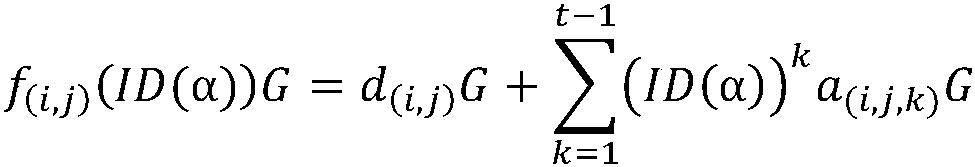Double-threshold signature method based on ECDSA
A dual-gate, node technology, applied in user identity/authority verification and key distribution, can solve the problems of inability to obtain rights and reduce the security of the scheme.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0102] The purpose and effects of the present invention will become clearer by describing the present invention in detail according to the accompanying drawings and preferred embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
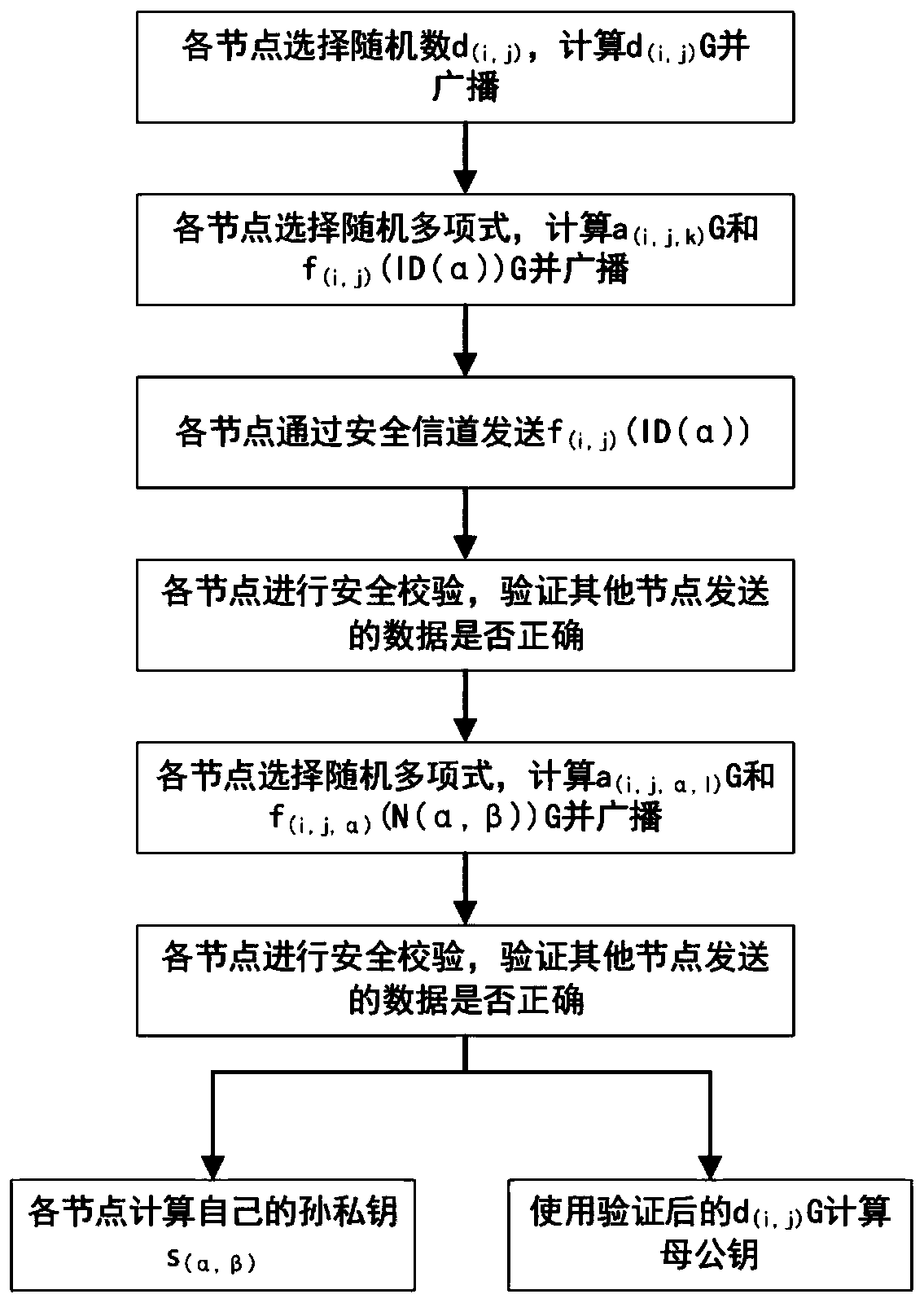
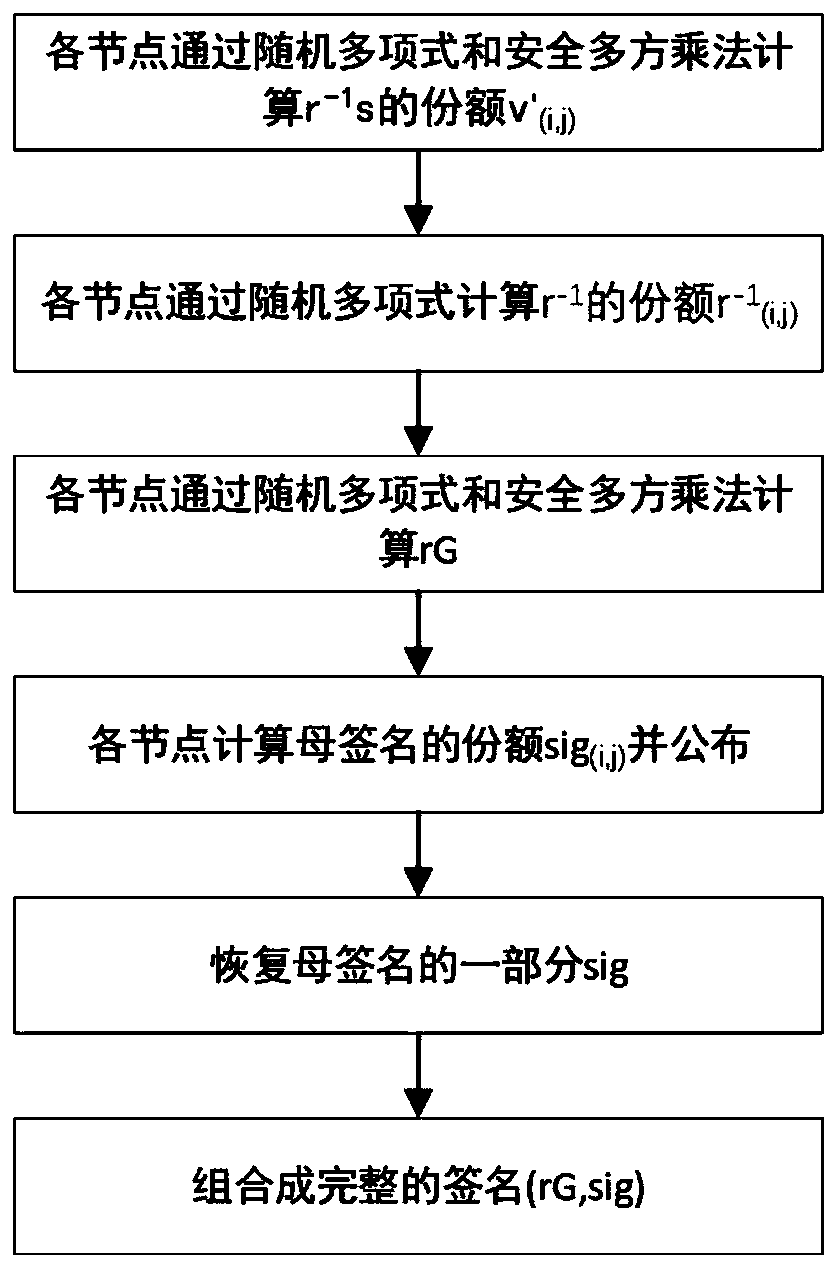
[0103] The ECDSA-based double-threshold signature method of the present invention is mainly composed of two parts: generating a parent public key and a grandson private key and synthesizing a signature. The first part is equivalent to the initialization of the system, and the second part is equivalent to the use of the system.
[0104] 1. Generate parent public key and grandson private key (such as figure 1 shown)
[0105] In this process, (i, j) is used to represent a certain node, i represents the large group where the node is located, and j represents the serial number of the node in the large group, (α, β) is used to represent another ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com