Key synchronization in a visual cryptographic system
A technology of keys and key sets, applied in transmission systems, digital transmission systems, synchronous sending/receiving encryption equipment, etc. key, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
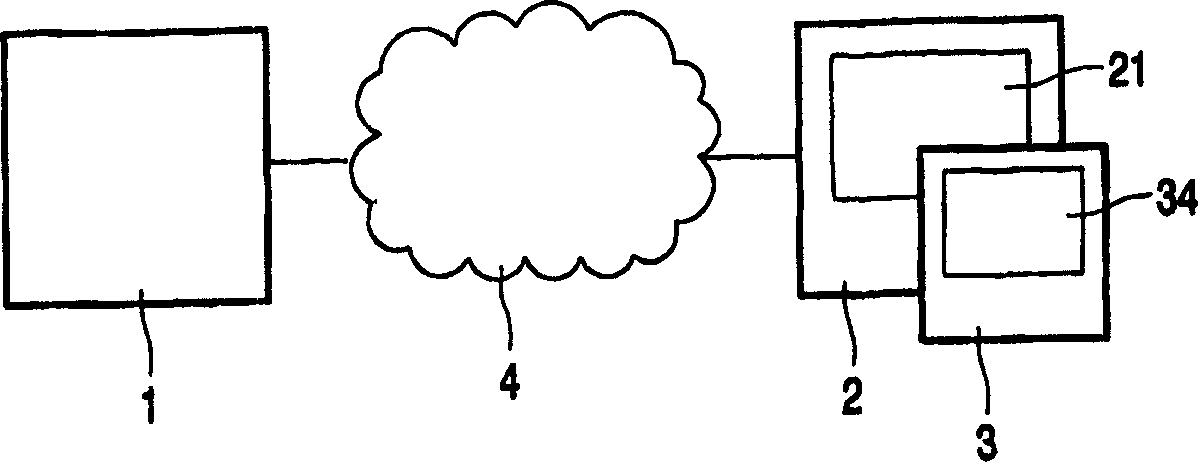
[0041] figure 1 The system in , given only as a non-limiting example, includes a server 1 , a terminal 2 , a decryptor (or decoder) 3 and a communication network 4 . The server 1 generates and encrypts an image, which is sent to the terminal 2 via the communication network 4 . The communication network 4 may consist of a dedicated network such as a LAN, a telephone network (POTS), the Internet or simply cables or wires. Both the server 1 and the terminal 2 can be dedicated devices, or they can be constituted by a general-purpose computer, at least in the case of the terminal 2 , with a display screen 21 . Decoder 3 is a cryptographic device discussed in more detail below. Both the server 1 and the decoder 3 are equipped with at least one key set consisting of a plurality of cryptographic keys. These keys are used in a suitable cryptographic process, such as DES. The special cryptographic handling used is not important.
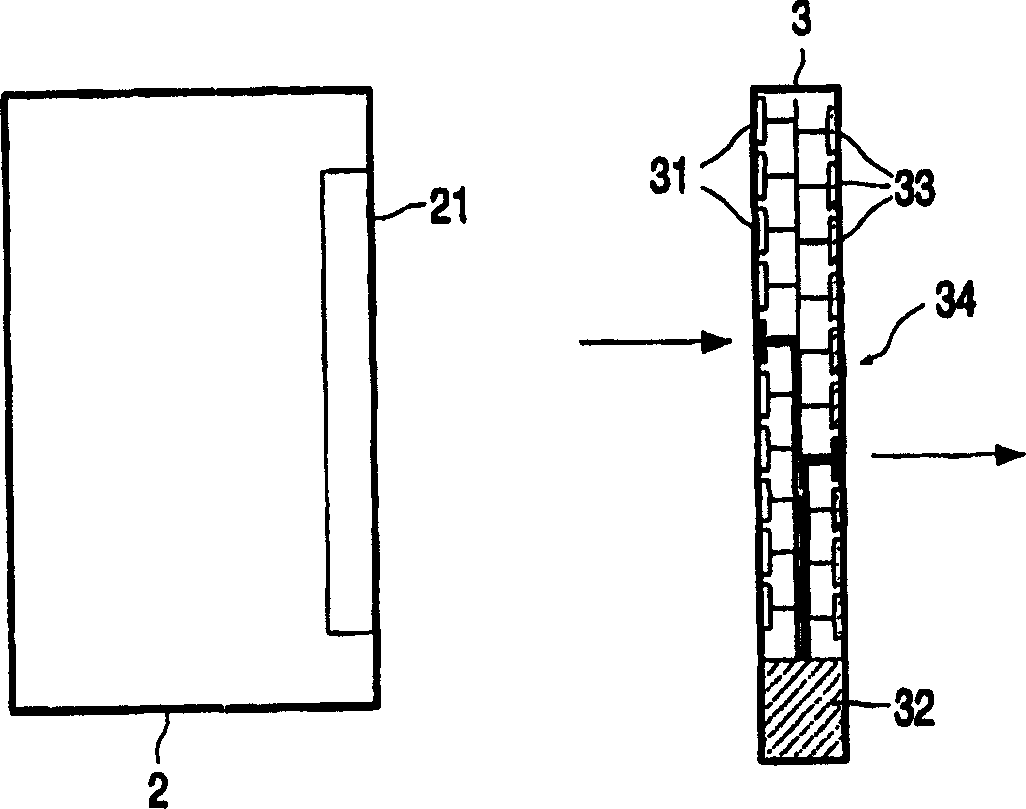
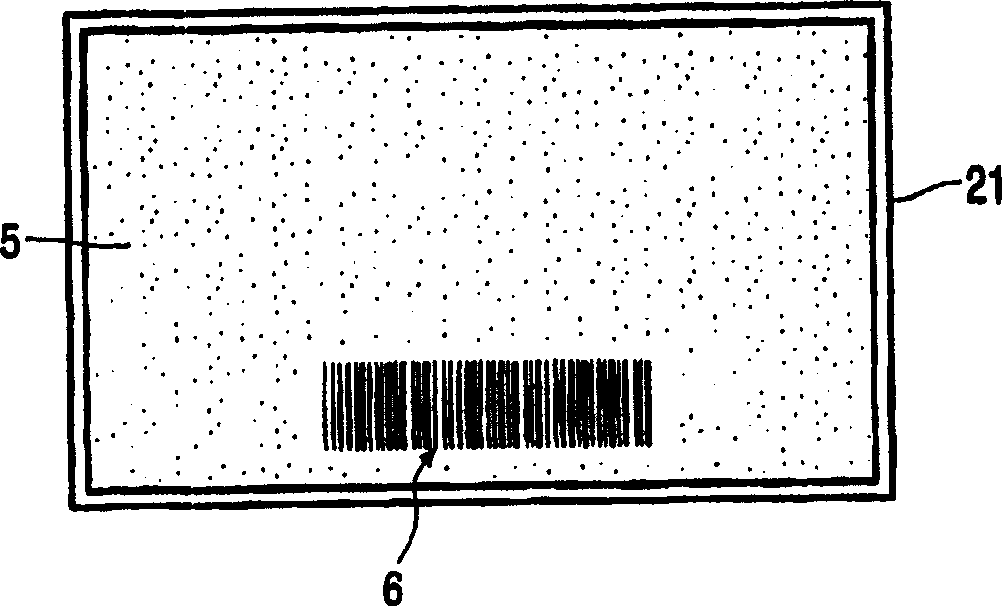
[0042] Such as figure 2 As shown in the exemplary e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com