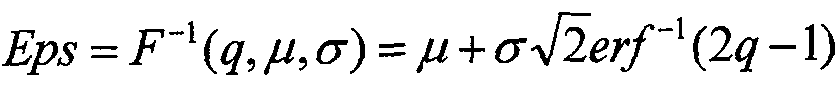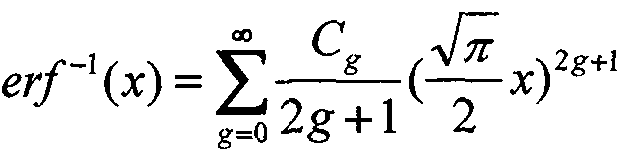Track clustering privacy protection method based on semantics
A privacy protection and trajectory clustering technology, which can be used in specific environment-based services, digital data protection, vehicle wireless communication services, etc., and can solve the problem of not considering privacy protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
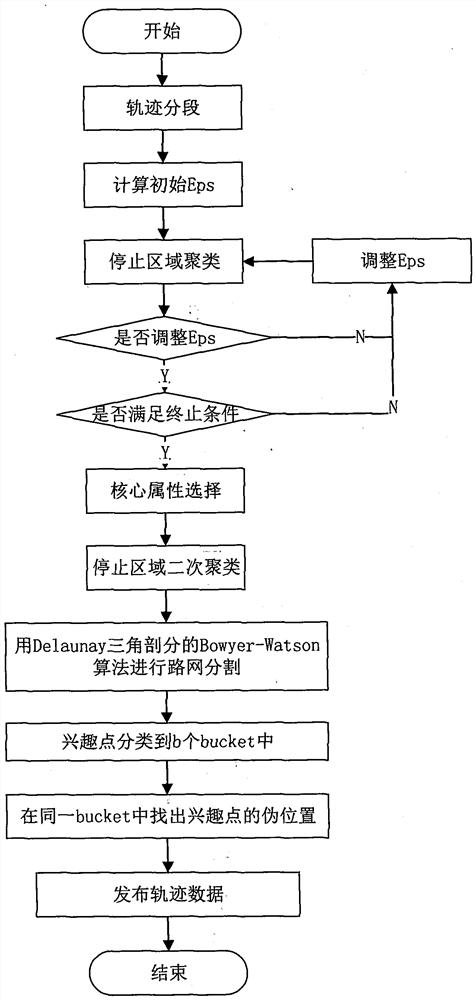
[0060]The invention will be further described in detail below with reference to the accompanying drawings:
[0061]Such asfigure 1As shown, a semantic-based trajectory cluster privacy method includes the following steps:
[0062]Step 1, trajectory segmentation;
[0063]1.1 Search the cluster in a single marker trajectory according to the direction and speed changes. Calculate two-point P in a single marker trajectoryi-1PiDuan direction changes (DC (p)i-1, Pi)) And speed changes (SC (Pi-1, Pi)), Where DC (Pi-1, Pi) = | DC (pi-1) -DC (pi), Sc (pi-1, Pi) = | V (pi-1) -V (p)i) |, V (pi)iTime point Pispeed.
[0064]Original trajectory: indicating the time-space sampling point sequence of time intervals:
[0065]P = {P0= (X0Y0, T0), P1= (X1Y1, T1), ..., pn= (XnYn, Tn}
[0066]Set Pi= (XiYi, Ti) For some sampling point in the trajectory, where XiIndicates the sampling point PiSlender, yiIndicates the sampling point PiThe latitude, TiIndicates the sampling point PiThe sampling time, n represents the number o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com