System, method, apparatus and computer program product for facilitating digital communications
a technology of digital communication and computer program, applied in the field of system, method, apparatus and computer program product for facilitating digital communication, can solve the problems of vpn being compromised, vpn using a conventional vpn client is vulnerable to the extent of user's ra credentials vulnerable, and encrypted user id and passwords are not necessarily protected from th
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Referring now to the drawings, wherein like reference numerals designate identical or corresponding parts throughout the several views.
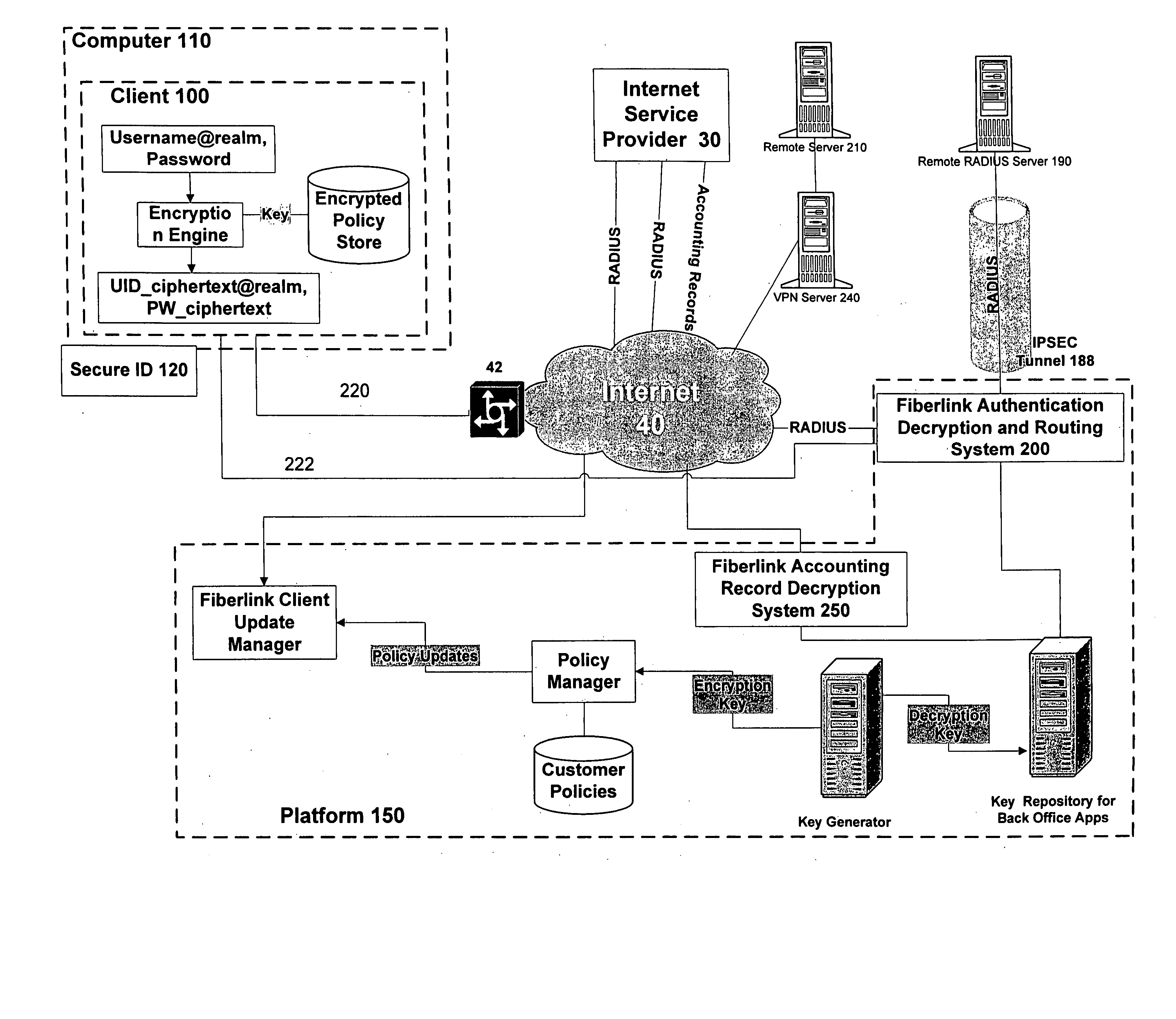
[0042] An exemplary embodiment of the present invention is illustrated in FIG. 4. FIG. 4 shows a computer system including a client 100 running on a computer 110 having a connection to the Internet 40 through NAS 42. Platform 150 is also connected to Internet 40. Remote RADIUS server 190 is connected to platform 150 through IPSec tunnel 188. Platform 150 includes Authentication, Decryption, and Routing System 200 and Single Sign On Application Server (SSOS) 160. Computer 110 has a SECUREID 120 associated therewith.
[0043] When a user requires access to remote server 210 from computer 110, the user enters their login credentials (user ID and password) into computer 110. Client 100 encrypts the user's ID and separately encrypts the user's password prior to passing the encrypted credentials to computer 110, which then transmits the credentials o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com