Attack organization identification method based on industrial control flow and threat intelligence association analysis
A technology of association analysis and organization identification, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of low practicality and reference, low accuracy, etc., and achieve strong scalability, flexible identification, The effect of improving recognition accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The following in conjunction with the accompanying drawings and embodiments, the specific embodiments of the present invention will be further described in detail.
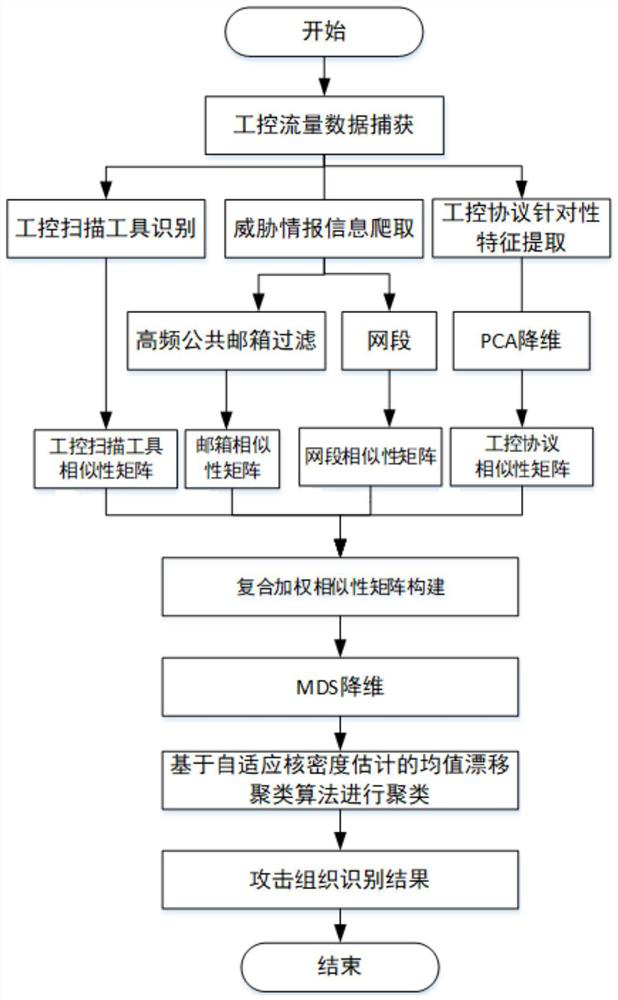
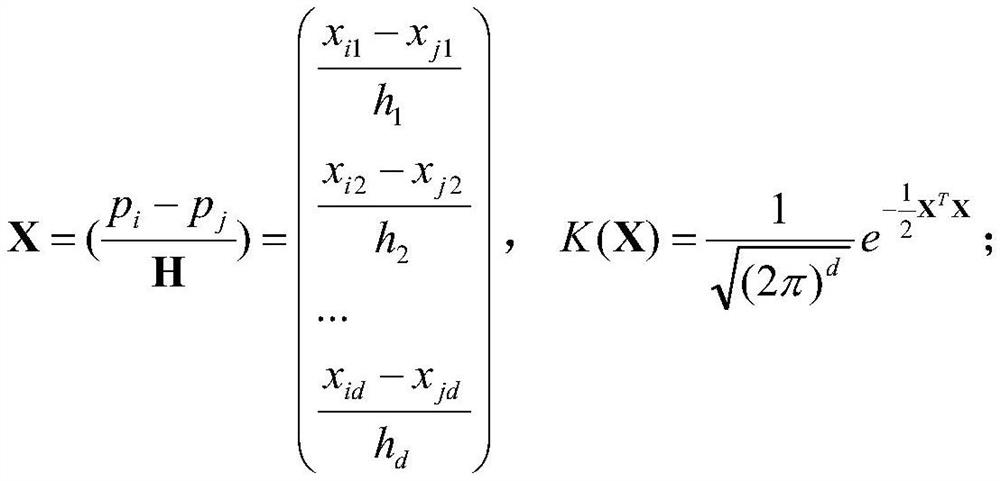
[0038] The present embodiment elaborates an algorithm flow of the present invention based on the analysis of industrial control traffic and threat intelligence correlation analysis of the attack organization when implemented in the case of implementation and application, the application of the industrial control honeypot attack IP organization identification problem in the field of network security.
[0039] Accurately identifying the attack organization to which the attacker belongs in the industrial control network can help the network security personnel to defend against the distributed attack of the attacking organization in a timely manner and ensure the safe and stable operation of the industrial control network. An attack organization identification method based on correlation analysis of industrial cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com