Virtual key sharing method, device and system, equipment and storage medium
A virtual key and device sharing technology, applied in the field of smart devices, can solve problems such as limited number of people, poor security, and inconvenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
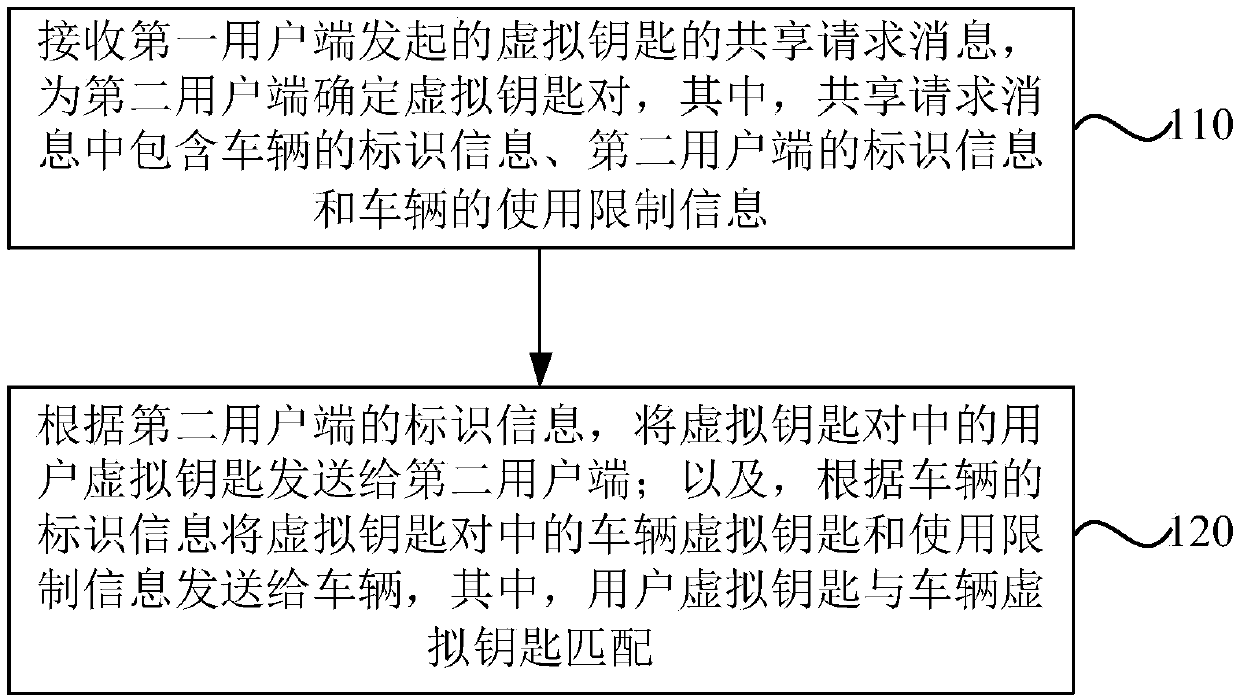
[0059] Figure 1a This is a flowchart of a virtual key sharing method provided in the first embodiment of the present invention. This embodiment is applicable to a situation where a virtual key is used to control a vehicle. The method can be executed by a virtual key sharing device, which can use software and / Or realized by hardware, the device can be configured in a server, such as a computer typically. Such as Figure 1a As shown, the method specifically includes the following steps:
[0060] Step 110: Receive a virtual key sharing request message initiated by the first user end, and determine a virtual key pair for the second user end, where the sharing request message includes the identification information of the vehicle, the identification information of the second user end, and the use restriction of the vehicle information.
[0061] Step 120: Send the user virtual key of the virtual key pair to the second user terminal according to the identification information of the seco...
Embodiment 2
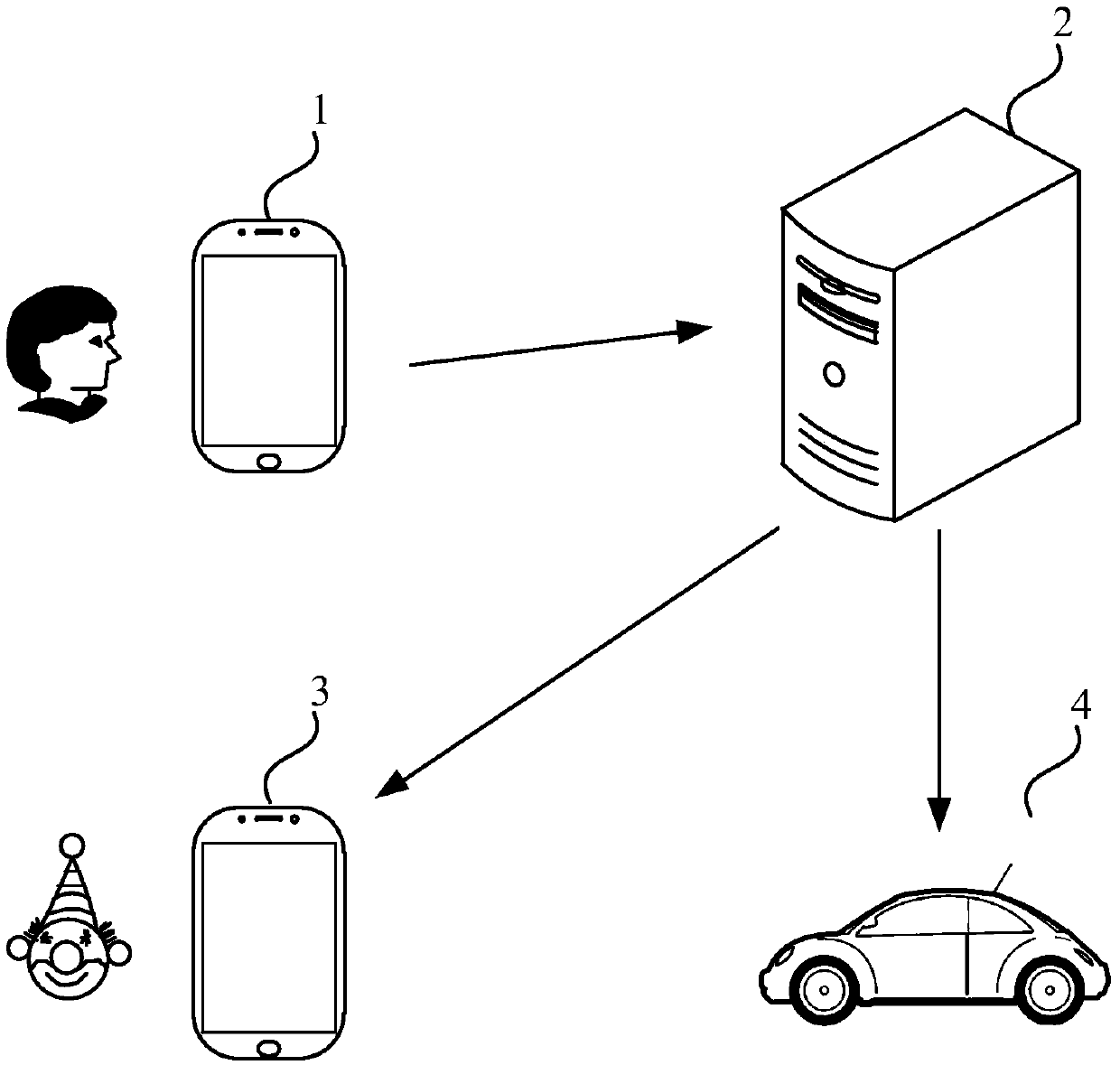
[0089] Figure 2a This is a schematic diagram of an application scenario of a virtual key sharing method provided in the second embodiment of the present invention. The server 2 is connected to the first user terminal 1, the second user terminal 3, and the vehicle 4 (that is, Figure 2b The vehicle control end in the) communicates via the Internet. The first client 1 sends a virtual key sharing request message to the server 2, and the server 2 processes the received sharing request message to establish a correspondence between the second client 3 and the vehicle 4.
[0090] Figure 2b This is a signaling diagram of a virtual key sharing method provided in the second embodiment of the present invention, which can be combined with the signaling diagram Figure 2a The application scenarios shown are understood.
[0091] In the virtual key sharing method provided by the embodiment of the present invention, the first user terminal sends a virtual key sharing request message to the server...
Embodiment 3
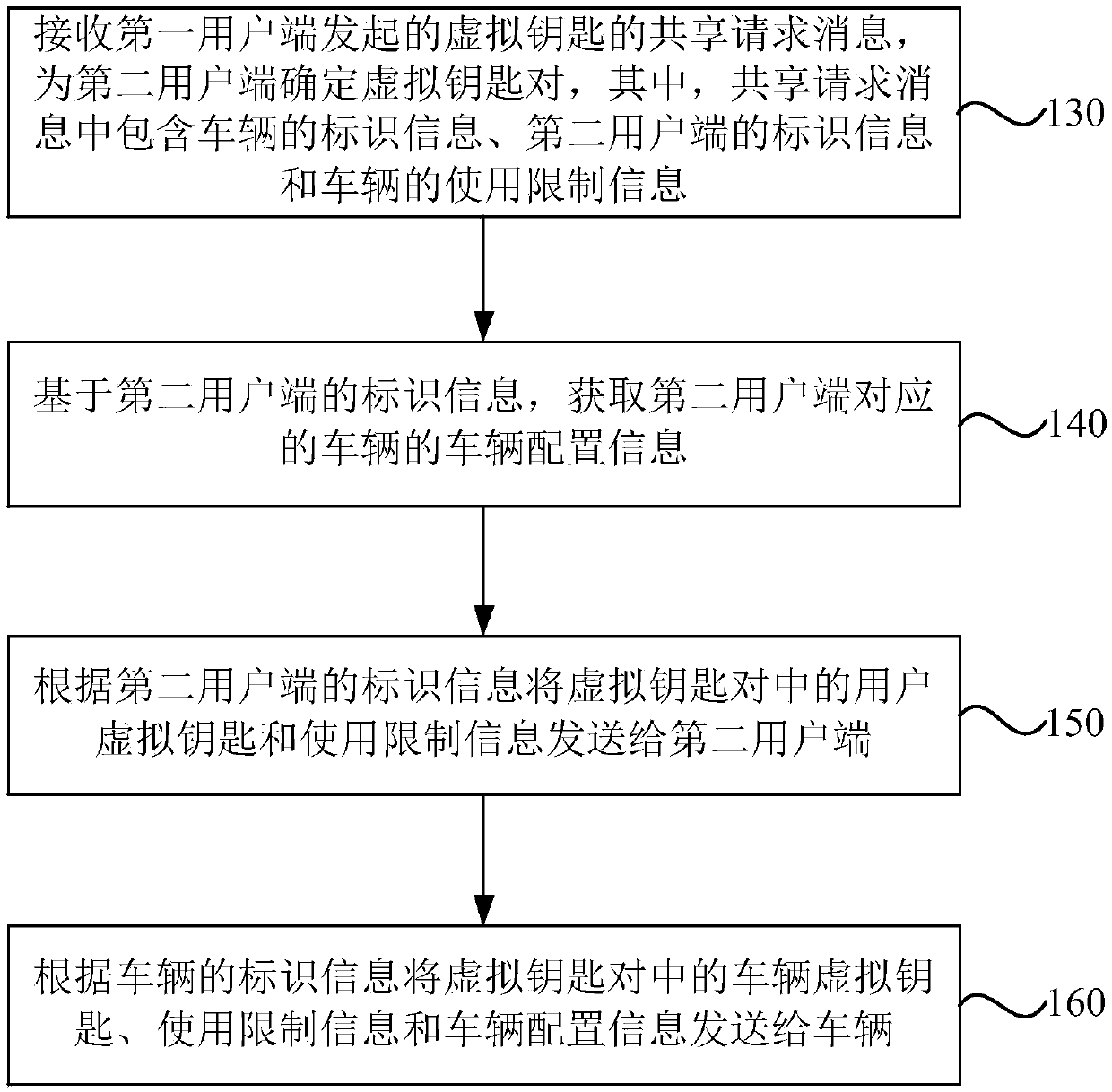
[0094] Figure 3a This is a flowchart of a virtual key sharing method provided in the third embodiment of the present invention. This embodiment is applicable to a situation where a virtual key is used to control a vehicle. The method can be executed by a virtual key sharing device, which can use software and / Or implemented by hardware, the device can be configured in the first user terminal, such as a mobile phone and / or a tablet computer. Such as Figure 3a As shown, the method specifically includes the following steps:
[0095] Step 310: Generate a sharing request message of the virtual key according to the user's operation. The sharing request message includes identification information of the vehicle, identification information of the second user terminal, and use restriction information of the vehicle.
[0096] Step 320: Determine the virtual key pair for the second user terminal according to the sharing request message, and send the user virtual key in the virtual key pair ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com