Method for implementing legal monitoring
A technology of lawful interception and interception system, applied in the field of interception, can solve the problems of restricting the application of lawful interception business and reducing the service quality of lawful interception business, and achieve the effect of expanding the scope of application and improving the quality of business service.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
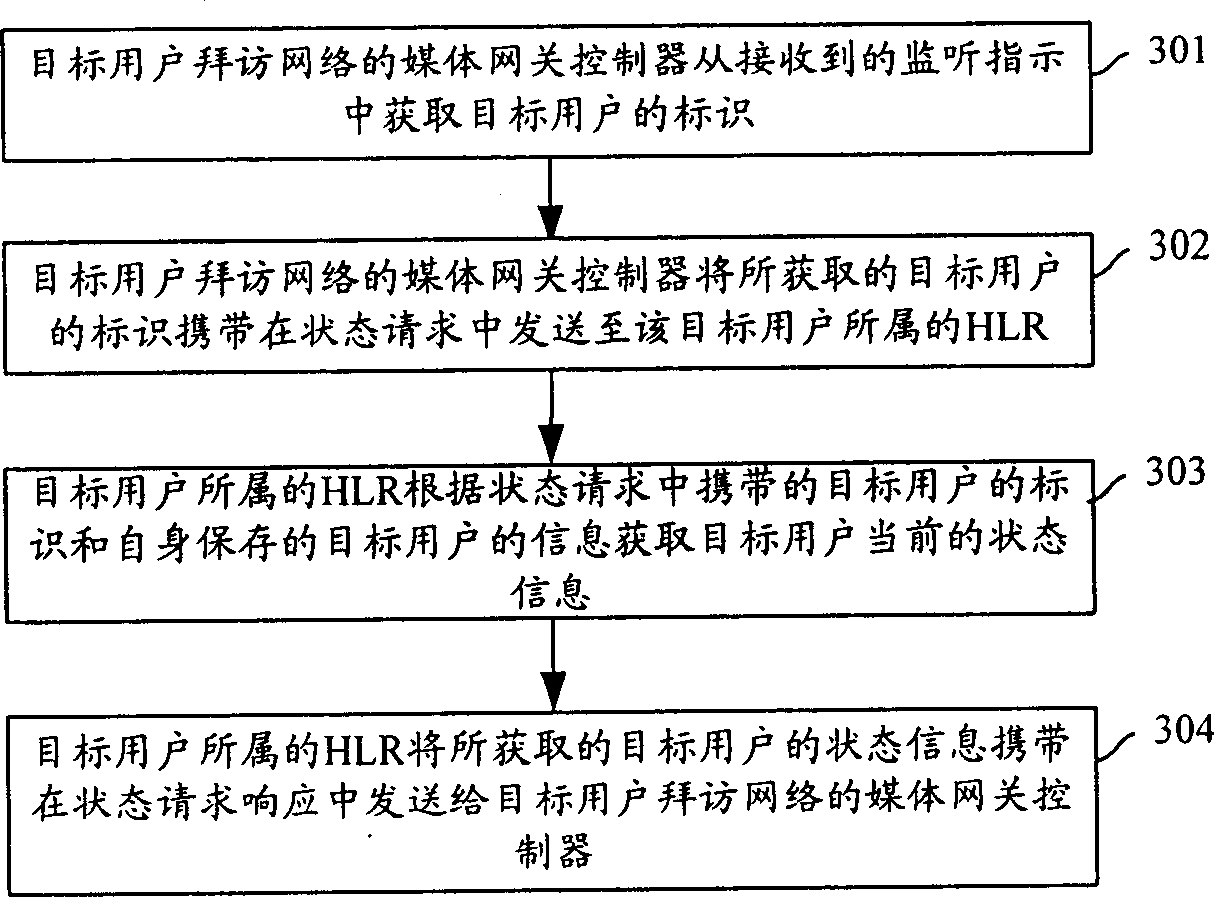
Embodiment 1
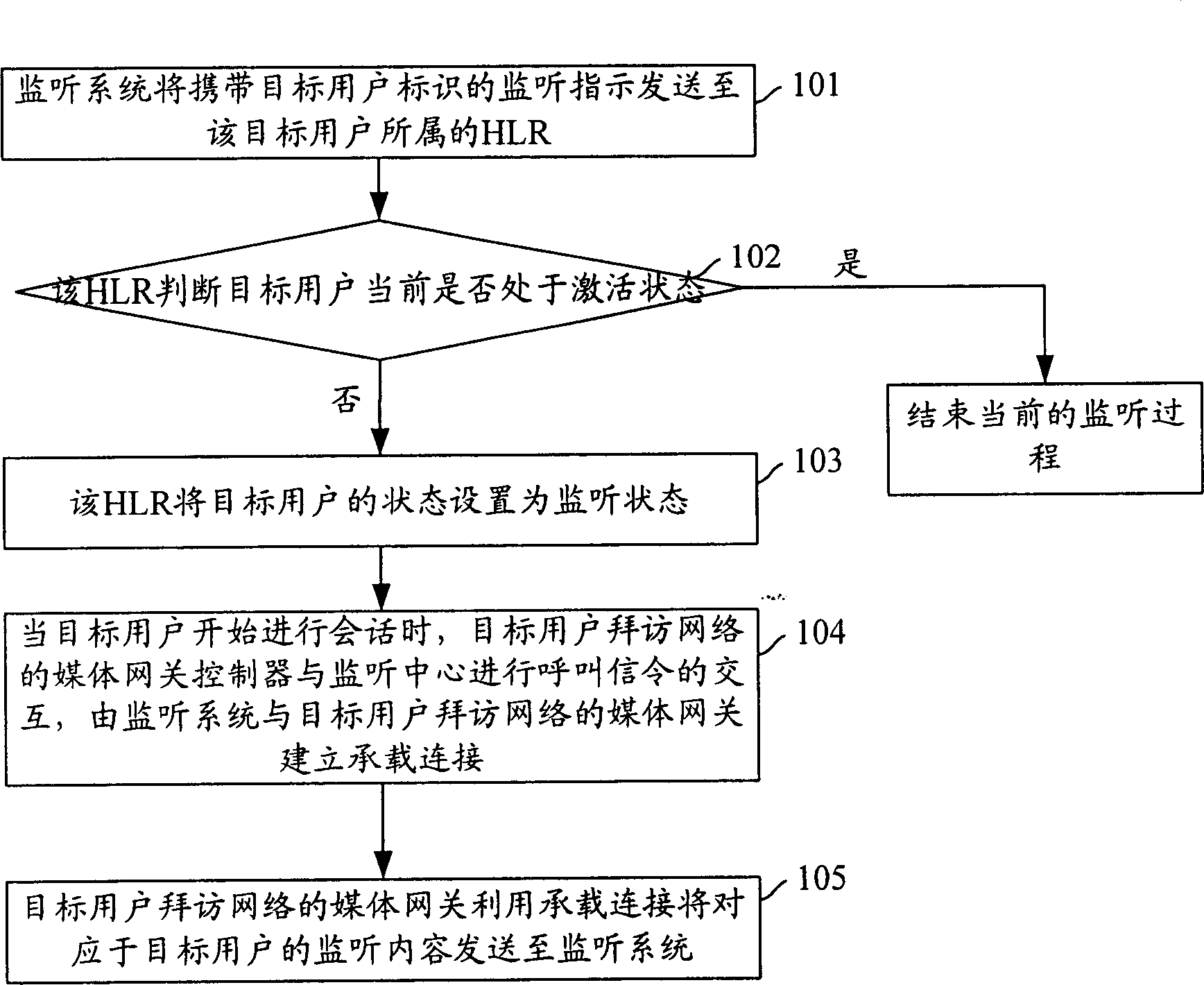
[0053] In this embodiment, the specific implementation process of the present invention is described by taking the monitoring system as an example to initiate a bearer establishment call to the media gateway controller of the network visited by the target user.
[0054] figure 2 It is a flow chart of implementing lawful interception in the CS in Embodiment 1 of the present invention. see figure 2 , in the present invention, the process of realizing lawful interception in CS specifically includes the following steps:
[0055] Step 201: the monitoring system sends a monitoring instruction to the HLR to which the target user belongs.
[0056] Here, the interception instruction sent by the interception system to the HLR to which the target user belongs carries the identity of the target user, interception content information and other relevant interception information. Here, the identifier of the target user may include: MSISDN, IMSI, IMEI, SIP URI, TEL URL, NAI. The monitor...
Embodiment 2
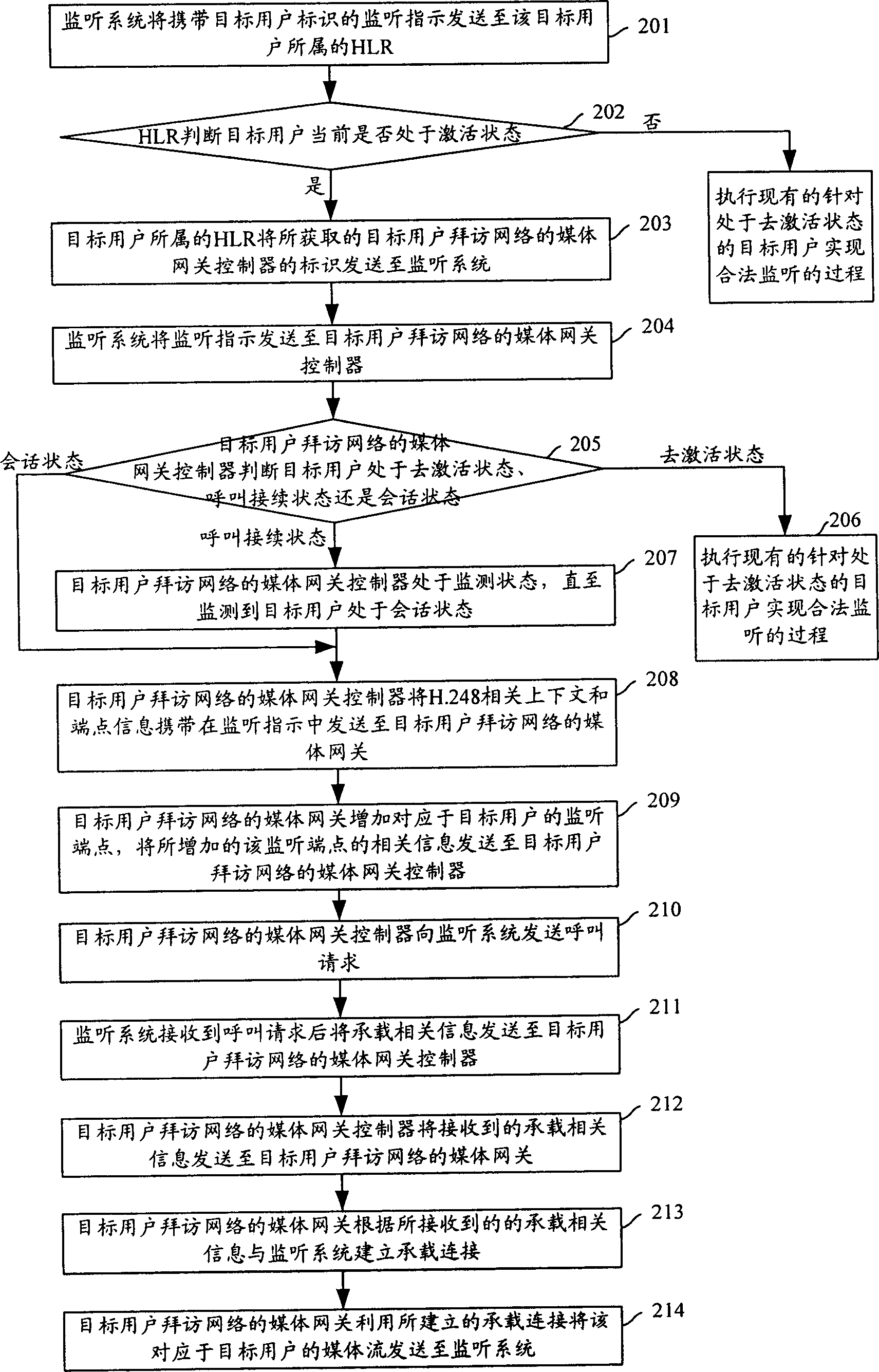
[0090] In this embodiment, the specific implementation process of the present invention is described by taking the media gateway controller of the network visited by the target user to initiate a call to the monitoring system to establish a bearer connection as an example.
[0091] Figure 4 It is a flow chart of implementing lawful interception in the CS in Embodiment 2 of the present invention. see Figure 4 , in the present invention, the process of realizing lawful interception in CS specifically includes the following steps:
[0092] All descriptions of steps 401 to 407 are the same as those of steps 201 to 207.
[0093] Step 408: The MGC of the network visited by the target user sends an interception response to the interception system.
[0094]Here, when sending the monitoring response, the media gateway controller of the network visited by the target user may further carry the information that the target user is in a session state in the monitoring response and send...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com