Method and system for fusing network threat intelligence metadata
A technology of intelligence data and metadata, which is applied in transmission systems, text database indexing, electronic digital data processing, etc., can solve the problems of rough fusion granularity and inflexible result output, and achieve good user experience effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
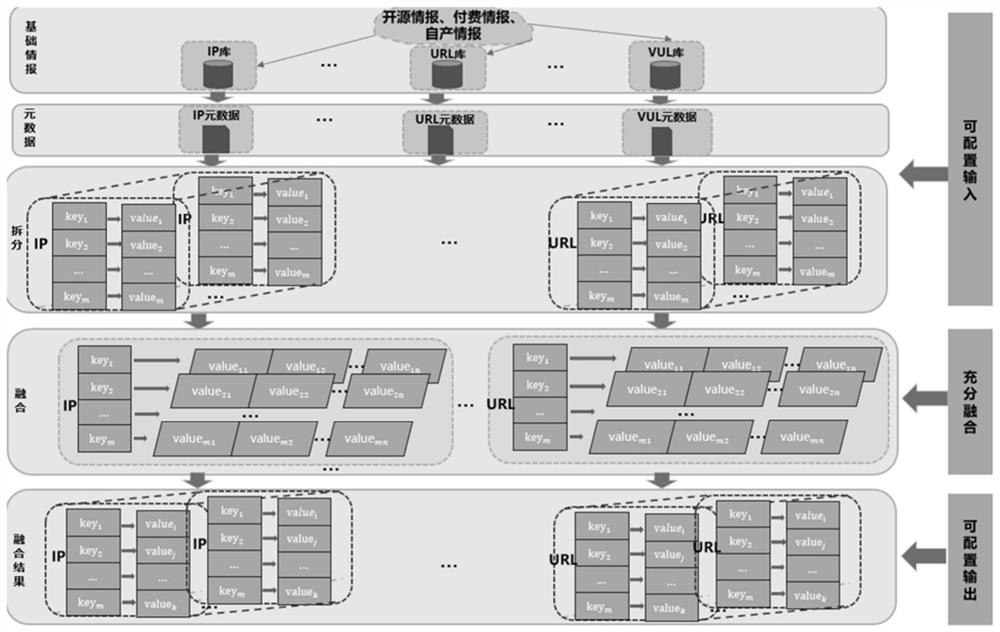
[0036] In order to make the technical solutions, features and advantages of the present invention clearer and easier to understand, the technical details of the present invention will be further described below in conjunction with the accompanying drawings.
[0037] The method for fusion of network threat intelligence metadata of the present invention comprises the following steps:
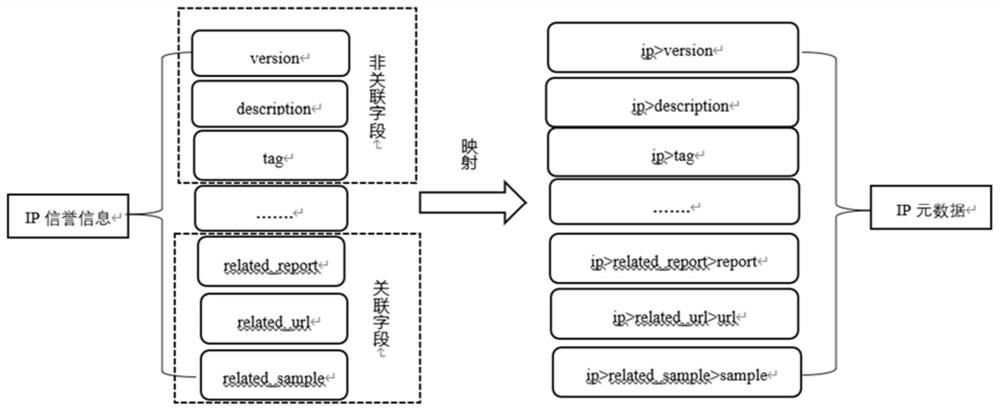
[0038] (1) First, obtain cyber threat intelligence data from various intelligence sources, including: open source intelligence, purchased paid intelligence, and self-produced intelligence. Since these intelligence data are unstructured, if automated processing is to be performed, these cyber threat intelligence data need to be standardized, that is, transformed into structured cyber threat intelligence data. With reference to international standards, OpenIOC, IODEF (Incident Object Deion and Exchange Format), STIX (Structure Threat Information eXpression) and actual business needs, the network thr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com