System and method for detecting network worm in interactive mode
A detection system and network technology, applied in the field of security detection systems, can solve problems such as inestimability, network equipment, host system burden, inability to attack data packet confirmation attacks, etc., to improve the efficiency of analysis and judgment, good versatility and applicability performance and avoid false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
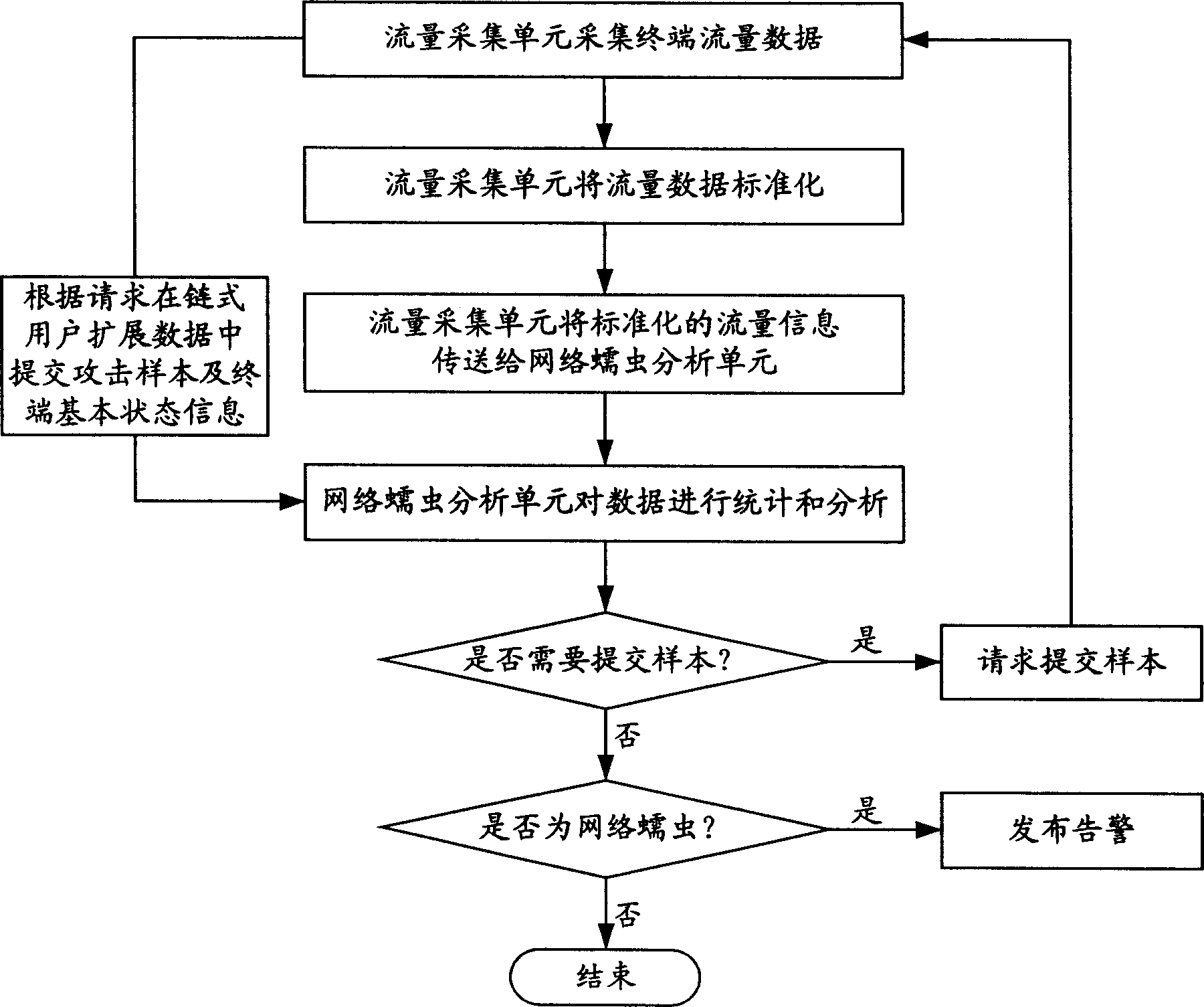
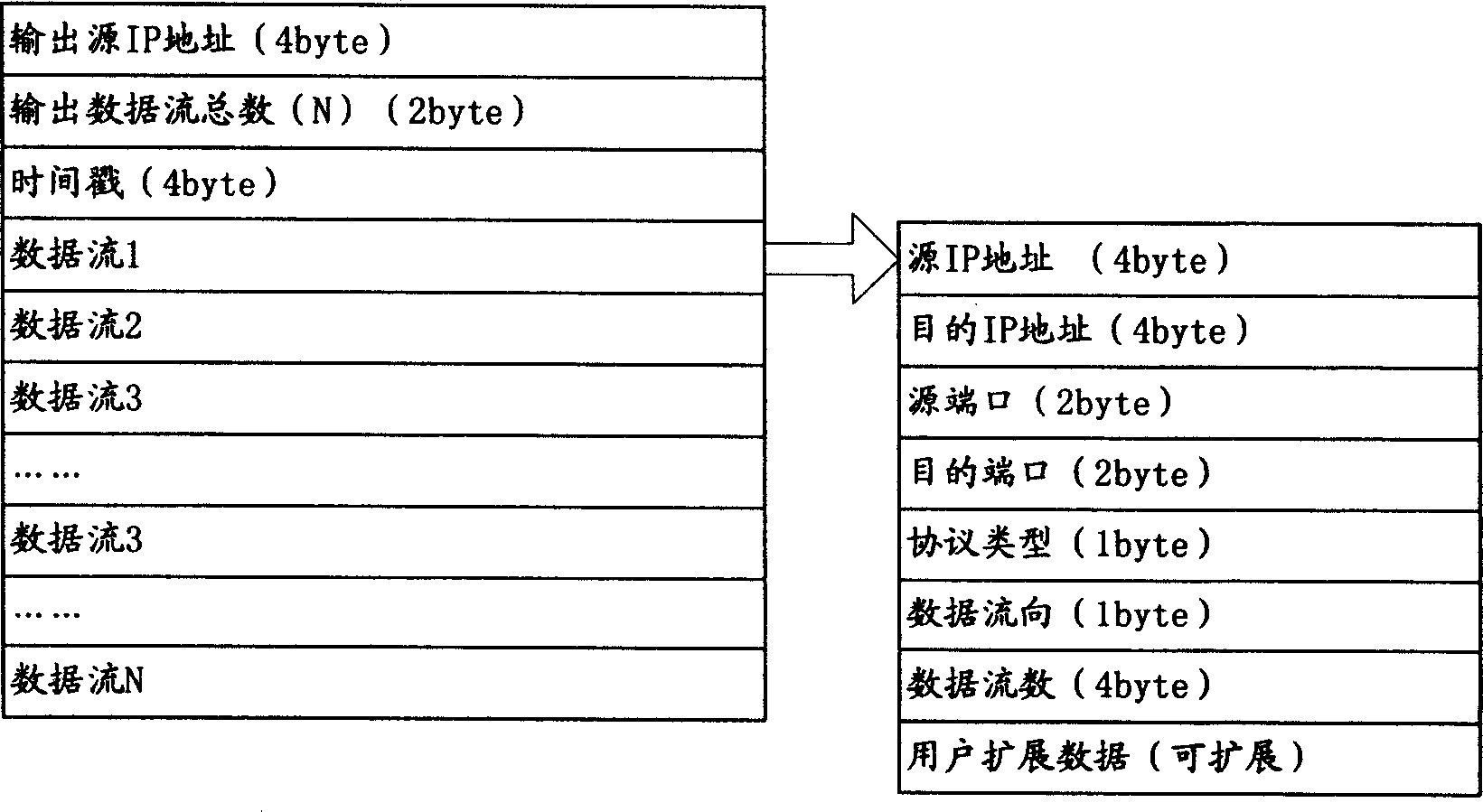
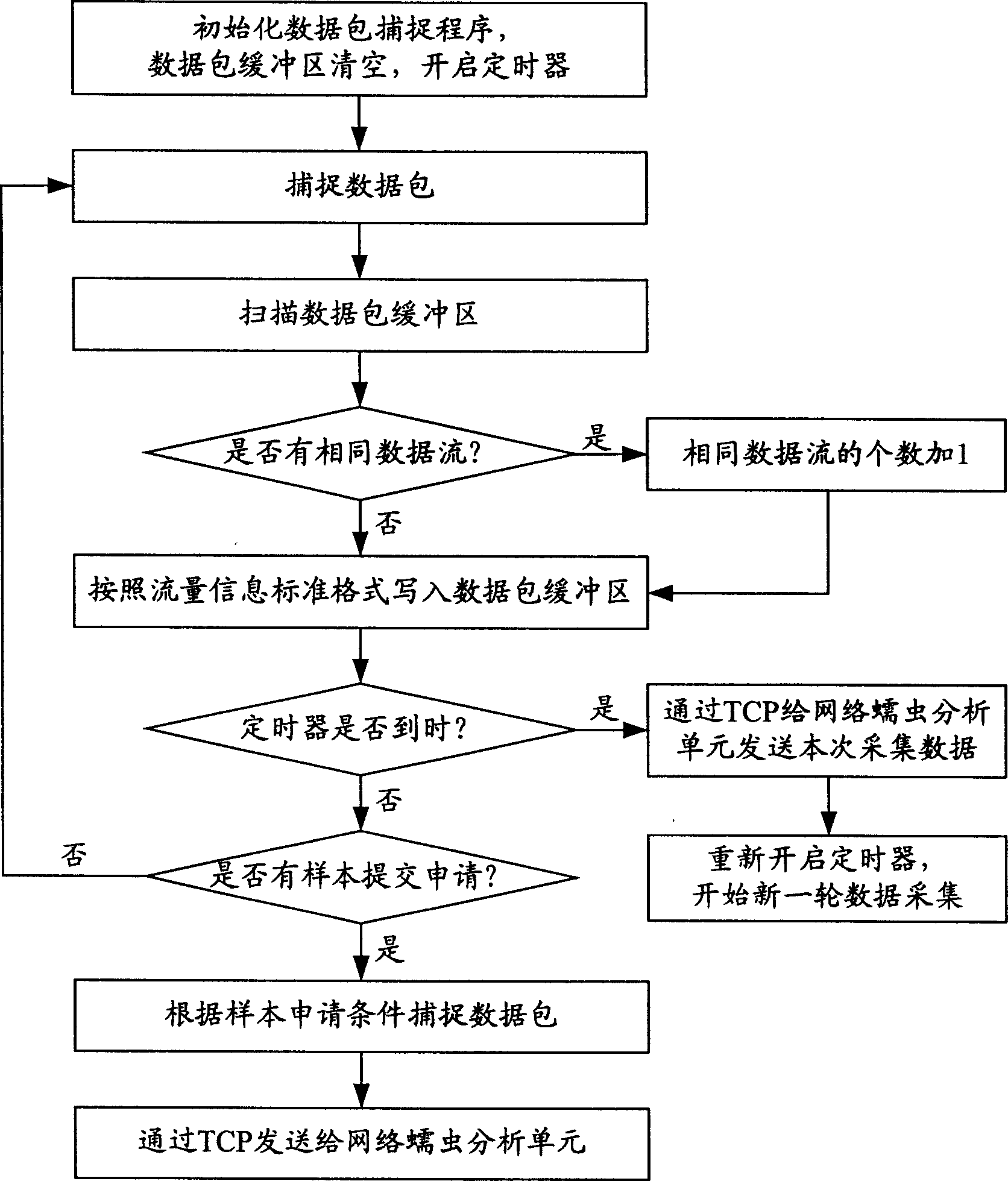
[0041] When a network worm attacks, it has certain behavioral characteristics. Usually, it first scans the computer system in the network segment to detect the existence of system vulnerabilities related to the worm attack. The targets of network worm attacks are mostly terminal devices, including PC hosts and server hosts. Based on this behavioral feature of network worms, the system of the present invention adopts distributed installation of network flow collection units on each terminal device to perform multi-point detection, and sends the flow information centrally to the network worm analysis unit located in the high-performance server for statistical analysis. Analysis and analysis based on feature matching, when it is found that some computers or servers r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com