Method and system for preventing charge cheat and medium route controller
A routing and media technology, applied in the field of information security, can solve the problems of delay loss, signaling flow attack, multi-resource, etc., and achieve the effect of preventing billing fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention is a billing method, system and media routing control device. In order to make the purpose, technical solution and advantages of the present invention clearer, the following describes the present invention in detail with reference to the accompanying drawings and examples.
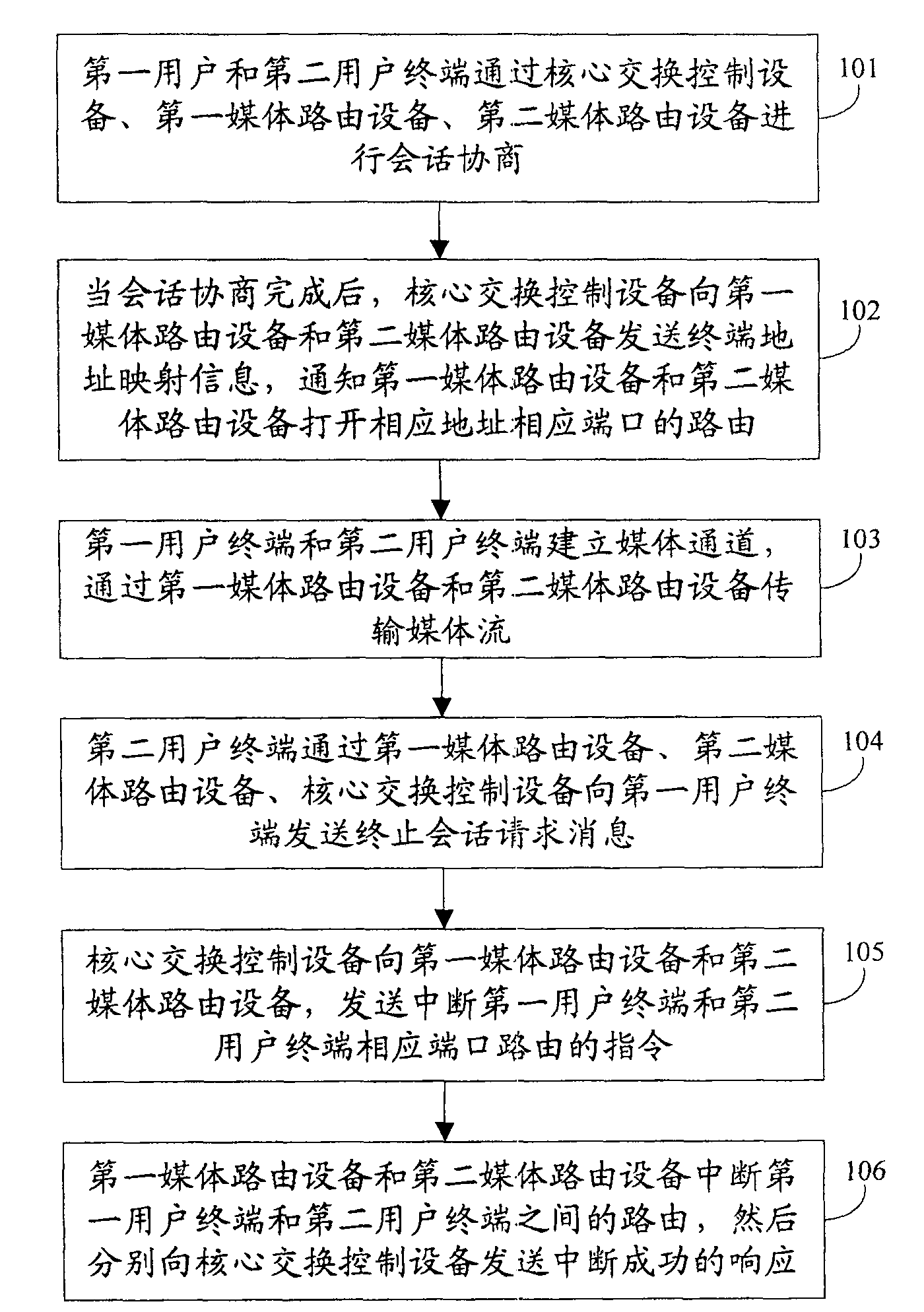
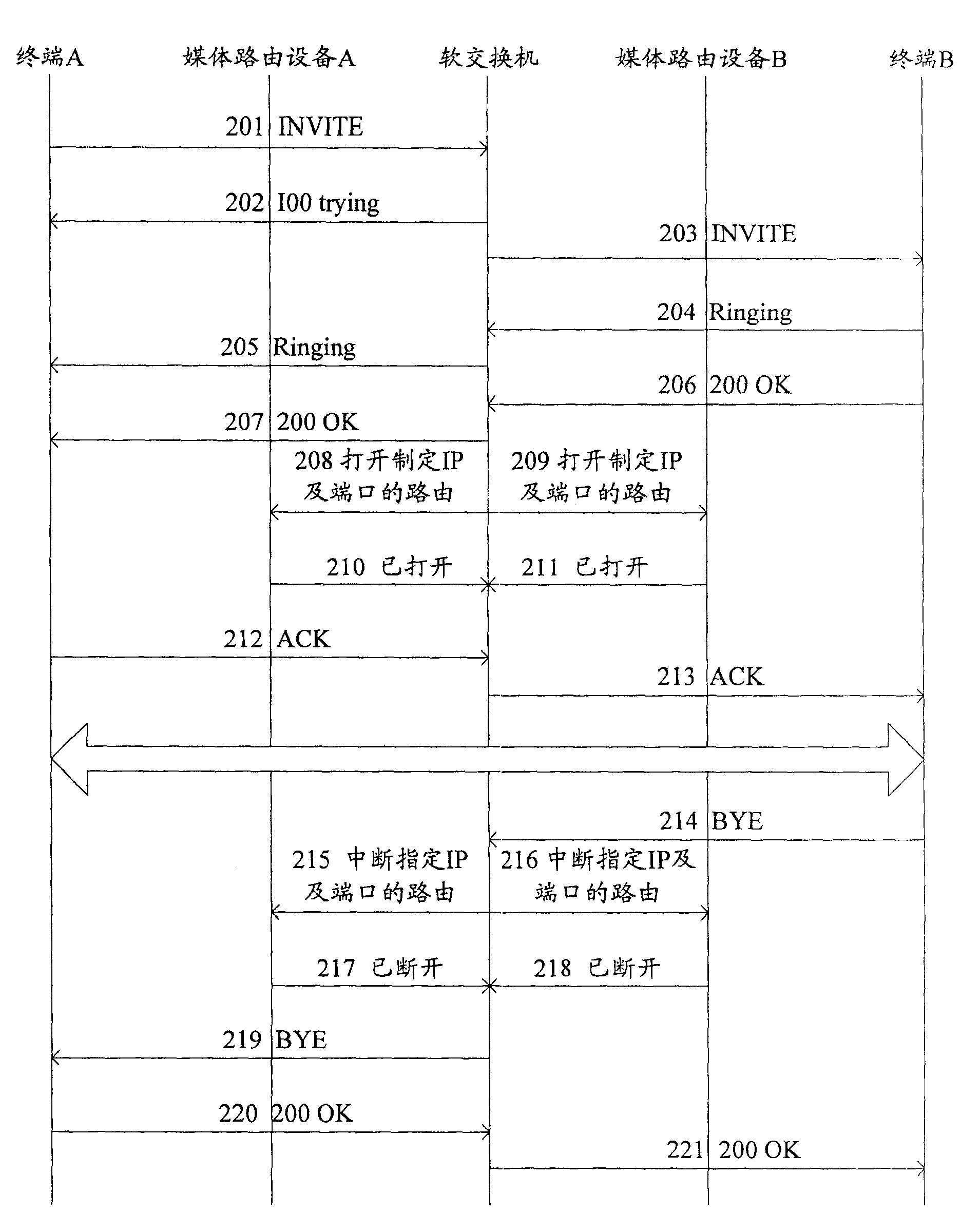
[0021] see figure 1 , is a flowchart of the present invention, specifically including:
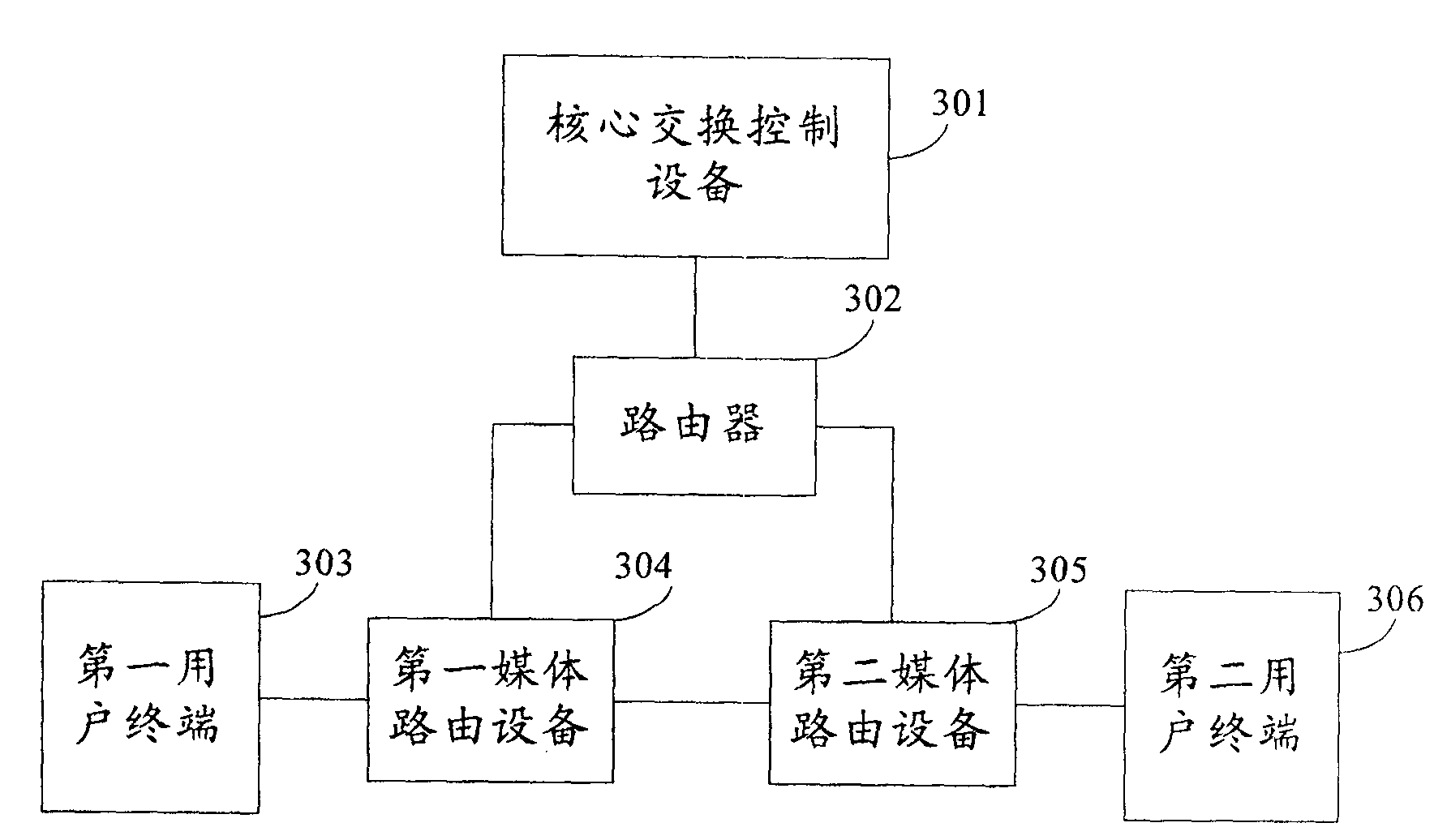
[0022] 101: The first user and the second user terminal perform session negotiation through the core switching control device, the first media routing device, and the second media routing device;
[0023] 102: After the session negotiation is completed, the core switching control device sends terminal address mapping information to the first media routing device and the second media routing device, and notifies the first media routing device and the second media routing device to open the route of the corresponding port of the corresponding address;
[0024] 103: The first user terminal an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com