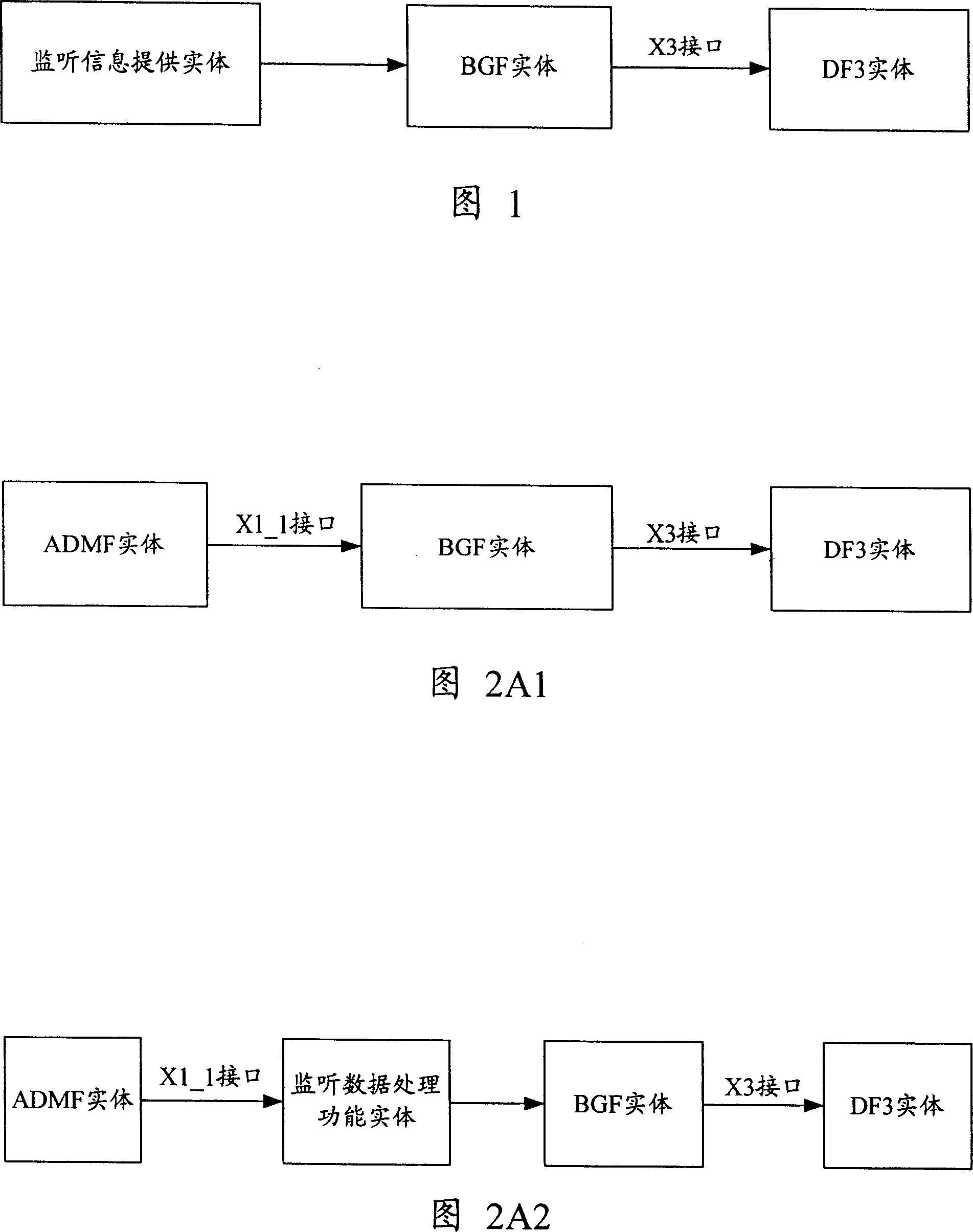
Method and system for realizing legal monitoring in nextgeneration network
A lawful interception, next-generation technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problems of unable to send media streams, no collection scheme, and unable to realize NGN user monitoring.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
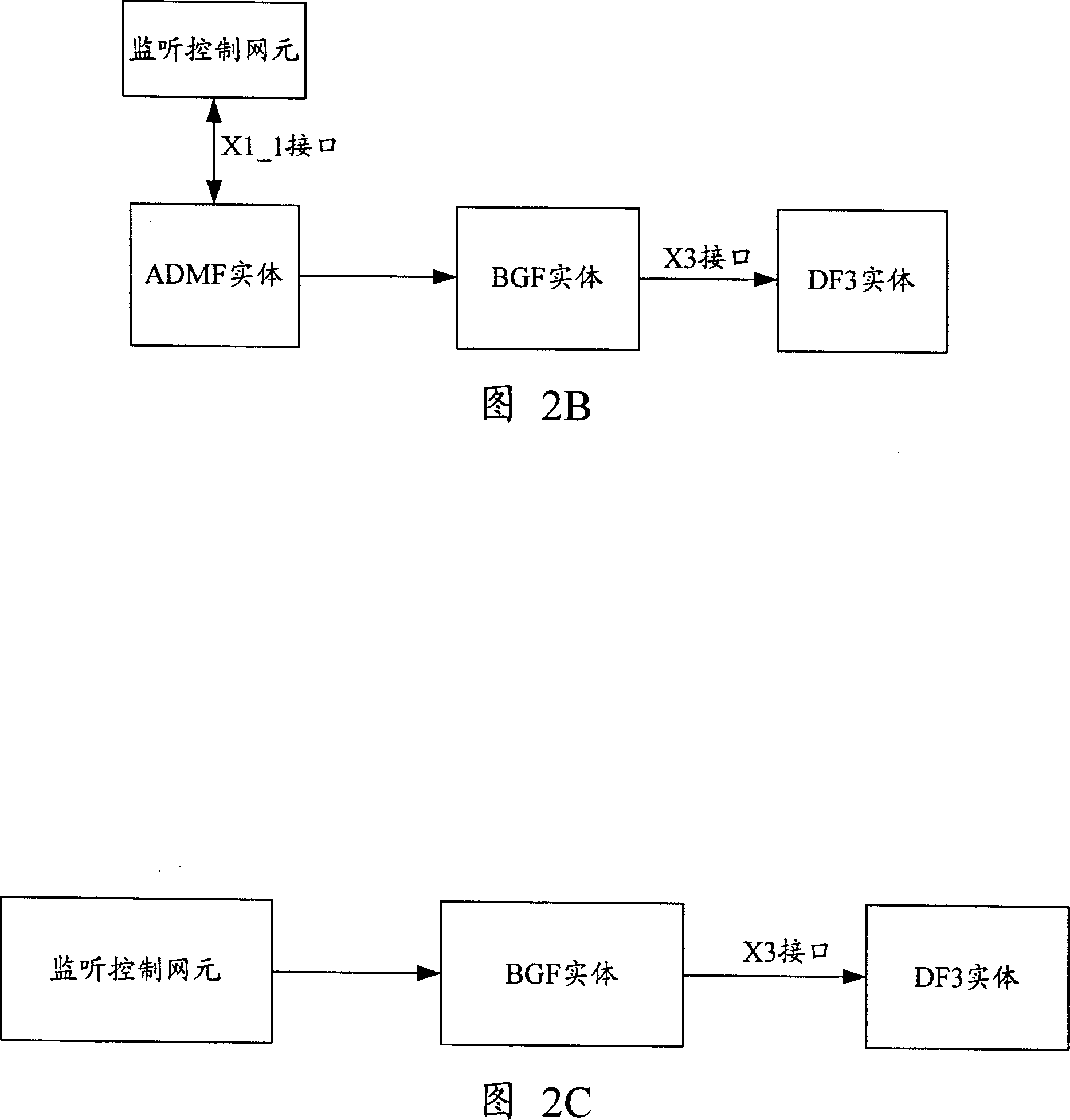
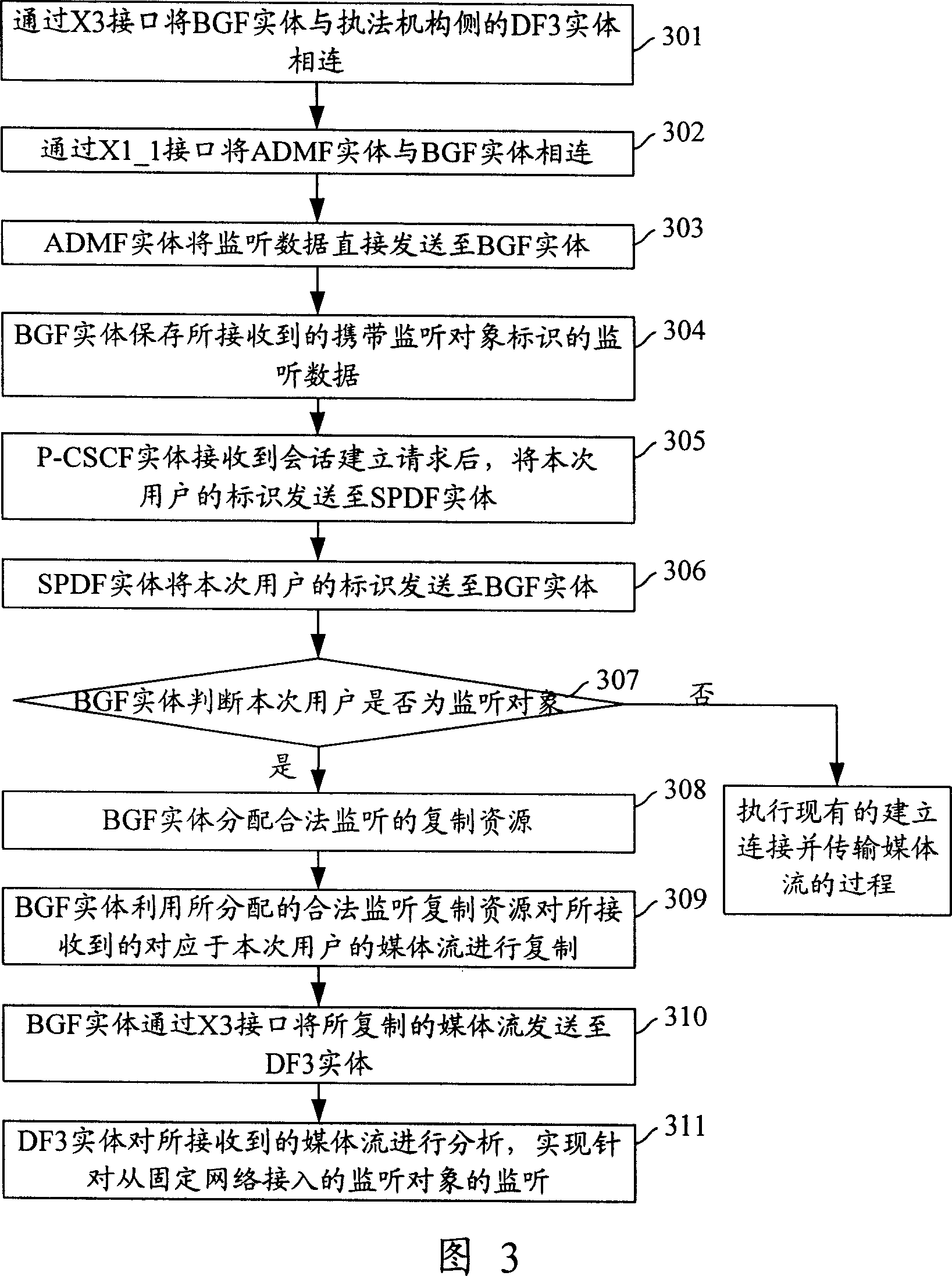
[0117] Fig. 3 is a flowchart of Embodiment 1 of the present invention. Referring to Figure 2A1 and Figure 3, in Embodiment 1, the ADMF entity on the law enforcement agency side is used as the monitoring information providing entity described in the present invention, and the BGF entity is used as the monitoring control network element as an example. In the NGN network, this implementation Example The process of implementing lawful interception for users accessing from a fixed network includes the following steps:
[0118] Step 301: Connect the BGF entity in the NGN network with the DF3 entity on the law enforcement agency side through the X3 interface in advance.
[0119] Step 302: Connect the ADMF entity on the law enforcement agency side with the BGF entity in advance through the existing X1_1 interface.
[0120] Step 303: When an interception object needs to be intercepted, the ADMF entity on the law enforcement agency side directly sends the interception data carrying the...
Embodiment 2
[0150] Fig. 4 is a flowchart of Embodiment 2 of the present invention. Referring to Figure 2B and Figure 4, in Embodiment 2, the ADMF entity is used as the monitoring information providing entity described in the present invention, but the BGF entity is not used as the monitoring control network element as an example. In the NGN network, the present invention aims at The process for users accessing the network to implement lawful interception includes the following steps:
[0151] Step 401: Connect the BGF entity in the NGN network with the DF3 entity on the law enforcement agency side through the X3 interface in advance.
[0152] Step 402: When an interception object needs to be intercepted, the ADMF entity on the law enforcement agency side sends the interception data carrying the interception object identifier to the existing interception control network element through the X1_1 interface.
[0153] Here, the P-CSCF entity, the S-CSCF entity, and the LI-AS as the intercepti...
Embodiment 3
[0164] In this embodiment 3, the interception control network element in the NGN network is used as the interception information providing entity in the present invention, and the interception control network element triggers the BGF entity to copy the media stream of the interception object by carrying the interception data in the message .
[0165] Fig. 5 is a flow chart of Embodiment 3 of the present invention. Referring to Fig. 2C and Fig. 5, for the convenience of description, take the lawful interception application server (LI-AS) in the NGN network as the interception control network element, and carry the interception data in the message to trigger the BGF entity to copy the media stream of the interception object as an example In this embodiment, the process of implementing lawful interception for users accessing from a fixed network includes the following steps:
[0166] Step 501: Connect the BGF entity in the NGN network with the DF3 entity on the law enforcement a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com