A Key Backup and Recovery Method Based on Integrated Encryption Technology
A recovery method and encryption algorithm technology, applied in the field of information security, can solve problems such as imperfect key storage methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The specific embodiments of the present invention will be described in detail below with reference to the accompanying drawings. The implementation is carried out on the premise of the technical solution of the present invention, so that those skilled in the relevant fields can better understand the technical characteristics and functional characteristics of the present invention, but the protection scope of the present invention is not limited to the following embodiments.
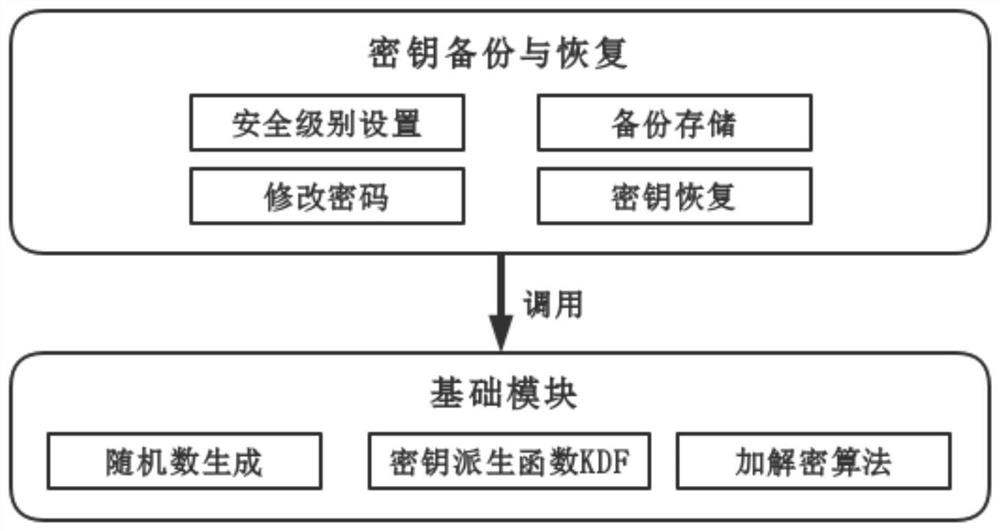
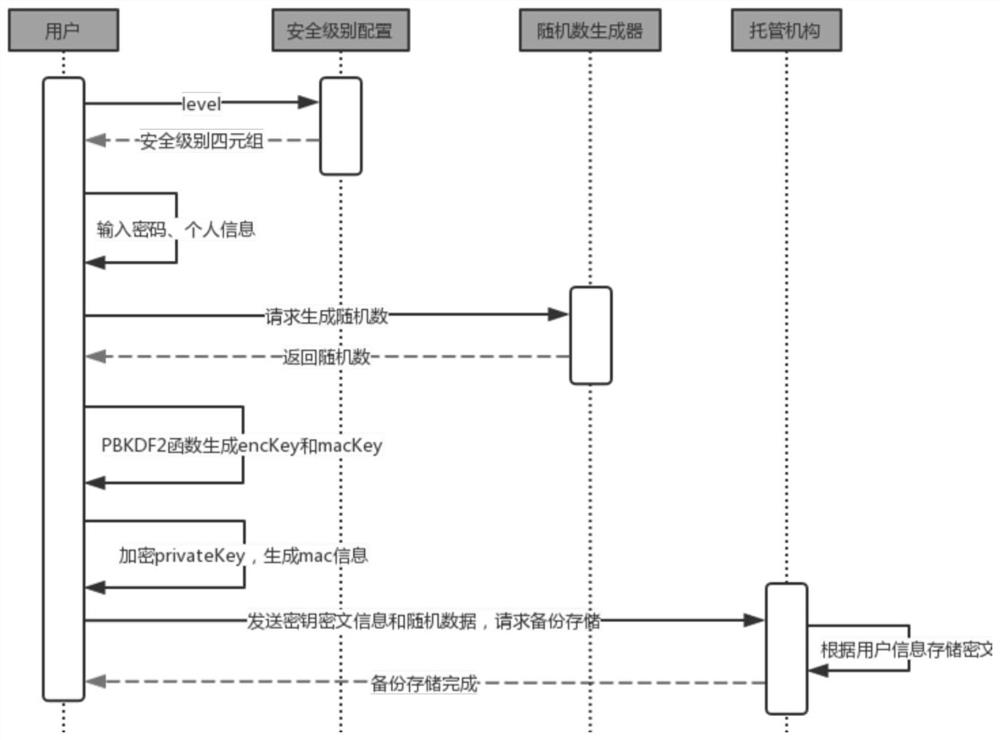
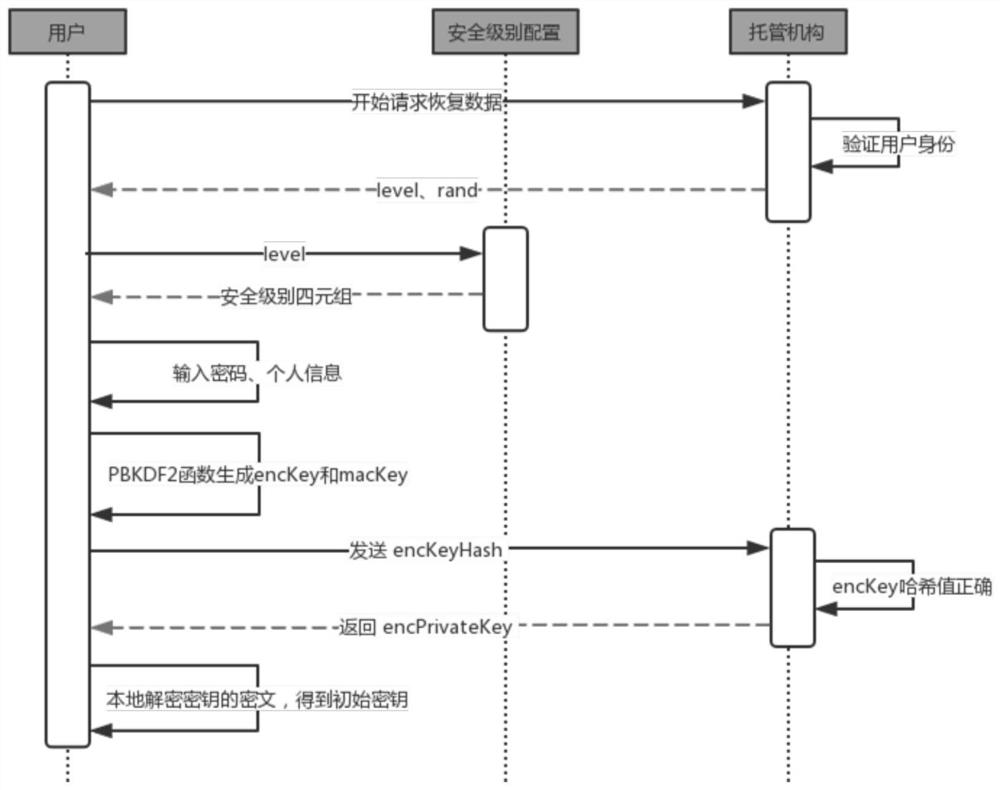
[0034] In this embodiment, the encrypted key is stored in a third-party escrow agency, and the escrow agency provides services for key storage and recovery. The escrow agency provides functions such as user registration, key backup, key recovery and password change.
[0035] First, the custodian institution provides a registration interface. Users register an account in the custodian institution. The account contains an account number and password. With an account, the custodian institution's key b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com