Network traffic monitoring and auditing method and system
A network traffic and traffic technology, applied in the field of network security, can solve the problems of difficult operation and maintenance deployment and high deployment complexity in the whole process of competition monitoring, so as to solve the deployment complexity, reduce the burden of operation and maintenance and referees, and reduce the difficulty of deployment. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention is described in detail below in conjunction with examples, but the present invention is not limited to these examples.
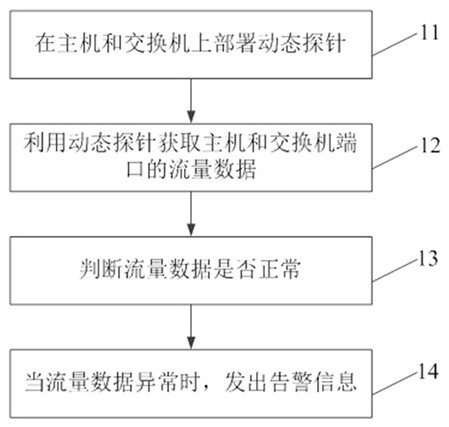
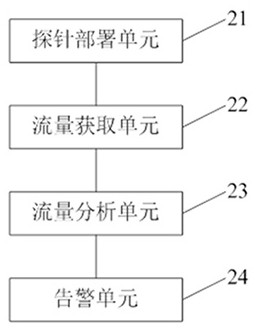
[0019] Embodiments of the present invention provide a method for monitoring and auditing network traffic, such as figure 1 As shown, the method includes:
[0020] Step 11, deploying dynamic probes on hosts and switches;
[0021] Step 12, utilize dynamic probe to obtain the flow data of host computer and switch port;
[0022] Step 13, judging whether the traffic data is normal;
[0023] Step 14, when the traffic data is abnormal, send out an alarm message.
[0024] The dynamic probe deployment scheme mainly includes the deployment of the probe host audit function in the physical host and virtualization environment. In this way, the dynamic scene port traffic can be collected, so as to analyze the traffic data.
[0025] By collecting the traffic data of the host and the switch port, the data of the game process is analyzed to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com