Safety detecting method and purview control system for client terminal
A technology of security detection and authority control, which is applied in the field of communication security, can solve problems such as difficult maintenance, inconsistency, and authorization errors for administrators, and achieve the effects of improving work efficiency, facilitating maintenance, and increasing the success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
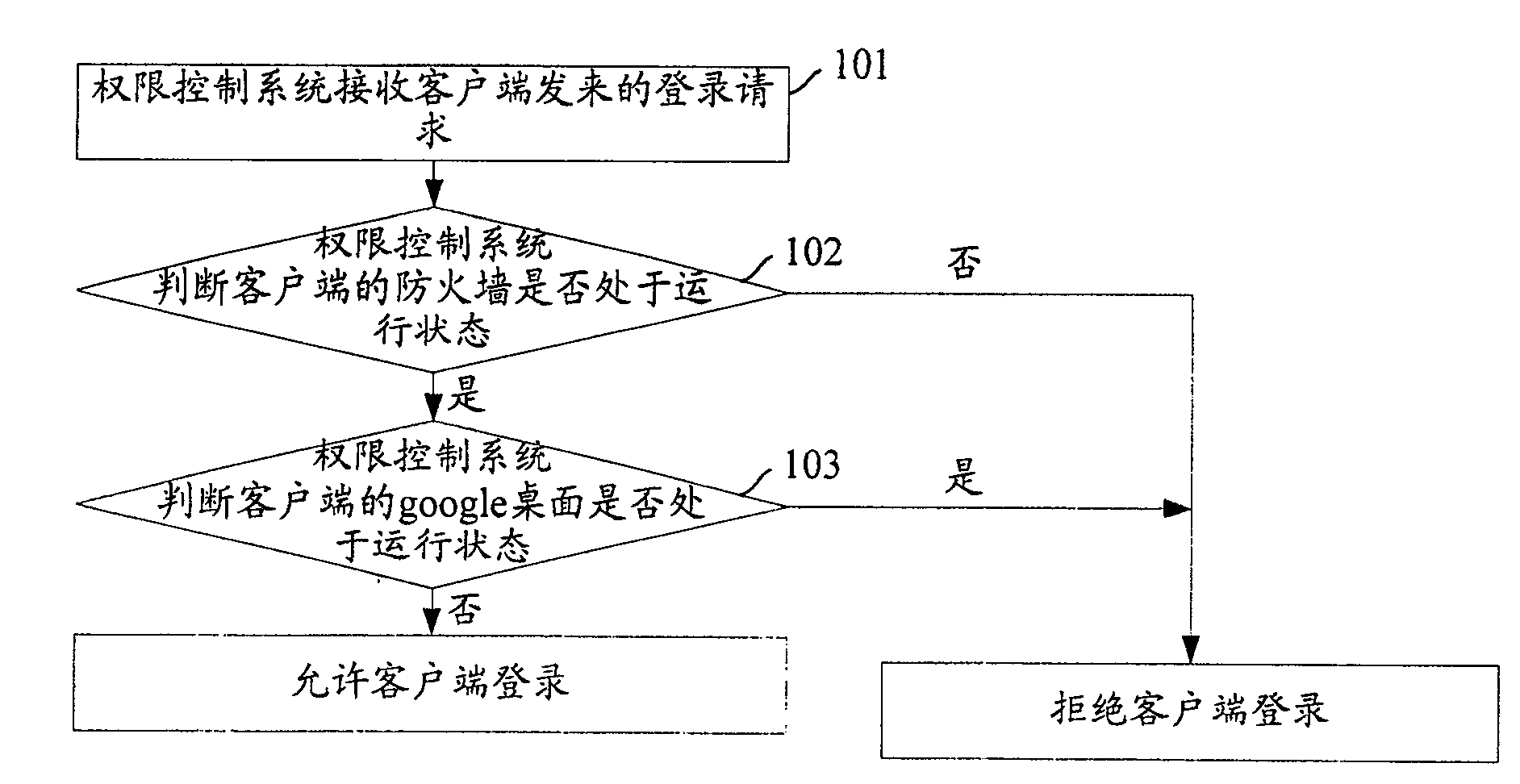
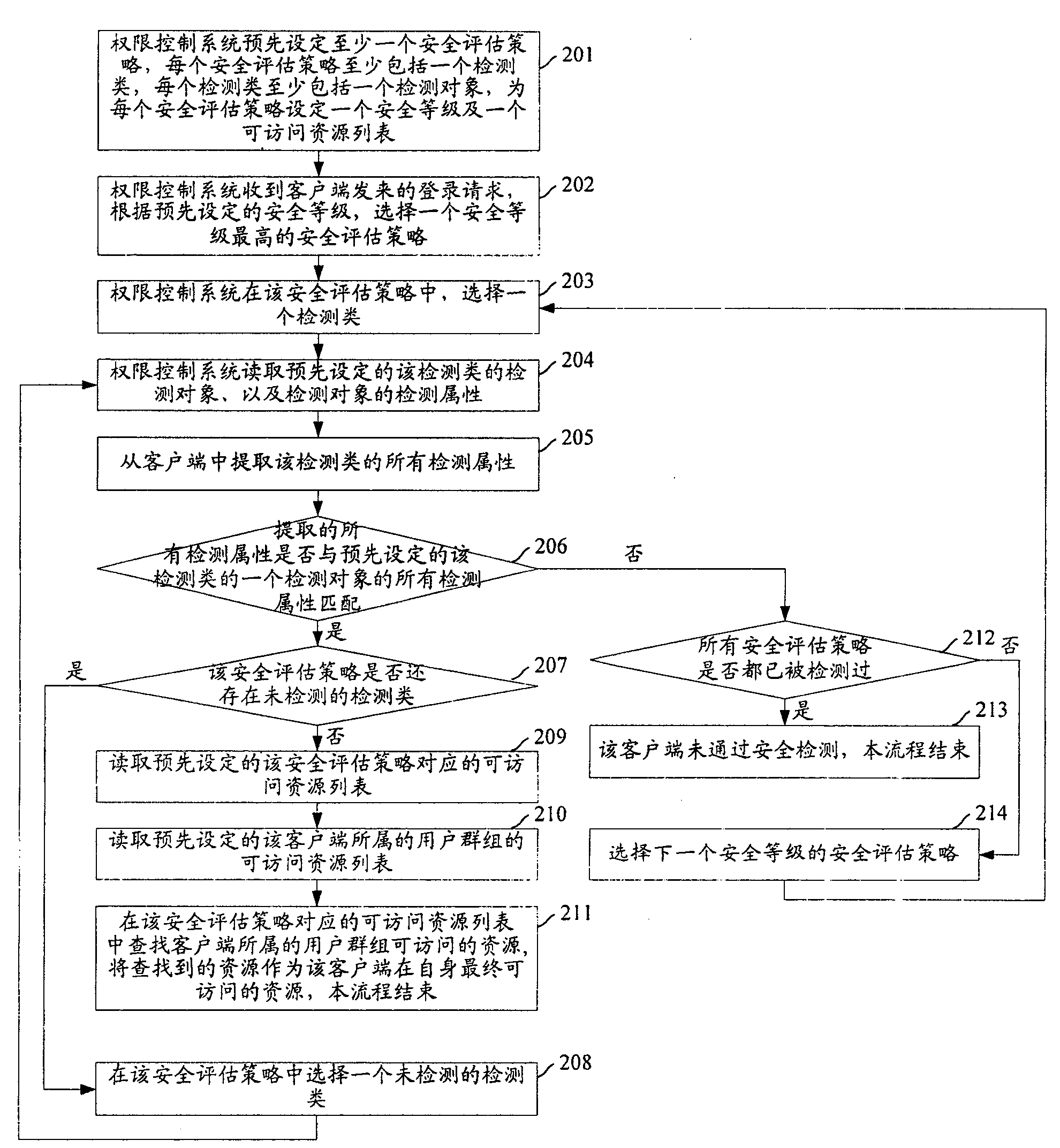
[0049] figure 2 It is a flow chart of performing security detection on the client provided by the embodiment of the present invention, such as figure 2 As shown, the specific steps are as follows:
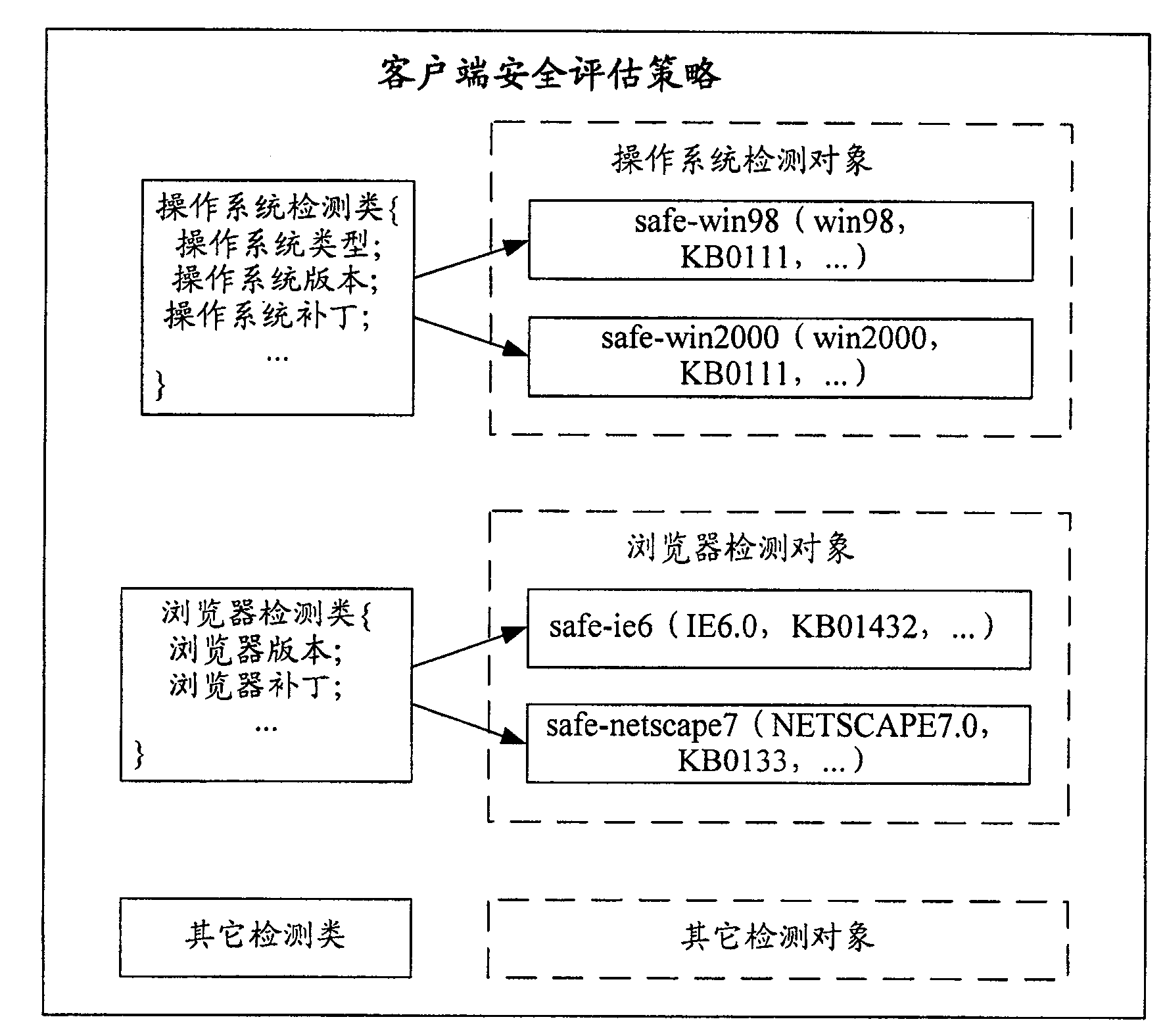
[0050] Step 201: The authority control system presets at least one security evaluation strategy, such as image 3 As shown, each security assessment strategy includes at least one detection class, and each detection class includes at least one detection object, each detection object corresponds to its own detection attribute, a security level is set for each security assessment strategy, and each security Evaluation policies set a list of accessible resources.
[0051] The detection class refers to the target object for security detection on the client, such as image 3 As shown, it may include: operating system detection category, b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com