A transmission method for cut packets
A sending method and pruning technology, which is applied in the field of sending pruned messages, can solve the problems of CPU resource consumption, router performance impact, waste of path network bandwidth, etc., and achieve the effect of simple implementation and elimination of data transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the purpose, technical solution and advantages of the present invention clearer, the following examples are given to further describe the present invention in detail.
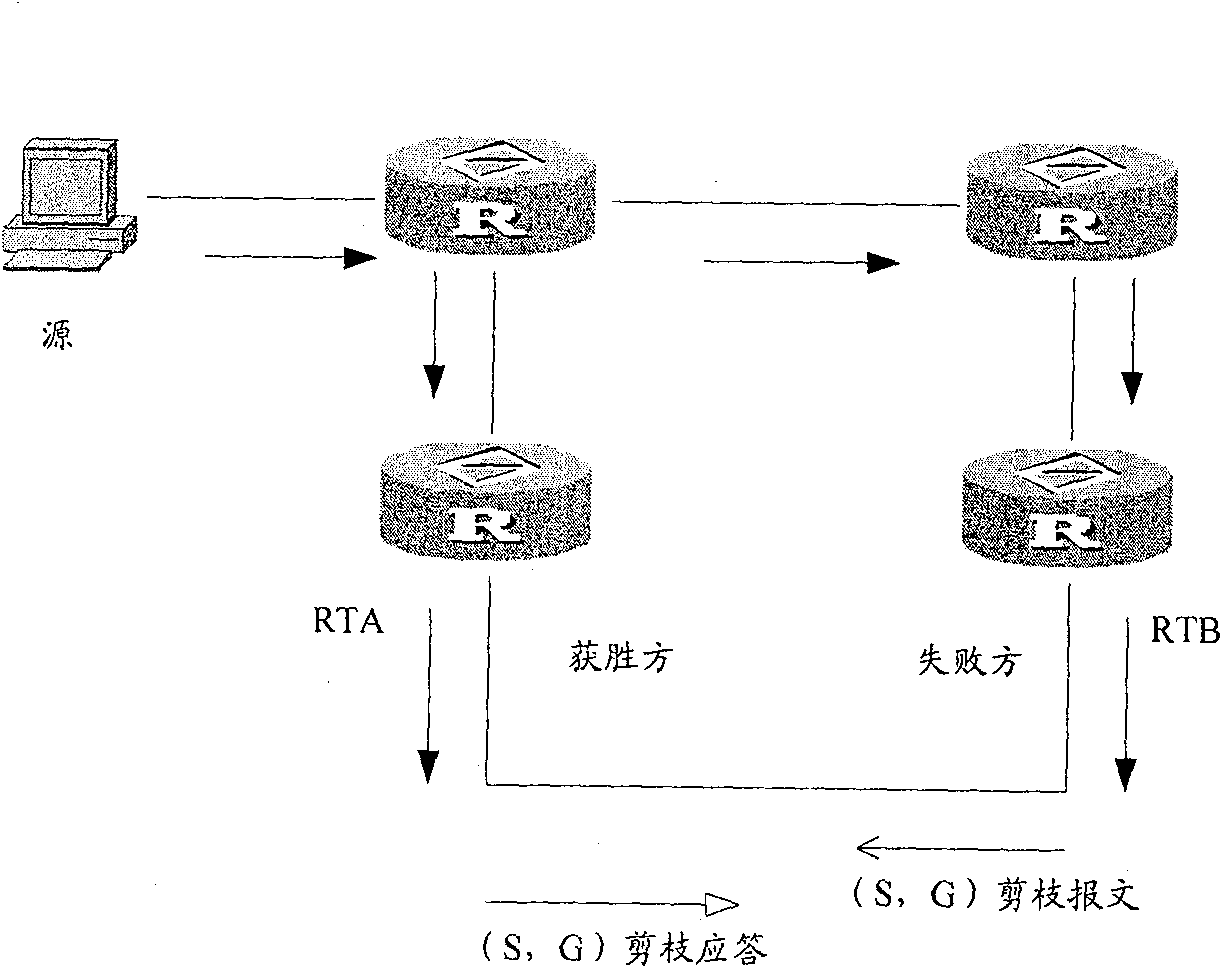
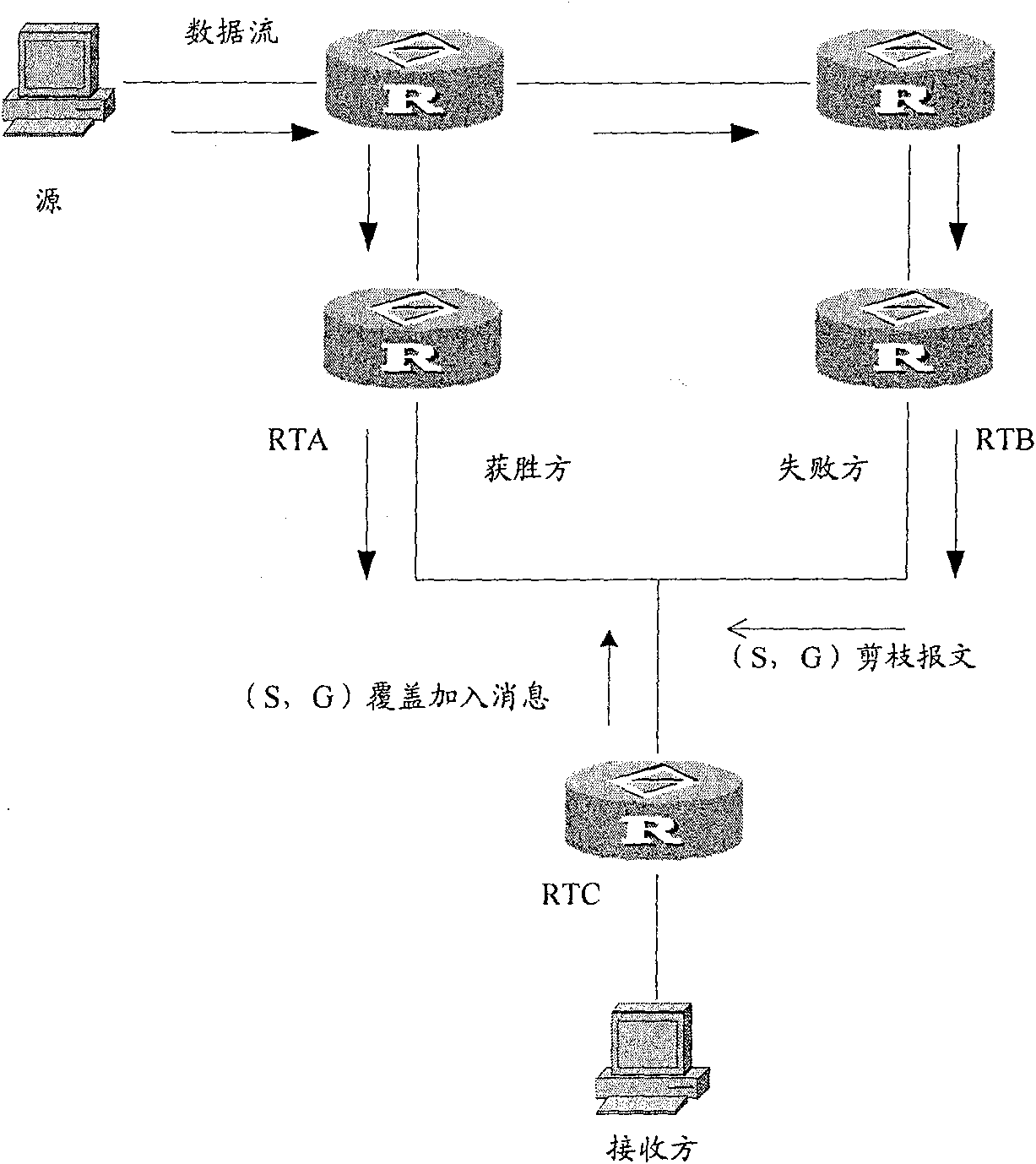
[0030] The core idea of the present invention is: when the assertion loser fails in the assertion, that is, when entering the loser state from the no-information state, or the assertion fails again, that is, when the assertion message of the new winner is received again in the loser state, the assertion The loser sets the status information as unpruned; when the status information is unpruned, the assertion loser satisfies the trigger condition and sends a pruning message to the assertion winner.
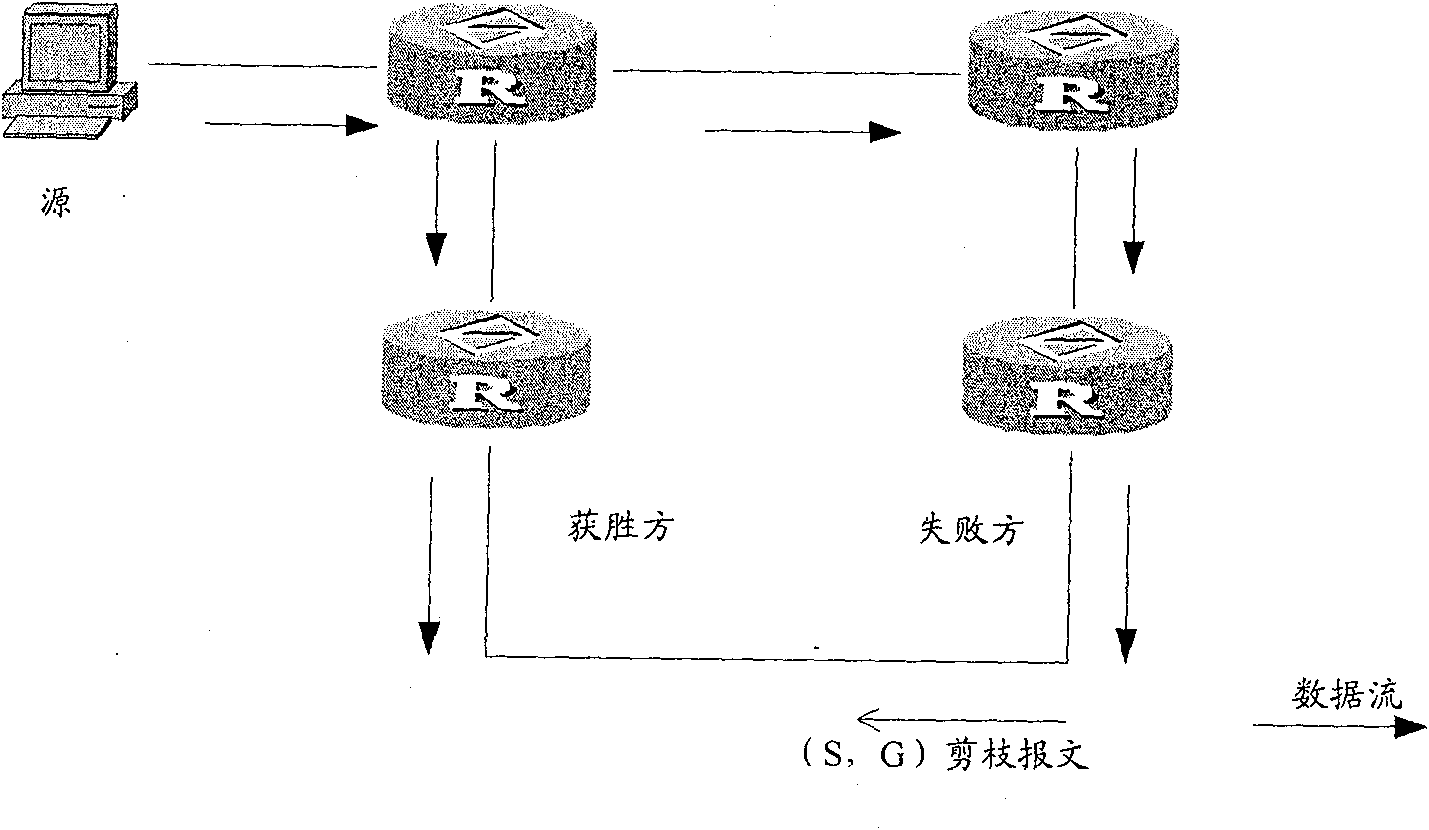
[0031] refer to figure 2 , when there is no downstream router or no downstream router receiving data, the process of the embodiment of the present invention is as follows:
[0032] After the assertion fails, the assertion loser (RTB) sets the prune status flag bit to indicate the unprune s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com