Data inspection method and device, terminal and storage medium
A data inspection and data technology, applied in the computer field, can solve problems such as database data inconsistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
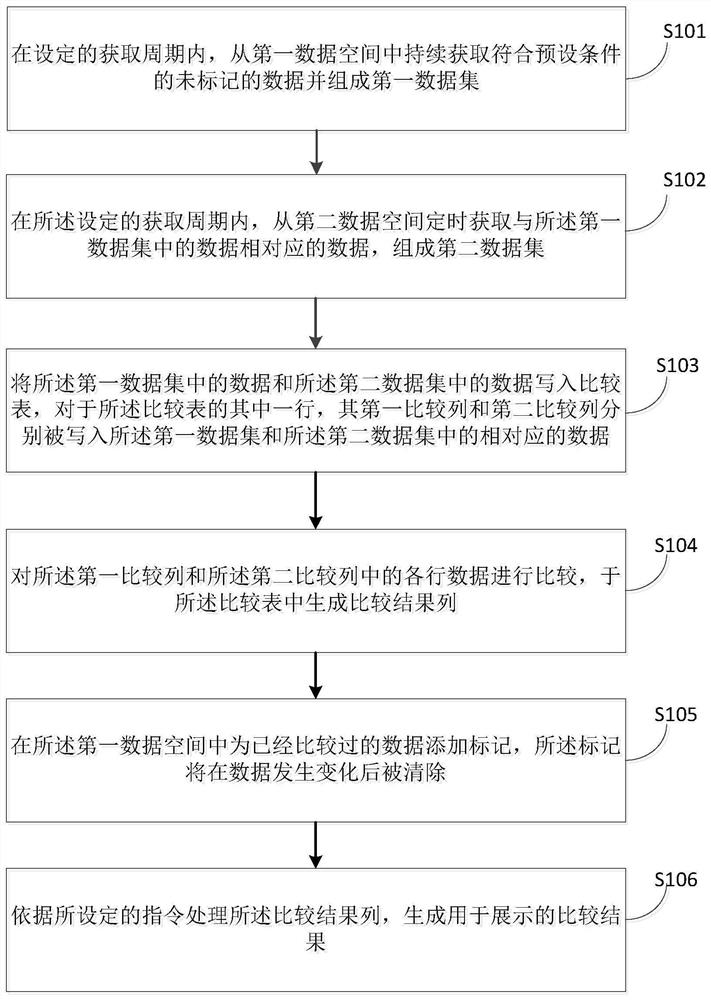
[0051] see figure 1 , the data verification method provided by the present disclosure may include the following steps S101 to S106:
[0052] In step S101, within a set acquisition period, continuously acquire unmarked data that meets preset conditions from the first data space and form a first data set;
[0053] In some implementations, the data may include data identification and data content.
[0054]Specifically, data identification can have multiple levels. Several lower-level data identifiers can be included under the high-level data identifiers.
[0055] For example, referring to Table 1, the company name of the company may be the primary data identifier. The business dimension of the company may be several secondary data identifiers under the primary data identifier.
[0056]
[0057] Table 1
[0058] Take Table 2 as a specific example: the company name "QianX Technology" is a primary data identifier, and several business dimensions of the company, "number of em...
Embodiment 2
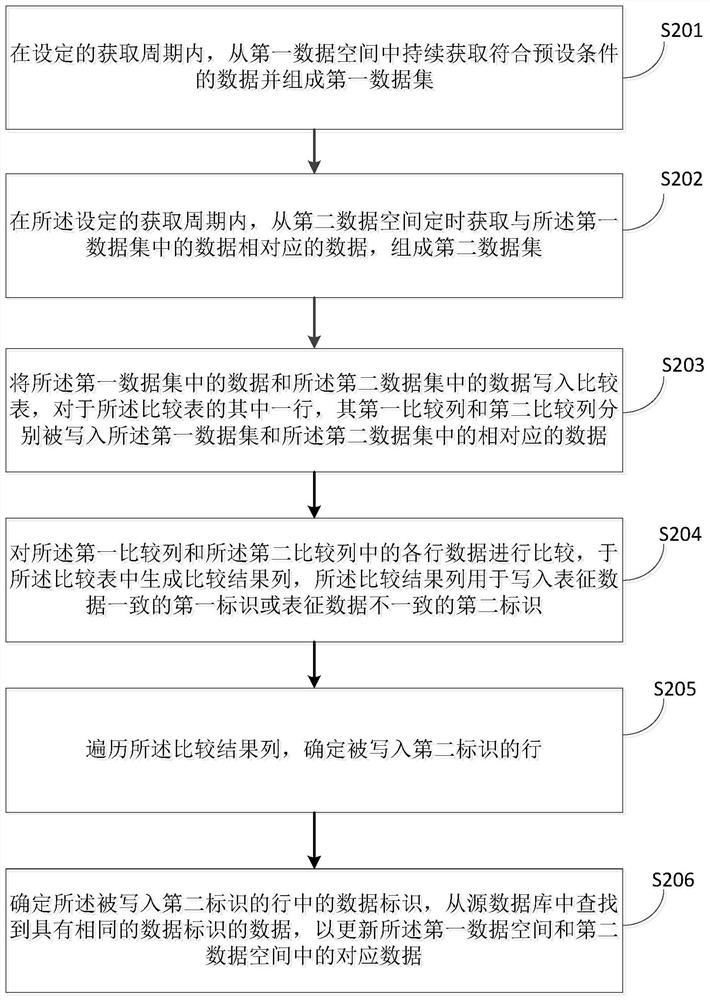
[0088] see figure 2 , the data verification method provided by the present disclosure may include the following steps S201 to S206:
[0089] In step S201, within a set acquisition period, continuously acquire data that meets preset conditions from the first data space and form a first data set;
[0090] In step S202, within the set acquisition period, periodically acquire data corresponding to the data in the first data set from the second data space to form a second data set;
[0091] In step S203, the data in the first data set and the data in the second data set are written into the comparison table, and for one row of the comparison table, the first comparison column and the second comparison column are respectively written into the corresponding data in the first data set and the second data set;
[0092] In step S204, the data of each row in the first comparison column and the second comparison column are compared, and a comparison result column is generated in the co...
Embodiment 3
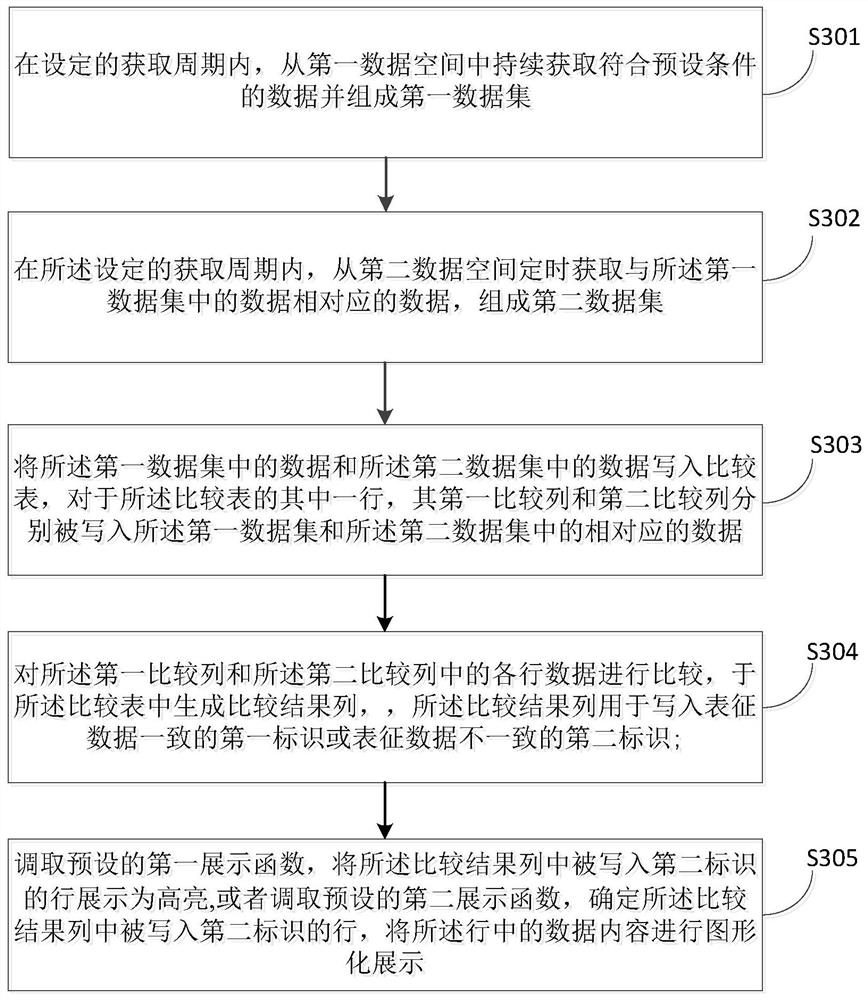
[0099] see image 3 , the data verification method provided by the present disclosure may include the following steps S301 to S306:
[0100] In step S301, within a set acquisition period, continuously acquire data that meets preset conditions from the first data space and form a first data set;
[0101] In step S302, within the set acquisition period, periodically acquire data corresponding to the data in the first data set from the second data space to form a second data set;
[0102] In step S303, the data in the first data set and the data in the second data set are written into the comparison table, and for one row of the comparison table, the first comparison column and the second comparison column are respectively written into the corresponding data in the first data set and the second data set;
[0103] In step S304, the data of each row in the first comparison column and the second comparison column are compared, and a comparison result column is generated in the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com