Method for guarding against attack realized for networked devices
A network device and anti-attack technology, which is applied in the network field, can solve problems such as poor anti-attack capabilities and affect normal business, and achieve the effect of preventing attacks, enhancing defense capabilities, and maintaining network order
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
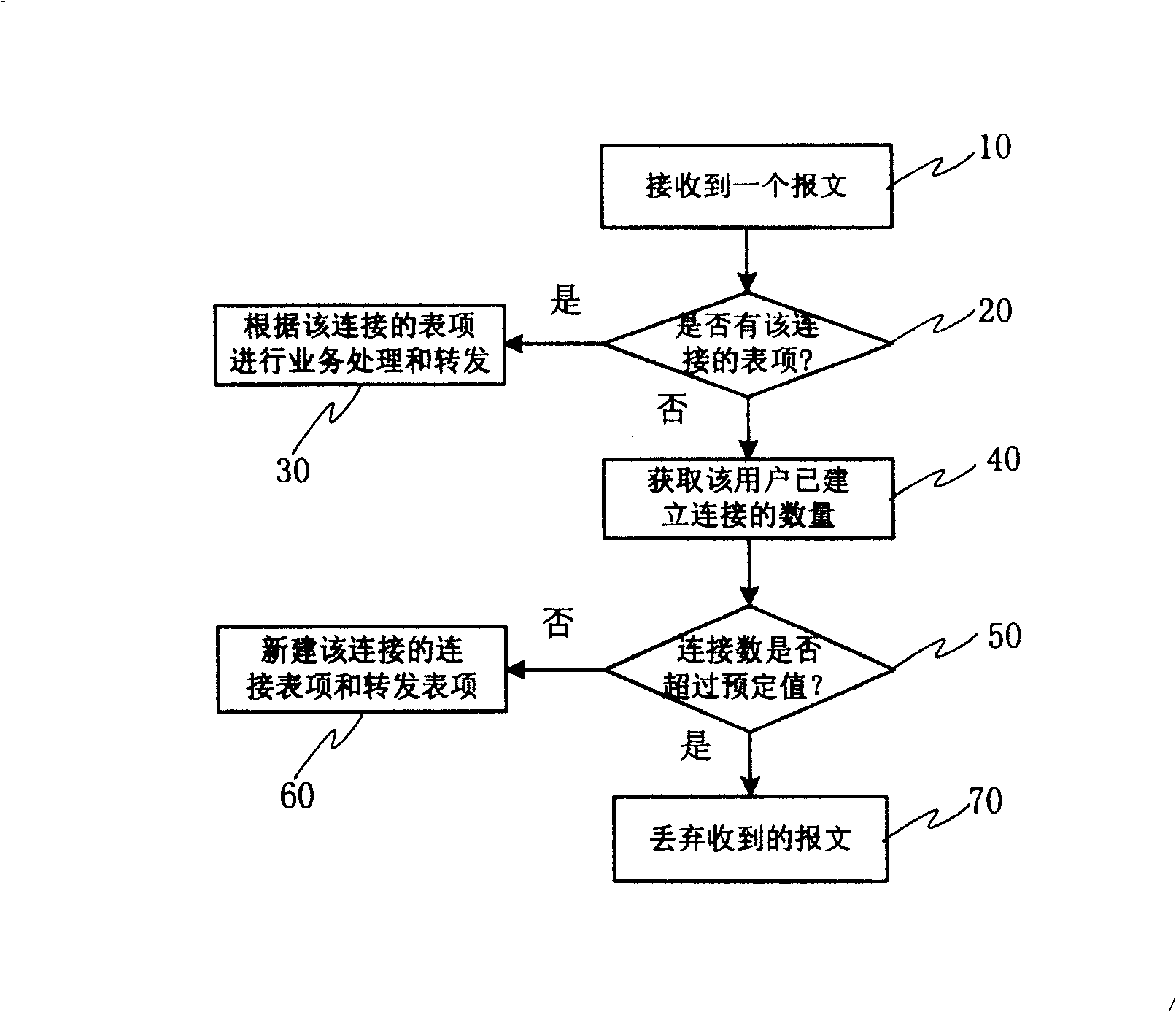
[0024] The invention prevents TCP SYN Flood and UDP Flood attacks by limiting the number of transmission control protocol / user datagram protocol (TCP / UDP) connections of each user.
[0025] The network storm (SYN Flood) attack is that the attacker sends a large number of first packet packets SYN to the server, and the server will send the first packet response packet SYN ACK after receiving each first packet packet, and establish the transmission control protocol (TCP) Half-open the connection, and then wait for the response message ACK from the client side. But the attacker will not send the response message ACK that the server is waiting for, causing the server to be full of half-open connections. Because the server keeps sending out the first packet response message SYN ACK without any response, the server is in an abnormally busy state, making it difficult to process normal connection requests, and eventually causing normal business interruption.
[0026] Since the transm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com