Two-factor content protection
A technology of content and protection function, applied in the field of protecting the content stored in the first device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In the following detailed description, numerous specific details are set forth in order to provide a thorough understanding of the embodiments. However, one of ordinary skill in the art would understand that the embodiments may be practiced without these specific details. In other instances, well-known methods, procedures, components, and circuits have not been described in detail so as not to obscure the embodiments.
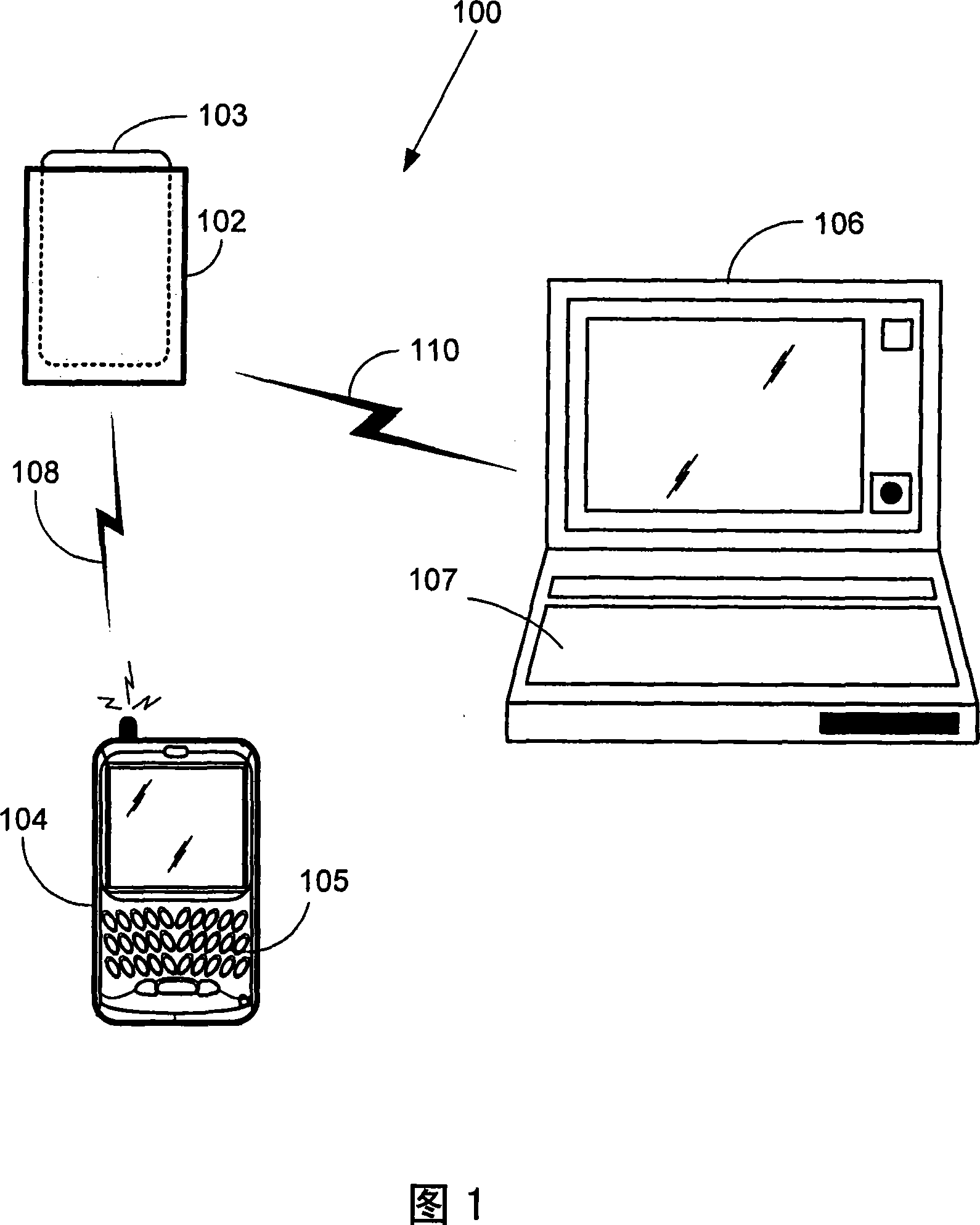
[0016] Figure 1 is a schematic diagram of an example system including an authentication device, according to some embodiments of the invention. System 100 includes personal computer 106 , smart card reader 102 and mobile device 104 . Smart card 103 is shown inserted in smart card reader 102 . The mobile device 104 includes a user input interface 105 and the personal computer 106 includes a user input interface 107 .
[0017] It is desirable to apply content protection to personal computers 106 and / or mobile devices 104 . Personal computer 106 and sma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com