Two-dimensional code secret sharing and restoration method and device based on (3,1) Hamming code
A technology of secret sharing and two-dimensional codes, which is applied in computer security devices, record carriers used by machines, instruments, etc., can solve problems such as failure, anti-fraud function defects, and meaningless barcodes of two-dimensional codes for secret sharing, and achieve good results. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
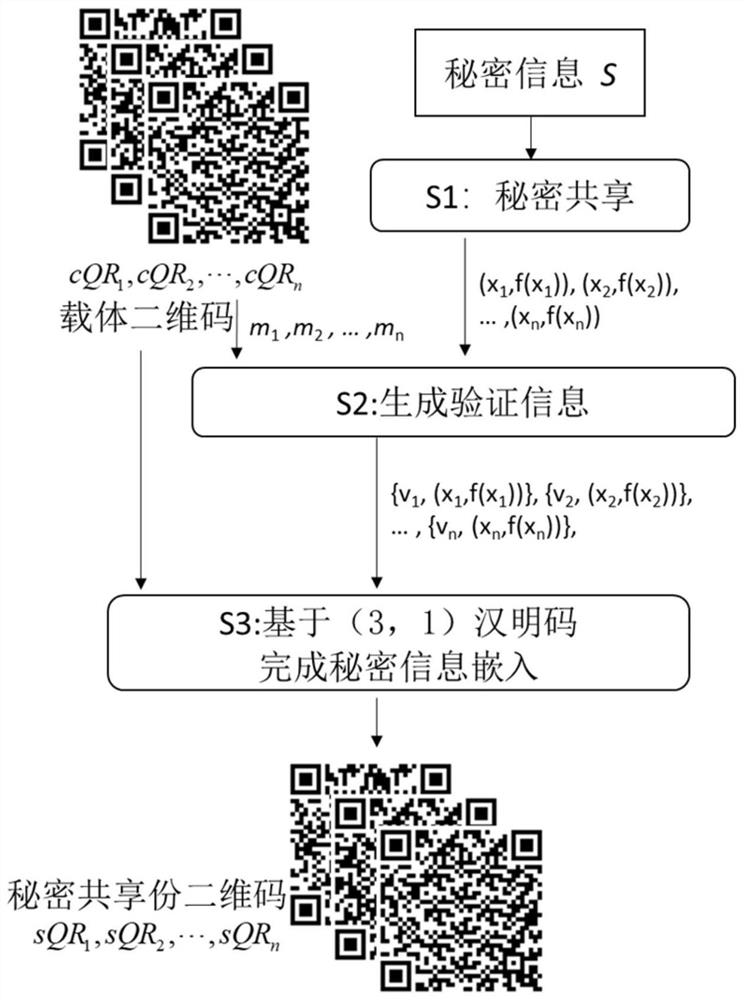
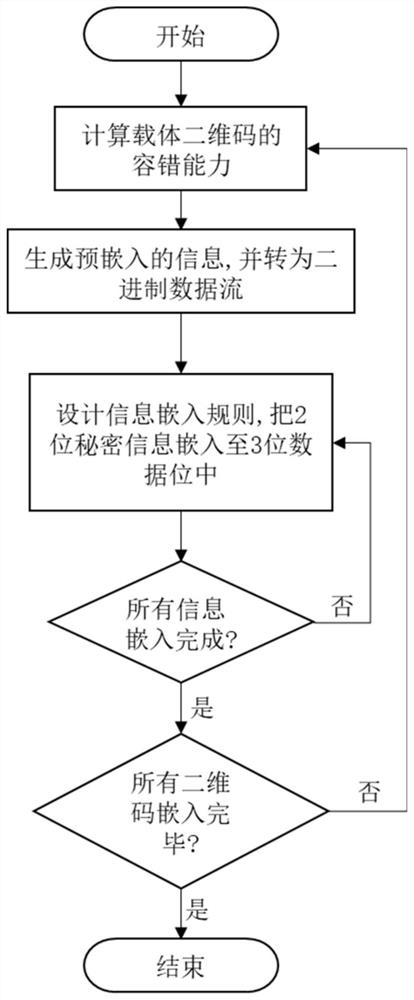
[0123] Step 1: According to the secret information S, use to generate n shares of secret information sharing (x i ,f(x i )).
[0124] In this embodiment, set k=3, n=3, 3 carrier QR codes refer to figure 2 . Among them, the versions of the three carrier QR codes are all 5-M, which contain meaningful content information, respectively: "www.bing.com", "www.google.com" and "www.yahoo.com" ;The secret information is: 1234567890.
[0125] The specific process is as follows:
[0126] Step 1.1: Split the secret information S into three non-repetitive secret information blocks; s 0 =12345,s 1 =678 and s 2 =90.
[0127] Step 1.2: According to the constraints, set the prime number p to 18251.
[0128] Step 1.3: Based on prime number p and n copies of secret information block s i , construct a polynomial equation f(x);
[0129] f(x)=12345+678*x+90*x 2 (mod18251)
[0130] Step 1.4: Generate 3 random numbers x 1 ,x 2 ,...,x n , into the polynomial equation f(x). Three secr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com