Malicious group determination method and device, electronic equipment and storage medium
A technology for determining methods and groups, applied in the computer field, can solve problems such as rapid occurrence time and difficulty in effectively finding malicious groups, and achieve the effect of improving efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
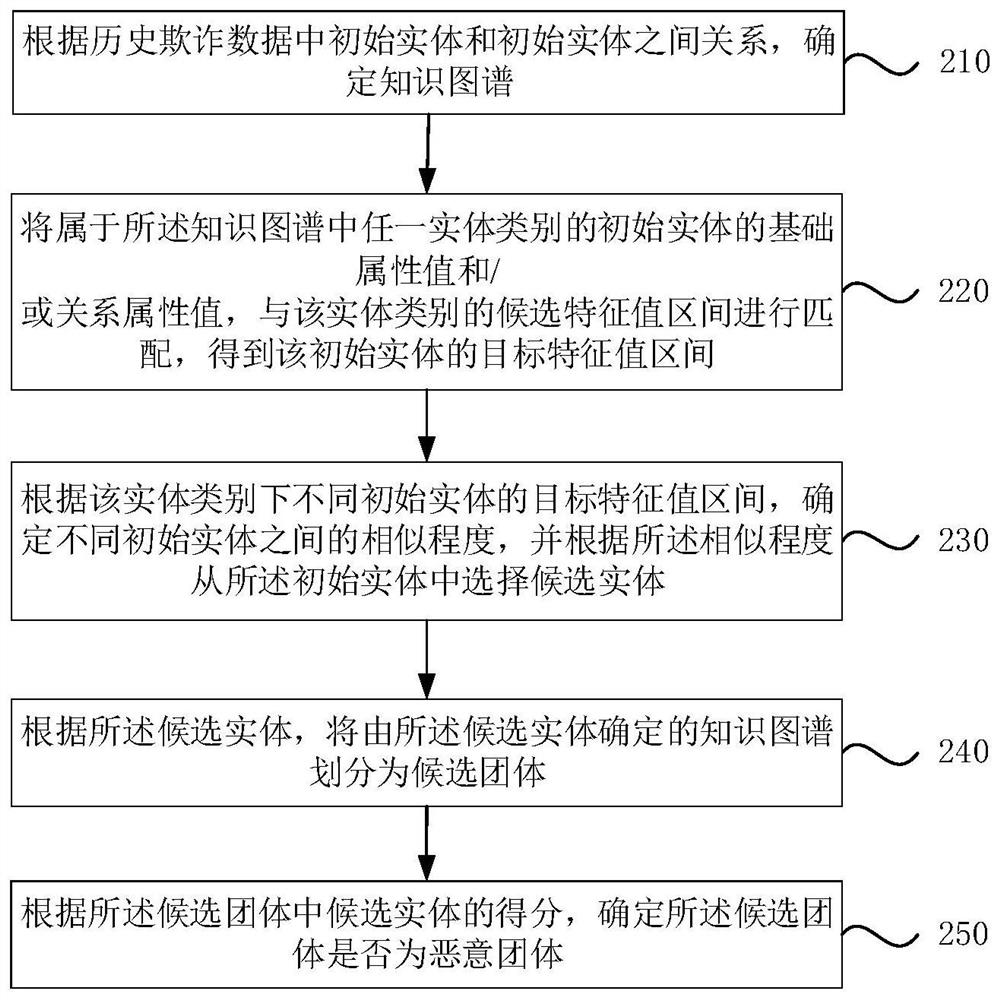
[0027] figure 1 It is a flow chart of a method for determining a malicious party provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of determining a malicious party from historical fraud data. This method can be implemented by the device for determining a malicious party provided in this embodiment Execution, the device may be implemented by software and / or hardware. see figure 1 , the method for determining a malicious group provided in this embodiment includes:
[0028] Step 110, determine the knowledge graph according to the relationship between the initial entity and the initial entity in the historical fraud data.
[0029] Wherein, the historical fraud data is data that has been determined to be related to fraudulent behavior, such as fraudulent transactions, fraudulent accounts, and the like. The initial entity is an entity object obtained based on historical fraud data. For example, if the historical fraud data is fraudu...
Embodiment 2
[0062] figure 2 It is a flow chart of a method for determining a malicious party provided by Embodiment 2 of the present invention. This technical solution is supplementary explanation for the process of determining the degree of similarity among different initial entities in the knowledge map. Compared with the above scheme, the specific optimization of this scheme is to determine the similarity between different initial entities in the knowledge map, including:
[0063] Matching the basic attribute value and relational attribute value of the initial entity belonging to any entity category in the knowledge graph with the candidate feature value range of the entity category to obtain the target feature value range of the initial entity;
[0064] According to the target eigenvalue intervals of different initial entities under the entity category, the similarity between different initial entities is determined. Specifically, the flow chart of the malicious group determination...
Embodiment 3
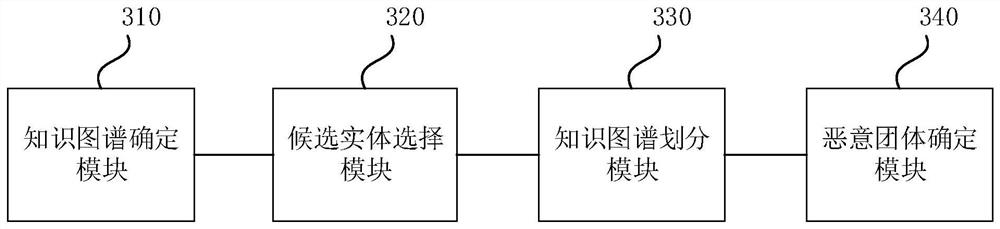
[0082] image 3 It is a schematic structural diagram of a malicious party device provided by Embodiment 3 of the present invention. The device can be realized by hardware and / or software, can execute a malicious party method provided by any embodiment of the present invention, and has corresponding functional modules and beneficial effects for executing the method. like image 3 As shown, the device includes:
[0083] The knowledge map determination module 310 is used to determine the knowledge map according to the relationship between the initial entity and the initial entity in the historical fraud data;
[0084] A candidate entity selection module 320, configured to determine the degree of similarity between different initial entities in the knowledge graph, and select candidate entities from the initial entities according to the degree of similarity;
[0085] A knowledge graph division module 330, configured to divide the knowledge graph determined by the candidate enti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com