Data tamper-proofing method and system based on abstract algorithm
A digest algorithm and anti-tampering technology, applied in the field of network security, can solve problems such as loss, reduce storage space, improve system security, and increase algorithm complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings.
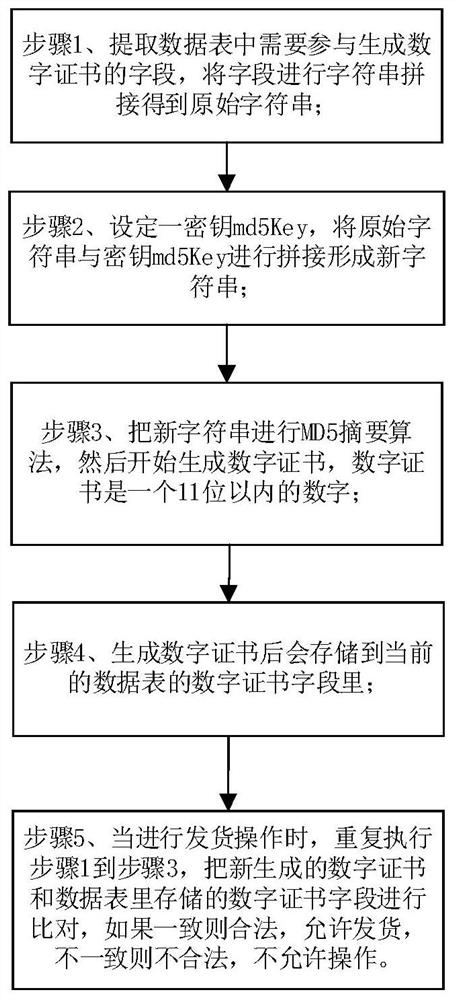
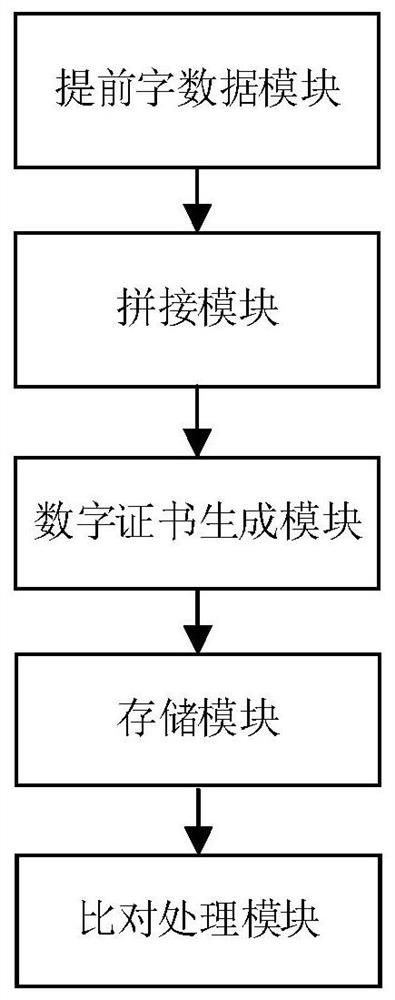
[0031] see figure 1 Shown, a kind of data tamper-proof method based on summary algorithm of the present invention, described method comprises the following steps:
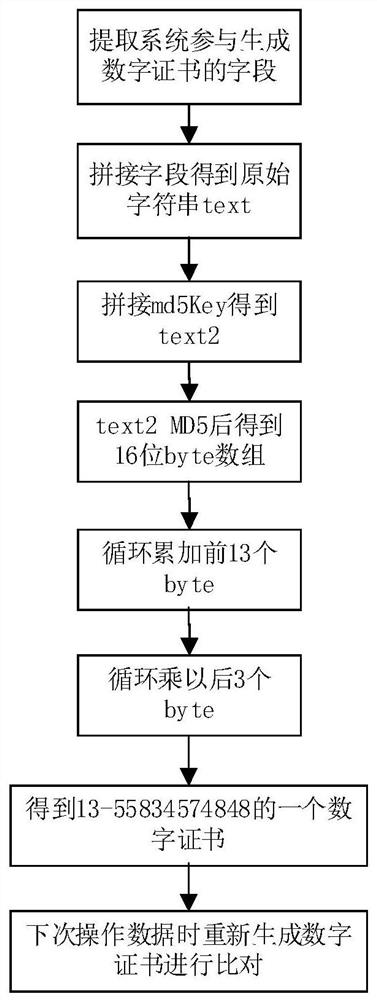
[0032] Step 1. Extract the fields in the data table that need to participate in the generation of digital certificates, and concatenate the fields to obtain the original string;
[0033] Step 2. Set a key md5Key, and splice the original character string with the key md5Key to form a new character string;
[0034] Step 3. Perform the MD5 digest algorithm on the new string, and then start to generate a digital certificate, which is a number within 11 digits;
[0035] The step 3 is further specifically:
[0036] Step 3.1: Perform MD5 with the new string to obtain a byte array with a length of 16;
[0037] Step 3.2: Circularly accumulate the first 13 byte arrays to obtain a first value between 13 and 3328. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com