Method, system and apparatus for realizing loop protection
A technology of ring network and sub-ring, applied in the field of realizing ring network protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
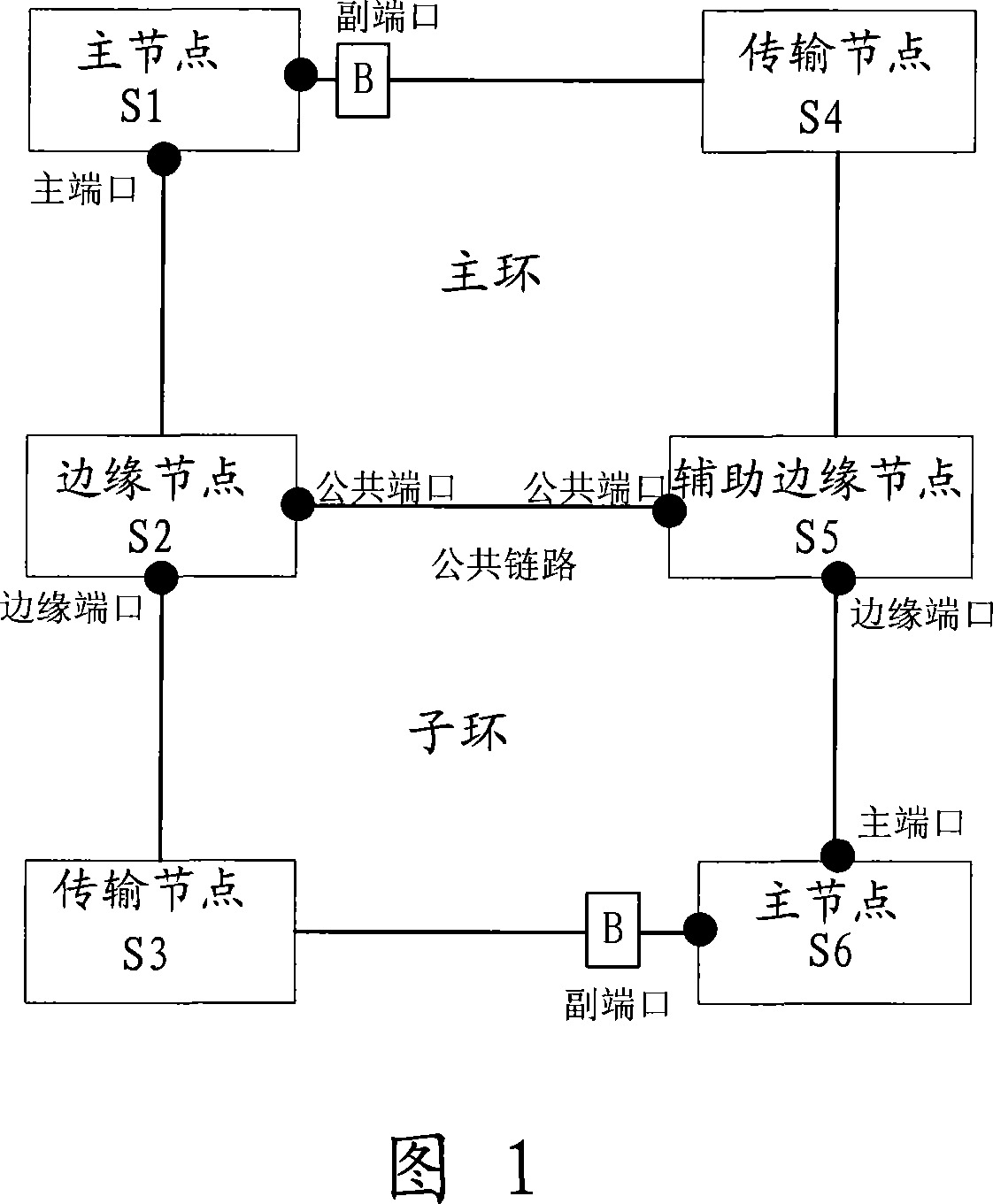
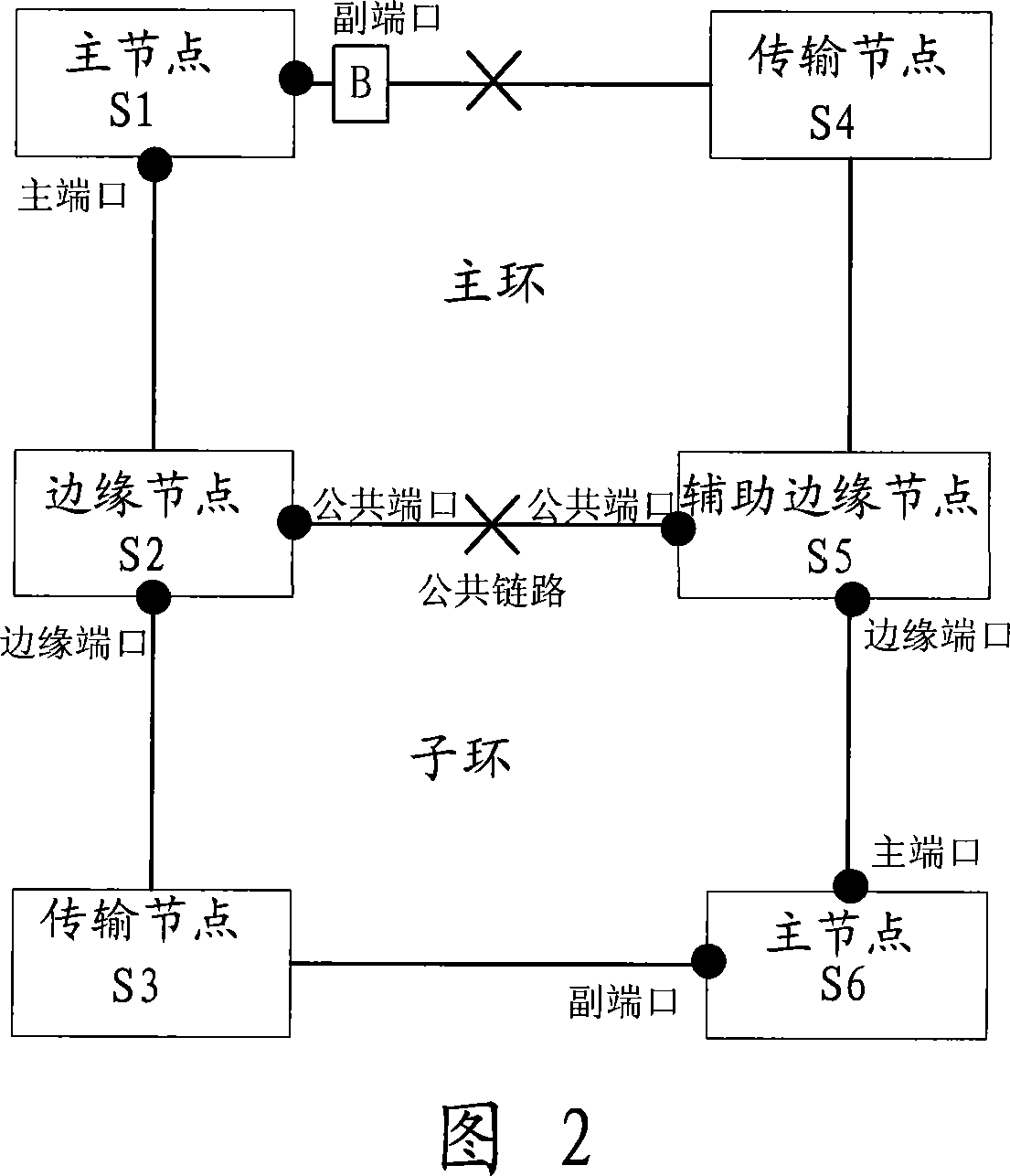
[0049] As shown in Figure 2, the RRPP protocol packets of the subring need to be transmitted between the edge nodes and the edge ports of the auxiliary edge nodes through the channel provided by the main ring, as if the entire main ring is a logical node on the subring, and the subring RRPP protocol packets are transparently transmitted through the main ring. When the sub-ring protocol message channel on the major ring is interrupted (that is, the public link between the major ring and the sub-ring fails, and more than one non-public link fails), after the master node sends a health detection message (HELLO), the Start the FAIL timer, because within the time specified by the FAIL timer, the master node of the sub-ring will not receive the HELLO message sent by itself, so the FAIL timer expires, and the master node of the sub-ring releases the secondary port.
Embodiment 2
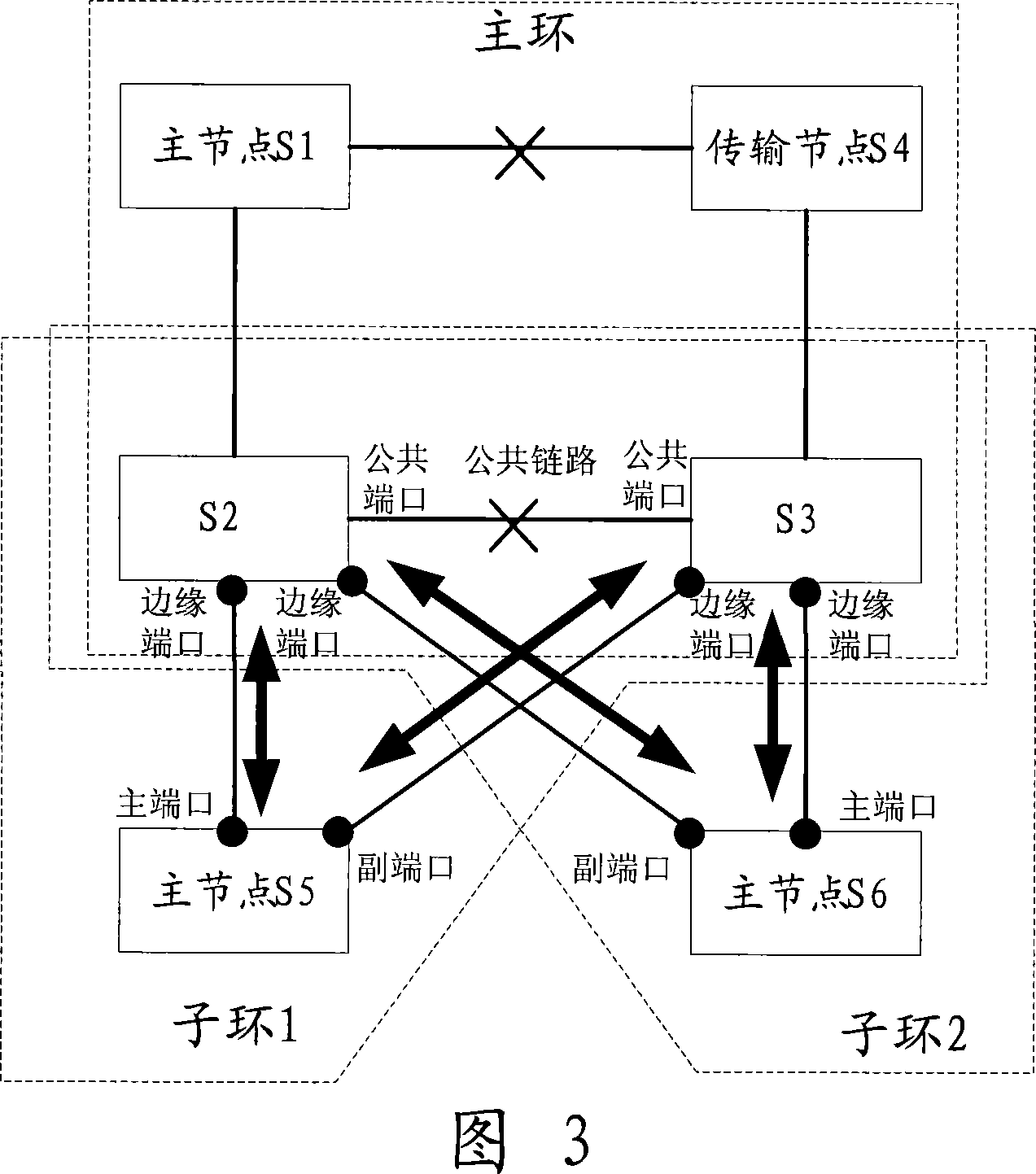
[0051] For the common networking shown in Figure 2, broadcast loops can be avoided. However, for the dual-homing network commonly used in actual networking shown in Figure 3, there are three ring networks in Figure 3, one of which is the main ring, and two are sub-rings, namely sub-ring 1 and sub-ring 2. Among them, sub-ring 1 is composed of main node S5, edge node S2 and auxiliary edge node S3. On sub-ring 1, we can assume that S2 is an edge node and S3 is an auxiliary edge node; Composed of S2 and edge node S3 (here, it is assumed that node S2 and node S3 have different roles in the two sub-rings, so that the subsequent diagram can more clearly show the effect of edge port being blocked. In fact, node S2 and node S3 Whether the roles in each sub-ring are the same does not affect the implementation of the embodiment of the present invention). Dual-homing sub-ring 1 and sub-ring 2 are connected to each other through nodes S2 and S3, forming a ring. When the sub-ring protocol ...
Embodiment 3
[0067] The embodiment of the present invention also provides a system for realizing ring network protection. The system includes N intersecting ring networks (N is a natural number greater than or equal to 2), one of which is a main ring, and N-1 is a sub-ring. There is one and only one master node in each ring network. The main port of the master node forwards data packets and protocol packets. When the secondary port is blocked, only protocol packets are forwarded. Each sub-ring intersects with the main ring at two nodes, respectively. is the edge node and the auxiliary edge node, and the edge node and the auxiliary edge node are directly connected,
[0068] When the auxiliary edge node detects that the sub-ring protocol message channel on the main ring is interrupted, it notifies the edge node of the sub-ring that the sub-ring protocol message channel on the main ring is interrupted;
[0069] The edge node, after receiving the notification from the auxiliary edge node, bloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com