Secret information identification system
A technology for identifying systems and inputting information, applied in the field of personal information identification systems, to solve problems such as inability to use machines
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
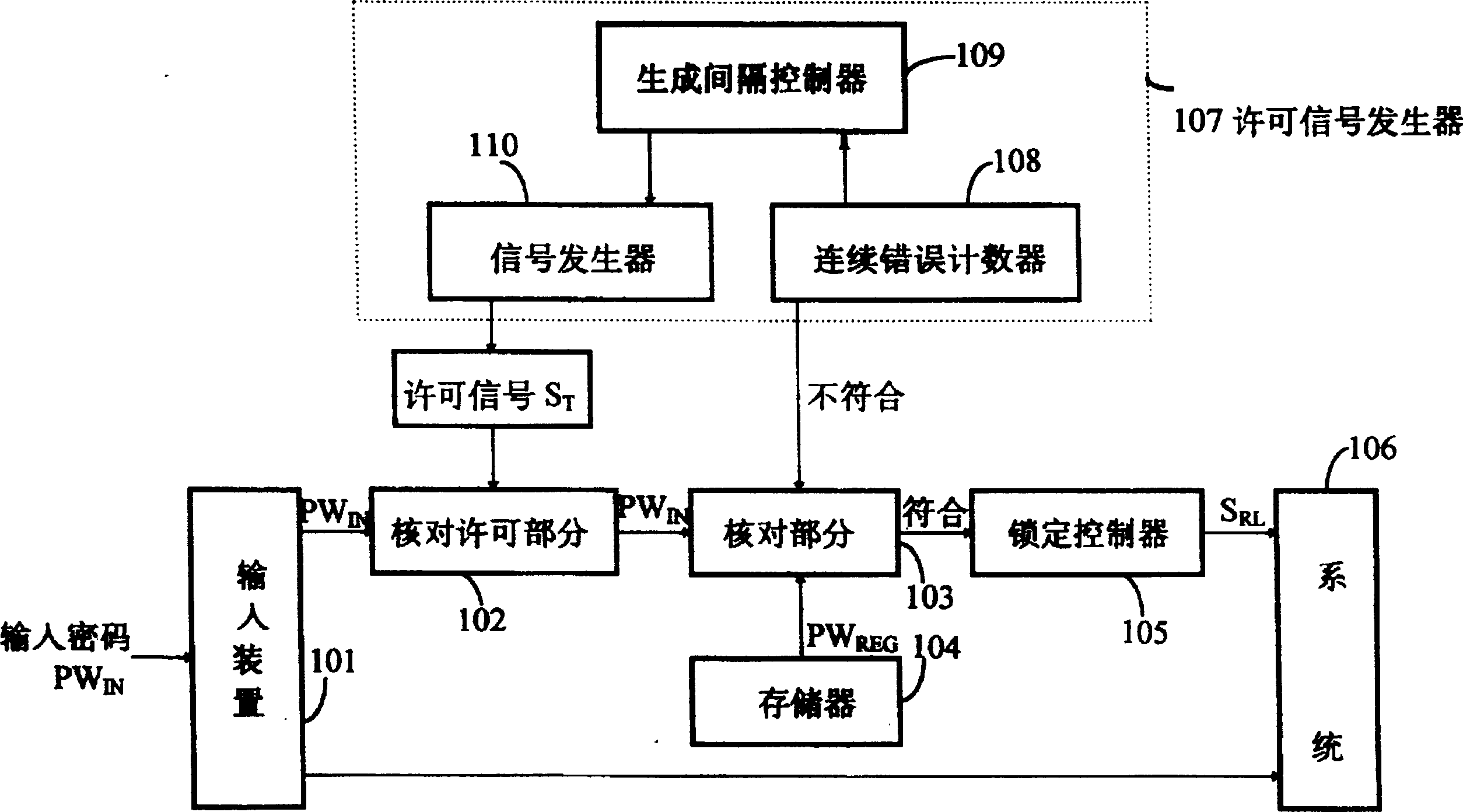
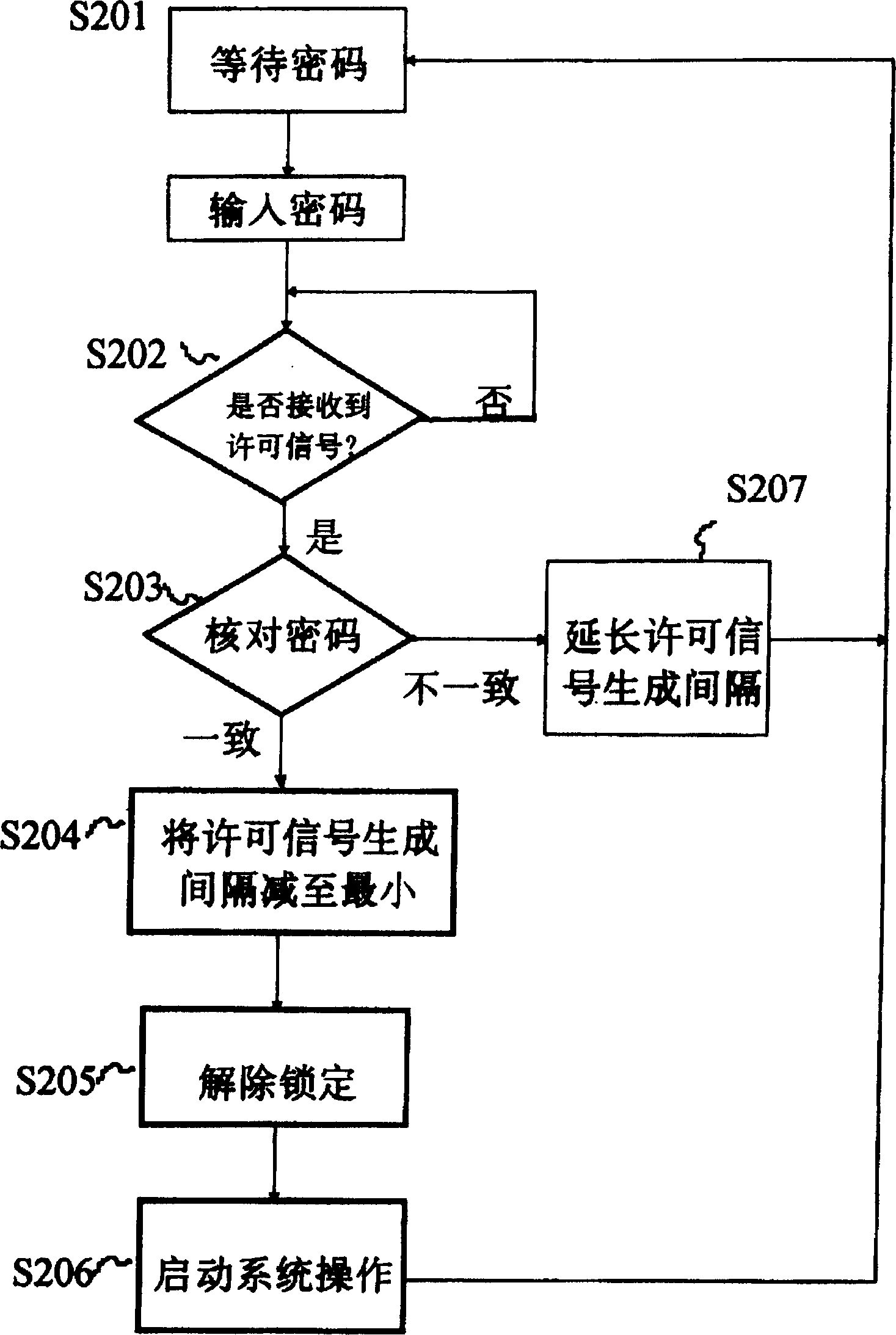
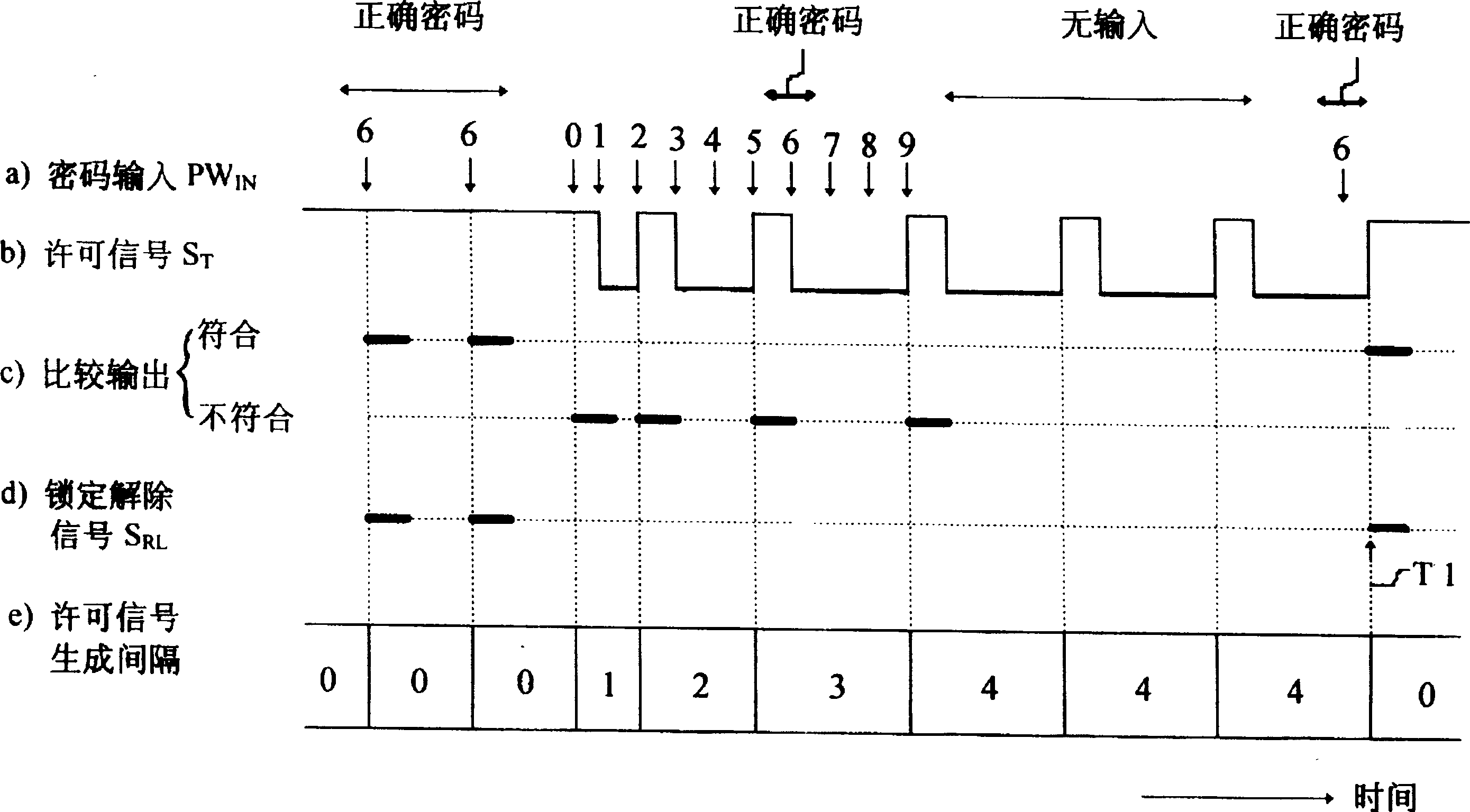
[0022] refer to figure 1 , the password identification system according to one embodiment of the present invention has the following structure. The user inputs the password PW using an input device 101 such as a keypad IN and other required information. The check permission section 102 will enter the password PW IN converted to a signal with permission S T Corresponding checking part 103. In other words, the check permission section 102 has T And the function of permitting-checking operation. The checking part 103 passes the input password PW IN and a registered password PW pre-stored in memory 104 REG Compare to the input password PW IN Check it out. When the comparison result is "consistent", the lock controller 105 releases the lock of the system 106 . The permission signal generator 107 receives the comparison result from the collation section 103 and changes the generated permission signal S according to the comparison result. T period and generate a permission...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com