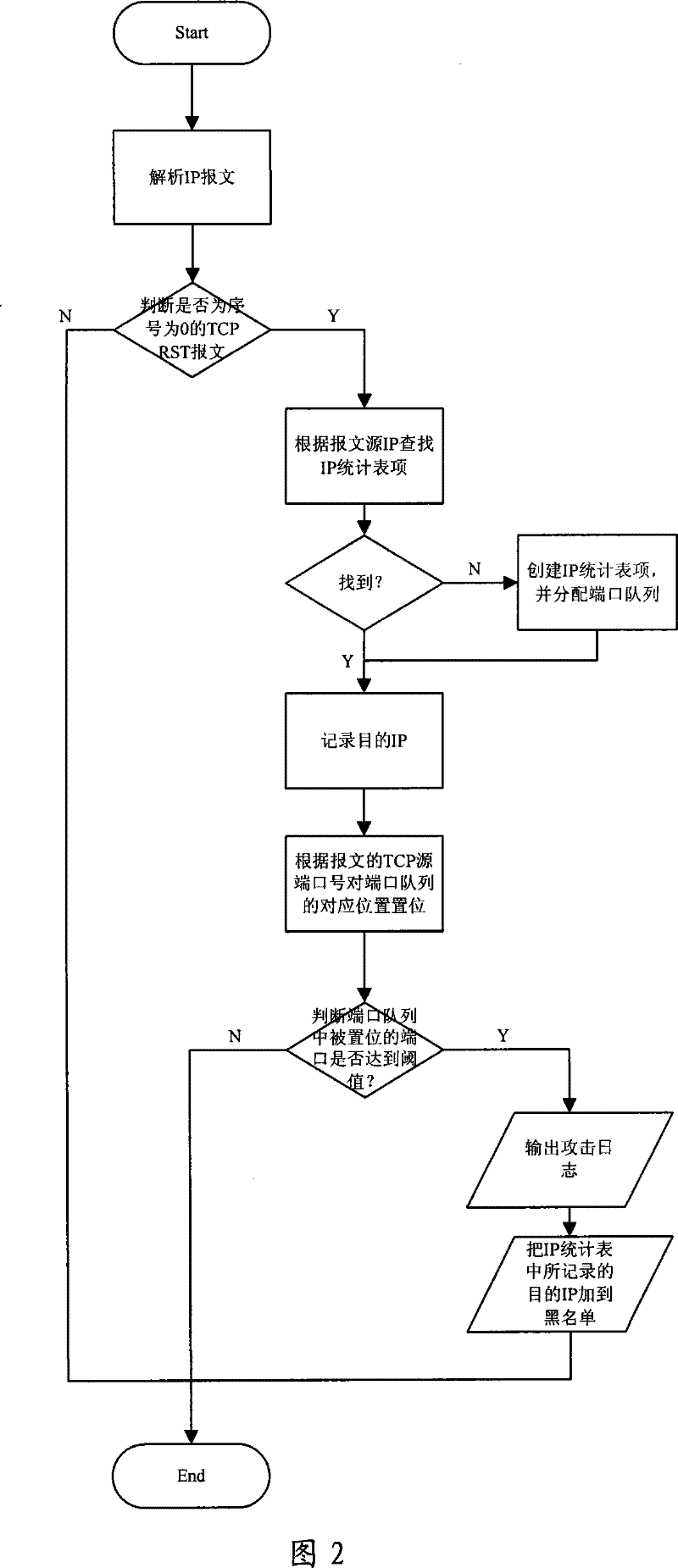
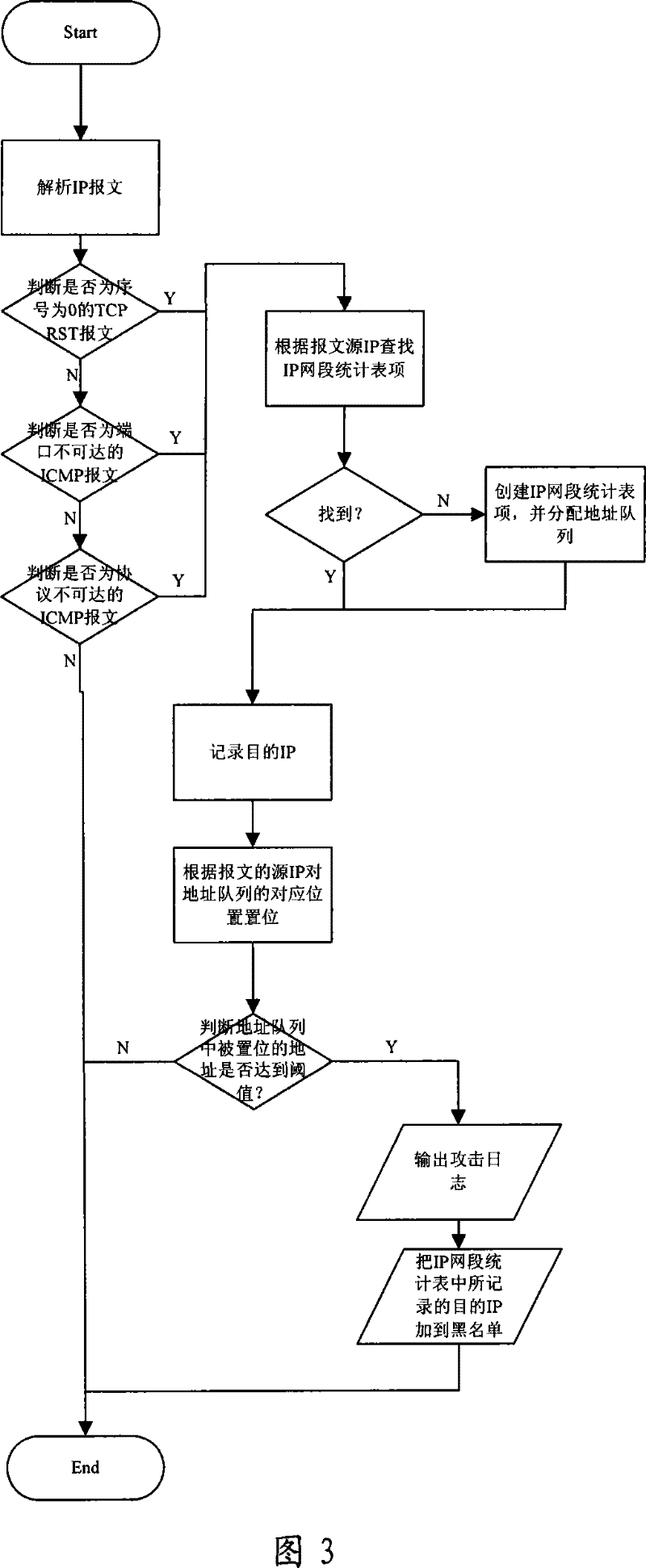
[0038] see figure 1 , which is an example of a detection m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com