More efficient post-quantum signatures
A digital signature and vector technology, applied in the direction of public key of secure communication, digital transmission system, user identity/authority verification, etc., can solve the problems of expensive calculation, difficult message signature and verification message
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
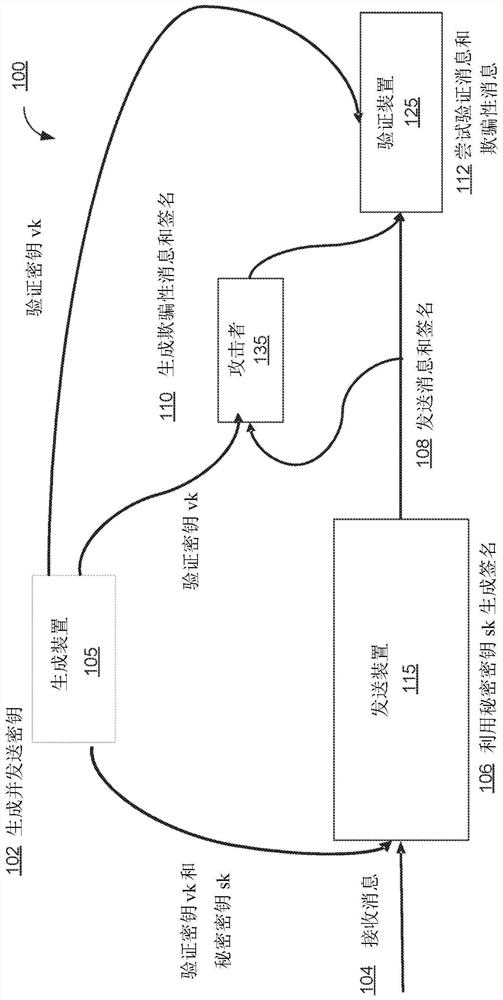
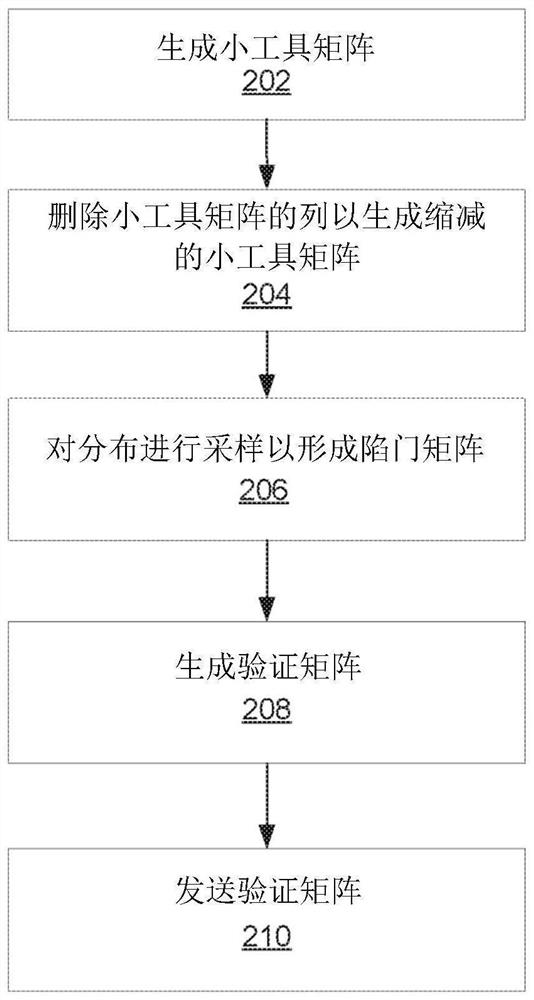
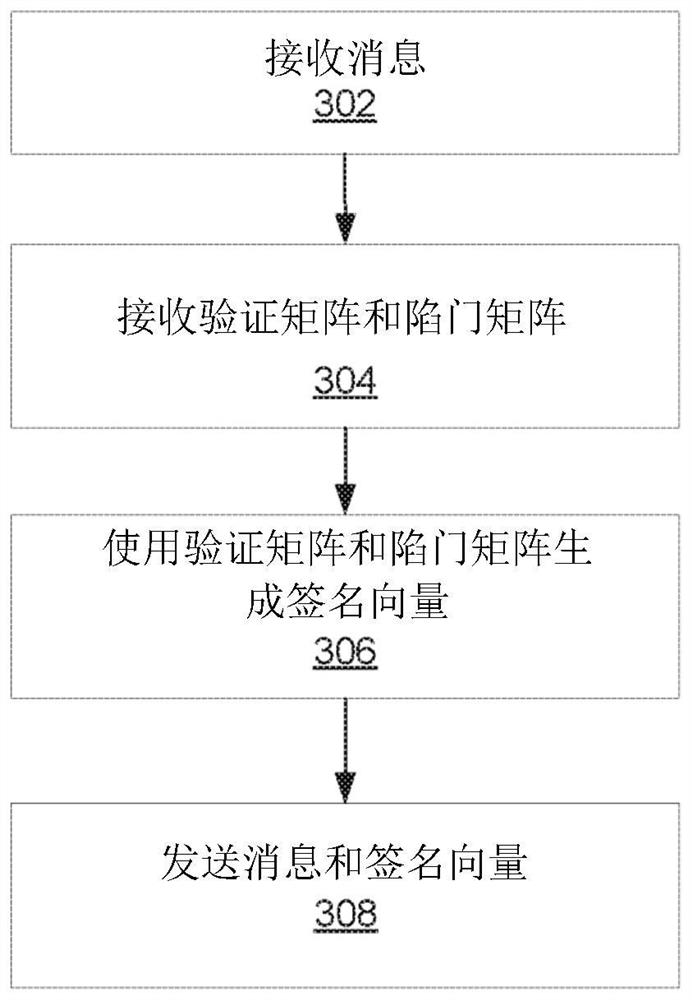
[0021] Based password, a problem-based password can provide a cryptographic solution, in particular with the development of quantum computing, the development of the quantum calculation may reduce the effect of more traditional cryptographic systems. The problem includes, for example, a non-uniform short-term solution (ISIS) problem involving finding the shortest vector in the N-dimensional grid of the point. Non-quasi-short integer solution (ISIS) problem requires a vector X that meets the relationship A · X = Y (Mod Q). In this example, the vector Y can be a hash of a message or message, and the vector X may be a signature associated with the message. The problem may be difficult to calculate - even with quantum calculations, this makes them very suitable for password applications. The use of the trap matrix may make it easier to solve the problem, which may be a matrix that makes a problem (e.g., ISIS problem) simply or becomes calculated within a reasonable time. In an example...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com