Associative attack analysis and detection method and device based on the time sequence and event sequence
A technology of correlation analysis and time series, which is applied in the direction of secure communication devices, electrical components, digital transmission systems, etc., can solve the problem of not considering the attack time series characteristics and event sequence characteristics at the same time, the attribution relationship of attack events cannot be accurately distinguished, and the attack cannot be realized Comprehensive and accurate description of problems, to achieve the effect of accurate detection, accuracy assurance, and diversification of associations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
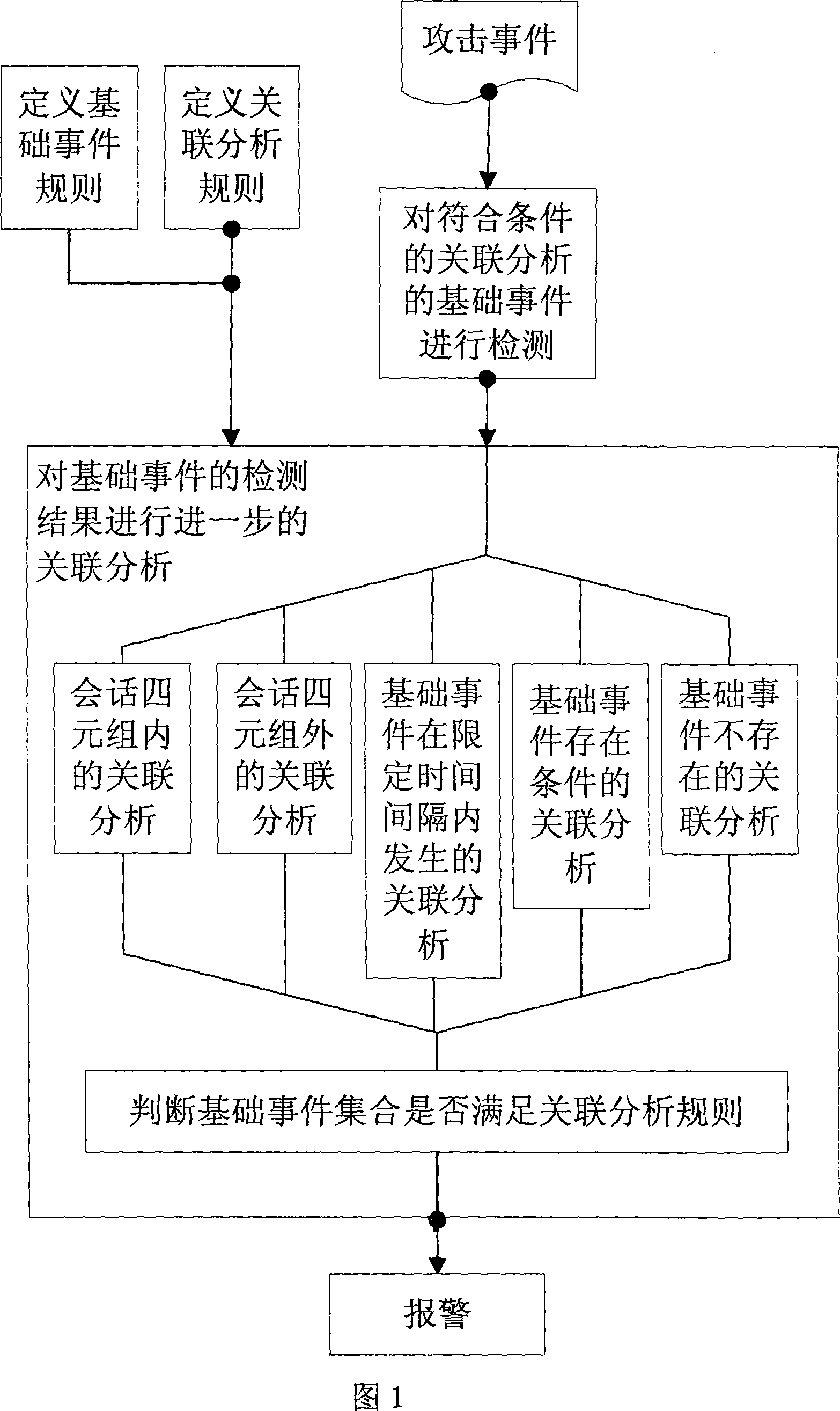
[0051] First define the nouns used in this patent:
[0052] Single attack event——an attack event detected by feature matching.
[0053] Single Event Sequence—A sequence of attack events consisting of a single attack event.
[0054] Correlation Analysis—Analyzes the correlation of individual attack events in a single event sequence.
[0055] Basic event - a single attack event that exists in a single event sequence and requires correlation analysis.
[0056] Session quadruple - a group composed of four elements in a TCP connection, source IP, destination IP, source port, and destination port.
[0057] The correlation analysis attack detection method based on time series and event sequence described in this embodiment, the operating principle block diagram is shown in Fig. Detection, after detecting single-step attack behaviors, analyze these attack behaviors in two dimensions, namely the time dimension and the event sequence dimension. And based on this analysis, the detect...
Embodiment 2
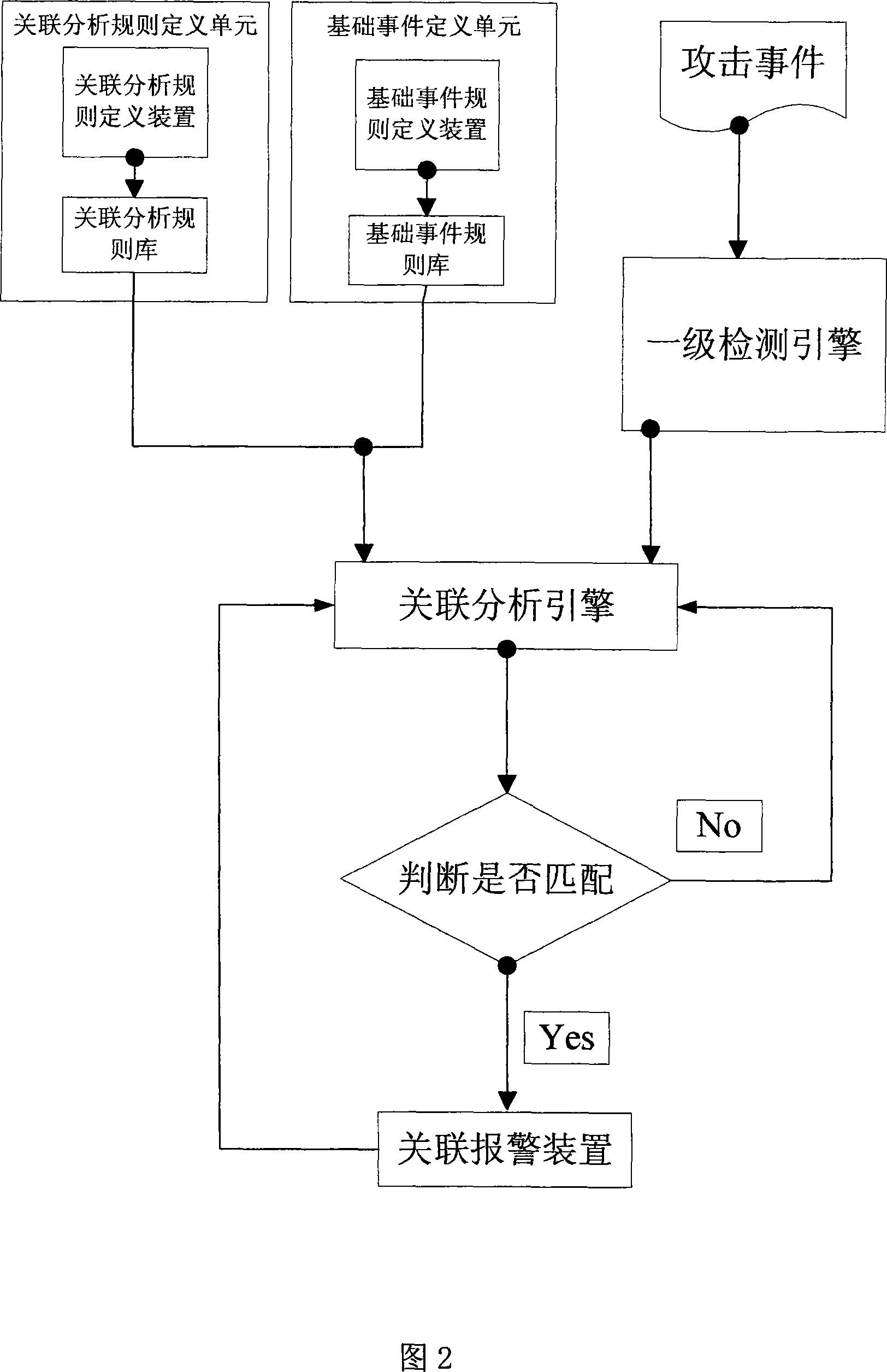
[0109] The correlation analysis attack detection device based on time series and event sequence, the functional block diagram is shown in Figure 2, including:
[0110] A basic event definition unit, a correlation analysis rule definition unit, a first-level event detection engine, and a correlation analysis detection engine.
[0111] Basic event definition unit: This unit mainly completes the basic events required for correlation analysis events, that is, the definition of event fragments. Basic events can be defined on any protocol level, and basic events can be defined complexly using & and | operators .
[0112] Association analysis rule definition unit: This module mainly completes the definition of association analysis events and defines the relationship between basic events. This definition needs to take two factors into account: the order of occurrence time between basic events, fragmentation events The sequence of events that occurred in between (this time may not be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com