Behavior prediction method of network attack knowledge graph generated based on honeypot actual combat
A network attack, knowledge graph technology, applied in knowledge expression, data exchange network, character and pattern recognition, etc., can solve the problem of ineffective analysis of attack behavior.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
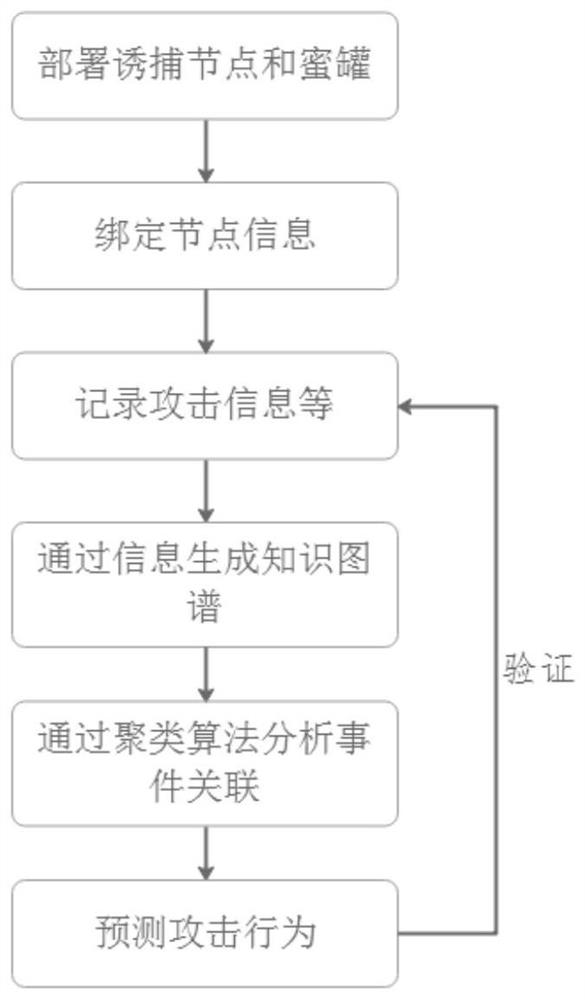
[0052] This embodiment provides a network attack knowledge map and behavior prediction method generated based on honeypot actual combat, including the following steps:
[0053] S1: Deploy trapping nodes and honeypots, bind node information, and record all attack information after being attacked, where attack information includes attack behavior, attack source IP and port, attack method, attack content, and attack time; The node information is to bind the trapping node and the honeypot, and record the node IP and the honeypot IP.
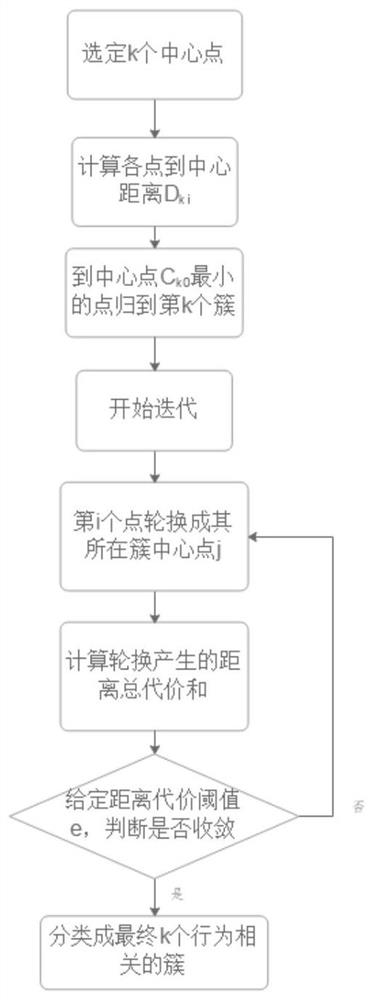
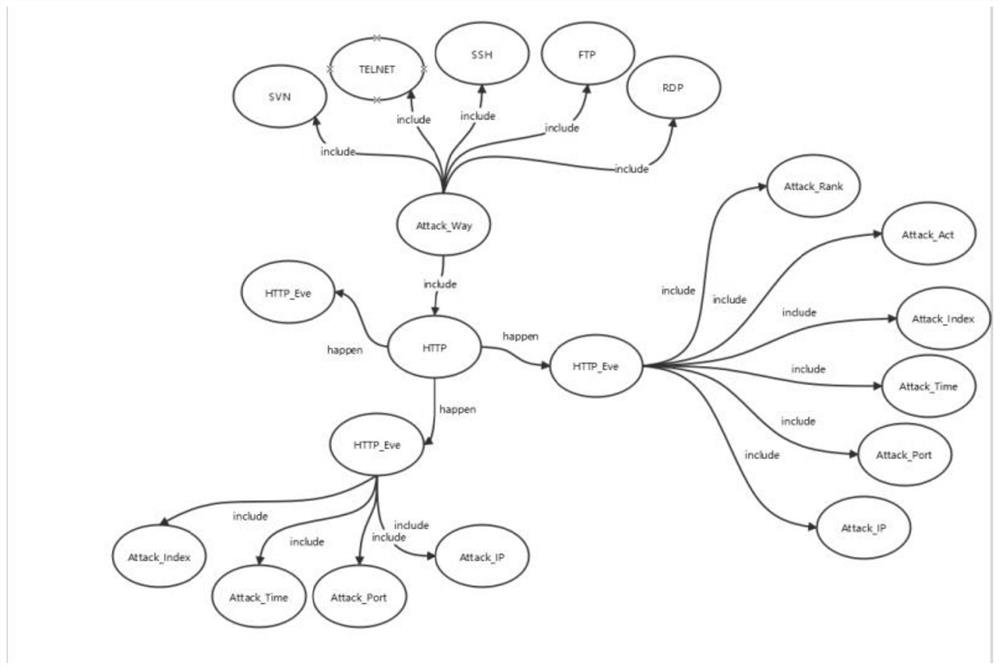
[0054] S2: Construct the knowledge map of the attack information recorded in step S1. The map construction method is as follows: divide all attack information into first-level nodes M1 according to attack types, which include SSH scanning attacks, Http attacks, and FTP attack events; second The first-level node M2 includes a single attack event; the third-level node M3 includes the collection of attack IP, attack port, attack time, attack sequence,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com