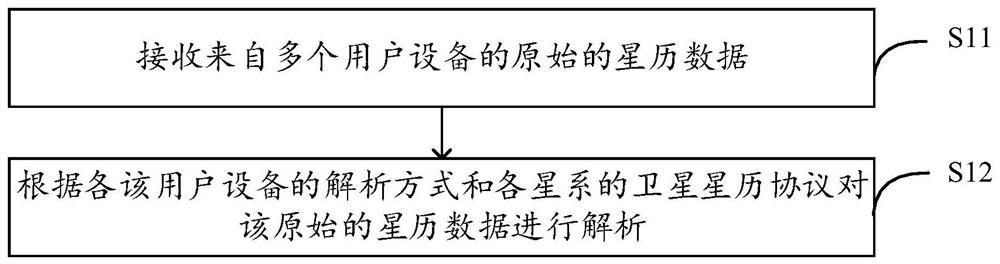
Ephemeris data processing method and device, equipment and storage medium
A technology of ephemeris data and processing method, applied in the fields of navigation, satellite communication, positioning, and computer, which can solve the problems of poor real-time performance and achieve the effect of enriching ephemeris data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0048]16,257,1,-1,2,34,-64,89,60,30,-11,-22,-108,18,1,-38,-84,11,-73,-121,-83, 62,-44,-11,-76,1,-80,-127,-72,6,-79,-21,83,2,102,-88,83,3,62,-4,-50,23 ,74,-97,-21
[0049] The above example is the message data of a GPS satellite. The first data after comma separation is the satellite number (16), the second data is the type (257, indicating GPS), and the rest of the data are binary byte data output data. The specific meaning can be obtained through further analysis.
example 2
[0051] 18,769,1,1,13,110,65,-14,105,-21,116,-64,47,52,99,40
[0052] The above is the message data of a GLONASS satellite. The first two digits separated by commas are the satellite number (18) and type (769, indicating GLONASS), and the remaining data is the data after binary byte data output. The specific meaning can be obtained through further analysis.
[0053] In an implementation manner, for binary message data, specific format conversion may be performed for different chips and different satellite systems.
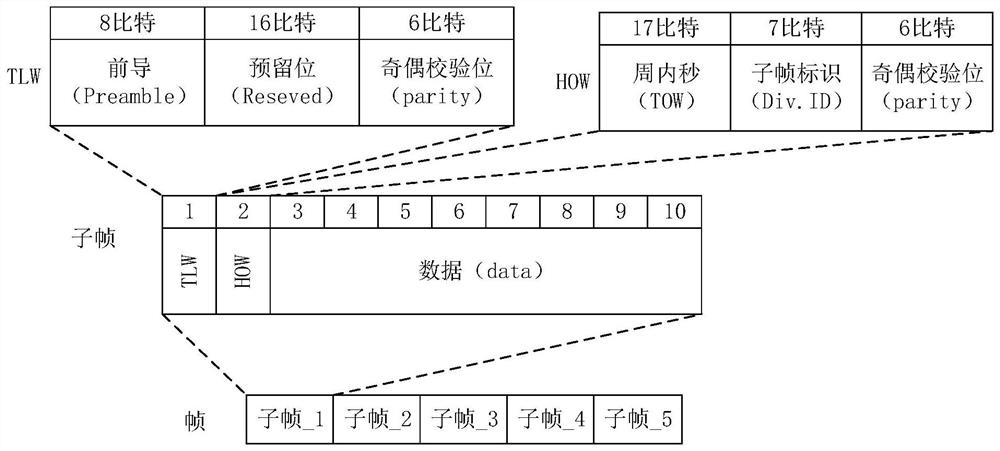
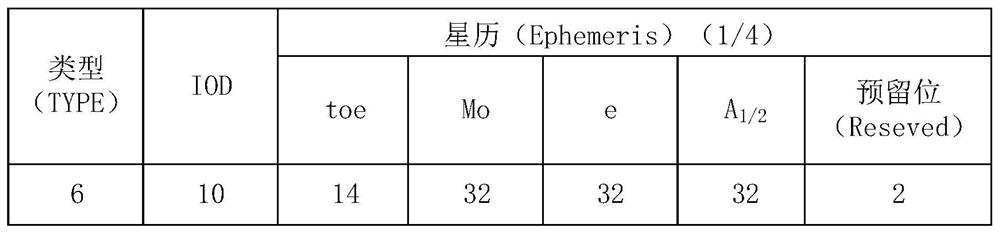
[0054] For example, see Figure 2a , in the complete ephemeris of a GPS satellite, the navigation message (Navigation Message) may include multiple frames of data. One frame may include 1500 bits of data, and one frame may be further divided into five sub-frames (Sub-frames), each of which has a length of 300 bits. The subframe may include TLW (Telemetry word, telemetry word), HOW (Hand over word, handover word), data (data), and so on. Wherein, the TLW may incl...
Embodiment approach
[0069] In one embodiment, the method also includes:
[0070] S42. Authenticate the ephemeris data acquisition request;
[0071] S43. In the case of passing the authentication, analyze and judge the validity of the ephemeris data acquisition request;
[0072] S44. When the analysis and legality judgment are successful, search the database for the ephemeris data corresponding to the ephemeris data acquisition request.
[0073] Exemplarily, in S41, after receiving the ephemeris data acquisition request from the target device, the server can use the device information and / or user information carried in the ephemeris data acquisition request to perform authentication to determine the ephemeris data acquisition request. Whether the request is from an authorized device and / or an authorized user. If it is from an authorized device and / or an authorized user, it can be determined that the authentication is passed. If the authentication is passed, the ephemeris data acquisition reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com