Electronic evidence analysis system
An electronic evidence and analysis system technology, applied in other database clustering/classification, data processing applications, other database retrieval, etc., can solve the problems of inability to deeply mine electronic evidence data, data omission, etc., and achieve the effect of protecting rights and interests.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
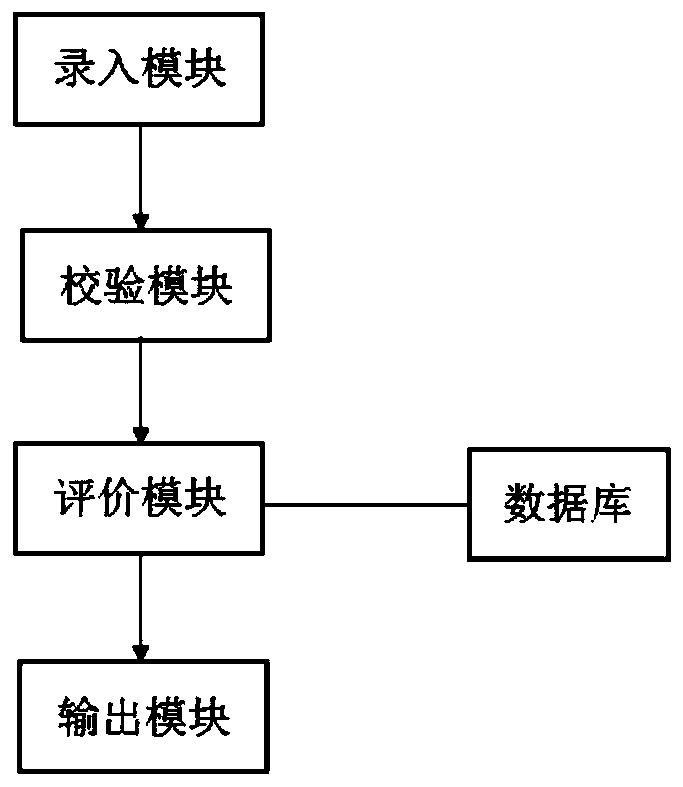
[0021] An embodiment of an electronic evidence analysis system of the present invention is basically as attached figure 1 As shown, it includes acquisition module, verification module, evaluation module, database and output module.
[0022] The database stores a large number of typical cases, case templates, laws and regulations, and judicial interpretations. These typical cases are generally guiding cases issued by the Supreme People's Court or very representative cases issued by local high people's courts, and can be processed in real time. renew.
[0023] The input module inputs the collected electronic evidence data (such as contracts, IOUs, IOUs, recordings, and videos) into the verification module. For example, the content of these electronic evidence is as follows:
[0024] "...Zhang San purchased 5 tons of cement from Li Si on April 1, 2008, and signed a cement sales contract on the same day. The contract stipulated that within 15 days, Li Si would transport the ceme...
Embodiment 2
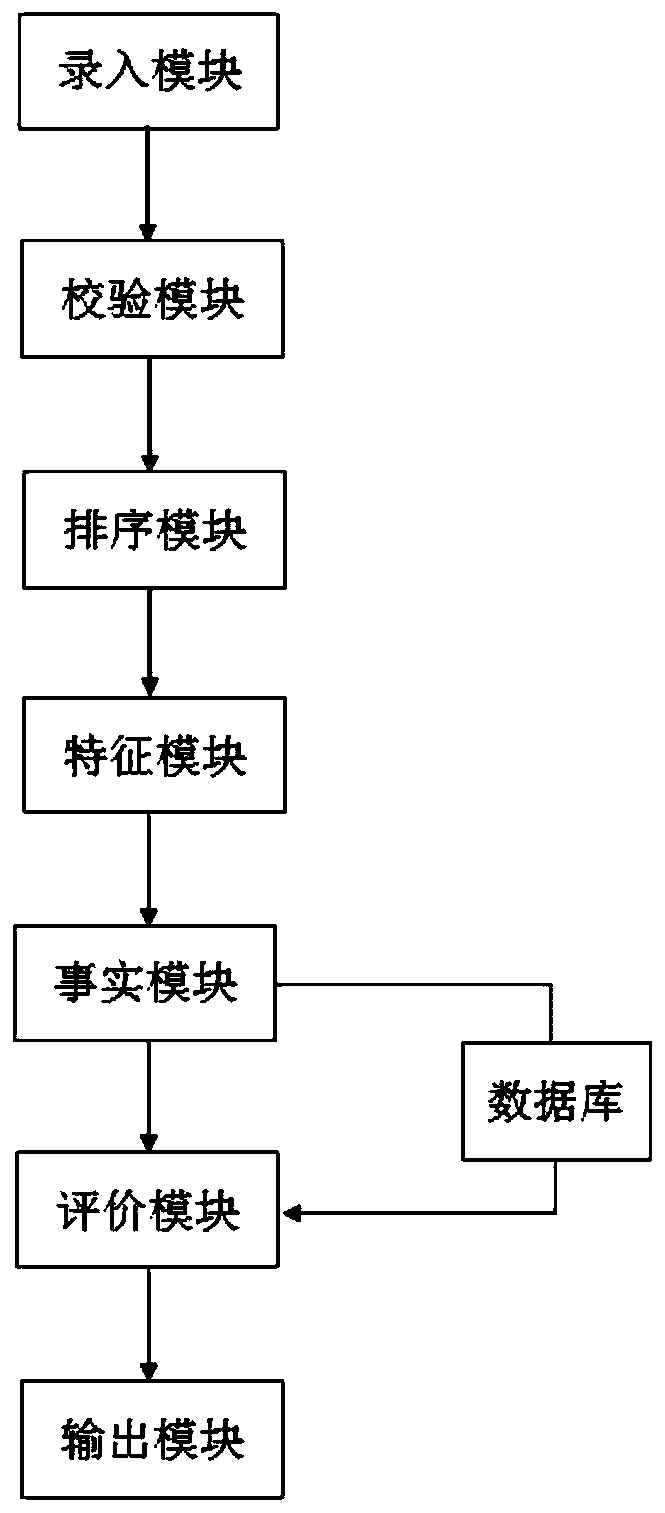
[0031] The only difference from Embodiment 1 is that it also includes a sorting module, a feature module, and a fact module, as attached figure 2 shown.
[0032] The input module sends the electronic evidence data to the sorting module. After the sorting module receives the electronic evidence, it extracts the hidden time features in the electronic evidence data, that is, the production time of the electronic evidence data; and sorts and stores the electronic evidence data according to the order of production time. For example, the above-mentioned electronic evidence is arranged as follows: on April 1, 2008, the contract, the audio recording of signing the contract, and the video of signing the contract; on April 16, 2008, the IOU, the recording of the delivery of cement and the IOU, and the video of the delivery of the cement and the IOU; April 28, 2008, IOU. Then, the sorted electronic evidence data is sent to the feature module.
[0033] After receiving the sorted elect...
Embodiment 3
[0040] The only difference with Embodiment 2 is that the evaluation module also includes a vulnerability unit, a risk unit, a suggestion unit and a learning unit; the vulnerability unit is used to check whether there is a loophole in the evidence chain with a time difference; and the vulnerability information is sent to the risk unit; the risk unit It is used to receive vulnerability information and assess whether there is legal risk based on the vulnerability information; and send the legal risk information to the suggestion unit; the suggestion unit is used to receive the legal risk information and generate suggestions based on the legal risk information; the learning unit is used to check the vulnerability , legal risk information assessment and recommendation generation process.
[0041] In this embodiment, the loophole unit checks the loopholes in the evidence chain according to the time difference. For example, Li Si said that he would set off on June 14 and transport th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com