Database attack defense method, device and system
A database and intrusion attack technology, which is applied in the field of information security, can solve the problems of vigilance of intruders and affecting the defense effect, and achieve the effect of improving the protection ability, increasing the possibility of discovery, and improving the defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
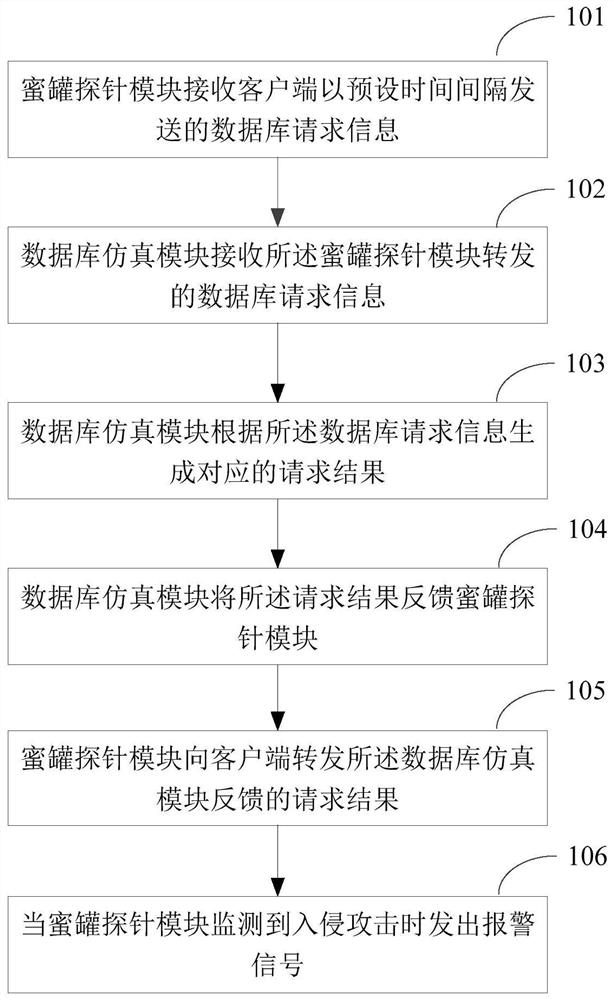
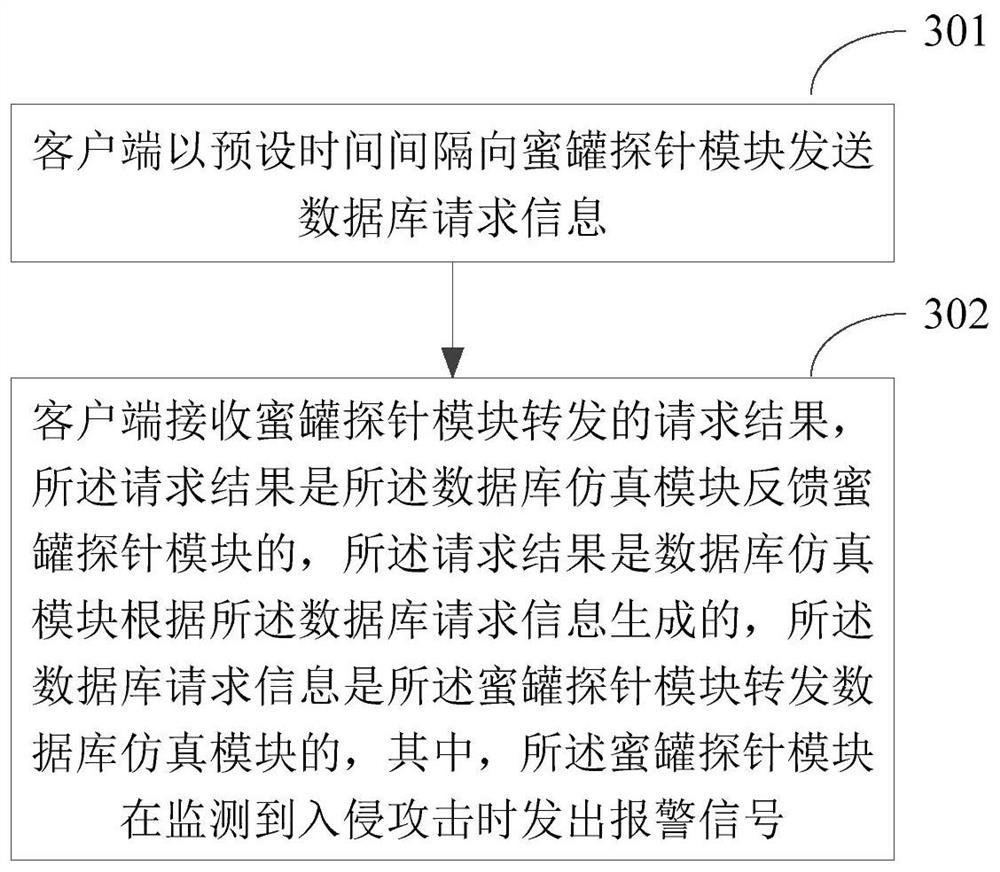
[0034] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. Here, the exemplary embodiments and descriptions of the present invention are used to explain the present invention, but not to limit the present invention.
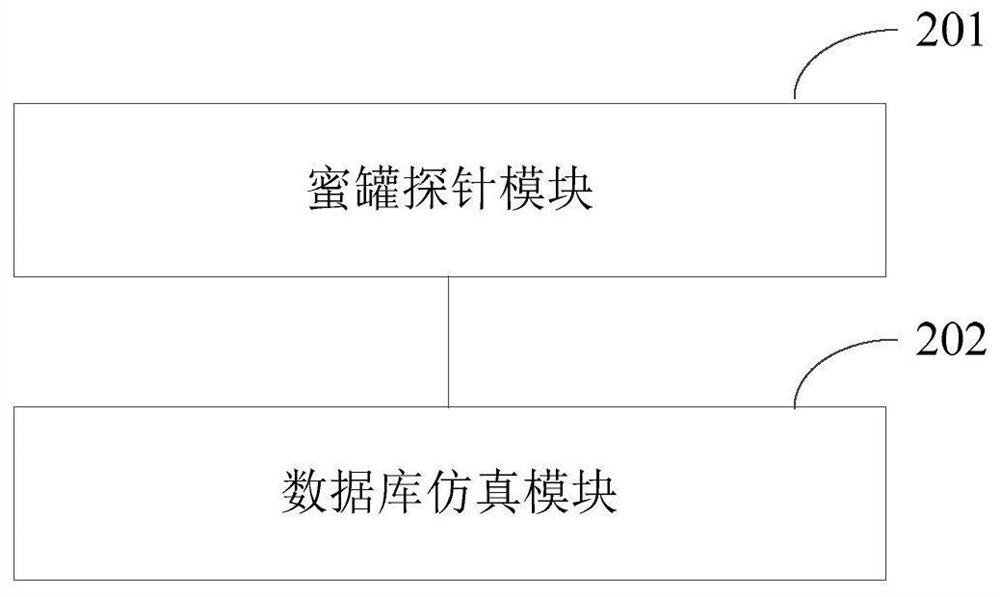
[0035] As mentioned above, a real host in a network environment should interact with other hosts in the network in real time. In these connection communications, intruders usually use data, personnel information, and high-privilege hosts as the primary targets of intrusion. Database interactions tend to be more attractive to intruders.
[0036] At present, the common solutions in the industry are mostly to place some breadcrumbs (similar to database or terminal configuration files, etc.) in some vulnerable servers or office environments that are easy to be phished. T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com